Placing the Security Scanner
As compared to classical intrusion detection systems, the placement of security scanners creates fewer problems. There are a limited number of variants of positioning in such systems. Still, there are lots of factors to take into consideration, especially with respect to network-level security scanners (Internet Scanner, Nessus, etc.), since host-level security scanners create no problems.
First, scanning the same host from different locations of the corporate network might produce different results. Let us consider a typical example: scanning the corporate web server. The first position for placing a security scanner that you will probably think of is the local area network in which the scanned host is located. Most often, security administrators proceed in this manner. The second way to position scanners is to place them in the same network with the scanned host (in the case under consideration, this is the demilitarized zone). The third way is to place the scanner at a remote affiliate. This approach is generally used for scanning remote offices that lack qualified security specialists (Fig. 10.22).
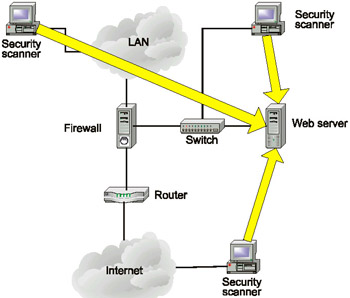
Fig. 10.22. Placement of a security scanner
However, placing the scanner there is potentially dangerous and involves several risks. For example, if there are security tools between the scanning and scanned hosts (such as a firewall or filtering router, or even network-level intrusion detection systems) or network devices, they might prevent the scanner from performing certain checks. This is especially true when the scanning and scanned hosts are located in zones with different security requirements (and note that this is rather common).
The second problem relates to scanning via public networks, since most ISPs lock such attempts. Furthermore, they can even lock all subsequent attempts to connect to the Internet (even to send e-mail). Therefore, when performing remote scanning in such a way, it would be a good idea for you to notify all providers between the scanner and scanned host(s) beforehand.
The second problem is due to VLANs, which, besides offering some advantages (including security advantages), also present some complications for security administrators. This fact was already mentioned in the section dedicated to selecting the right place for IDS network scanners.
Yet another problem might arise if the scanning and scanned hosts are installed in different network segments based on dissimilar architectures (for example, Ethernet and Token Ring). Not all checks available for Ethernet can be implemented in Token Ring. For example, Internet Scanner can not check Token Ring networks for vulnerabilities to some DoS attacks, such as Land, Teardrop, and SYN Flood.
EAN: 2147483647
Pages: 152