Chapter 7: Setting Up a Server
One of the basic choices that you must make before you proceed any further in building your network is to decide which network operating system (NOS) to use as the foundation for your network. This chapter begins with a description of several important features found in all network operating systems. Next, it provides an overview of the advantages and disadvantages of the most popular network operating systems.
Of course, your work doesn't end with the selection of an NOS. You must then install and configure the NOS to get it working. This chapter provides an overview of what's involved with installing and configuring the most popular NOS choice, Windows Server 2003.
Network Operating System Features
All network operating systems must provide certain core functions, such as connecting to other computers on the network, sharing files and other resources, and providing for security. In the following sections, I describe some core NOS features in general terms.
Network support
It goes without saying that a network operating system should support networks. (I can picture Mike Myers in his classic Saturday Night Live role as Linda Richman, host of Coffee Talk, saying "I'm getting a little verklempt … talk amongst yourselves … I'll give you a topic: Network operating systems do not network, nor do they operate. Discuss.")
That requires a range of technical capabilities:
-
A network operating system must support a wide variety of networking protocols to meet the needs of its users.
A large network typically consists of a mixture of various versions of Windows, as well as Macintosh and Linux computers. As a result, the server may need to simultaneously support TCP/IP, NetBIOS, and AppleTalk protocols.
-
Many servers have more than one network interface card installed. In that case, the NOS must be able to support multiple network connections:
-
Ideally, the NOS should be able to balance the network load among its network interfaces.
-
If one of the connections fails, the NOS should be able to seam- lessly switch to another connection.
-
-
Most network operating systems include a built-in capability to function as a router that connects two networks.
The NOS router functions should also include firewall features to keep unauthorized packets from entering the local network.
File-sharing services
One of the most important functions of a network operating system is to share resources with other network users. The most common resource that's shared is the server's file system-organized disk space that a network server must be able to share (in whole or in part) with other users. In effect, those users can treat the server's disk space as an extension of their own computers' disk space.
The NOS allows the system administrator to determine which portions of the server's file system to share.
| Tip | Although an entire hard drive can be shared, it isn't commonly done. Instead, individual directories or folders are shared. The administrator can control which users are allowed to access each shared folder. |
Because file sharing is the reason many network servers exist, network operating systems have more sophisticated disk management features than are found in desktop operating systems. For example, most network operating systems can manage two or more hard drives as though they were a single drive. In addition, most can create a mirror-an automatic backup copy of a drive-on a second drive.
Multitasking
Only one user at a time uses a desktop computer; however, multiple users simultaneously use server computers. As a result, a network operating system must provide support for multiple users who access the server remotely via the network.
At the heart of multiuser support is multitasking-a technique that slices processing time microthin and juggles the pieces lightning fast among running programs. It's how an operating system can execute more than one program (a task or a process) at a time. Multitasking operating systems are like the guy who used to spin plates balanced on sticks on the old Ed Sullivan Show. He'd run from plate to plate, trying to keep them all spinning so that they wouldn't fall off the sticks. To make it challenging, he'd do it blindfolded or riding on a unicycle. Substitute programs for the plates and file management for the unicycle, and there you are.
Although multitasking creates the appearance that two or more programs are executing on the computer at the same time, in reality a computer with a single processor can execute only one program at a time. The operating system switches the CPU from one program to another to create the appearance that several programs are executing simultaneously, but at any given moment, only one of the programs is processing commands. The others are patiently waiting their turns. (However, if the computer has more than one CPU, the CPUs can execute programs simultaneously-but that's another kettle of fish.)
To see multitasking in operation on a Windows Server 2003 computer, press Ctrl+Alt+Delete to bring up the Windows Task Manager and then click the Processes tab. This displays all tasks that are active on the computer, as shown in Figure 7-1.
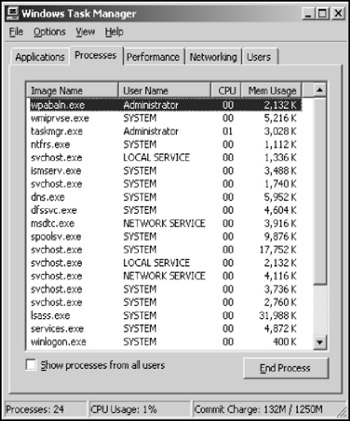
Figure 7-1: Displaying active tasks on a Windows Server 2003 computer.
Directory services
Directories are everywhere-and were, even in the days when they were all hard copy. When you needed to make a phone call, you looked up the number in a phone directory. When you needed to find the address of a client, you looked her up in your Rolodex. And then there were the nonbook versions: When you needed to find the Sam Goody store at a shopping mall (for example), you looked for the mall directory-usually, a lighted sign showing what was where.
Networks have directories, too, providing information about the resources that are available on the network-such as users, computers, printers, shared folders, and files. Directories are an essential part of any network operating system.
In early network operating systems (such as Windows NT 3.1 and NetWare 3. x), each server computer maintained its own directory database-a file that contained an organized list of the resources available just on that server. The problem with that approach was that network administrators had to maintain each directory database separately. That wasn't too bad for networks with just a few servers, but maintaining the directory on a network with dozens or even hundreds of servers was next to impossible.
In addition, early directory services (programs that made the directory databases usable) were application specific. For example, a server had one directory database for user logons, another for file sharing, and yet another for e-mail addresses. Each directory had its own tools for adding, updating, and deleting directory entries.
The most popular modern directory service is Active Directory, which is standard with Windows-based server operating systems. Active Directory provides a single directory of all network resources. It drops the old-style 15-character domain and computer names that were used by Windows NT Server in favor of Internet-style DNS-style names, such as http://www.Marketing.MyCompany.com or http://www.Sales.YourCompany.com. Figure 7-2 shows the Active Directory Users and Computers tool, which is used to manage Active Directory user and computer accounts on Windows Server 2003.
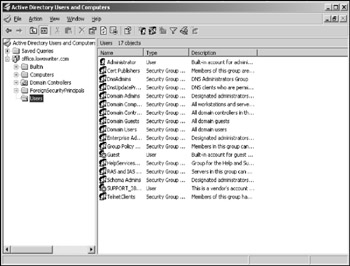
Figure 7-2: Active Directory Users and Computers.
Security services
All network operating systems must provide some measure of security to protect the network from unauthorized access. Hacking seems to be the national pastime these days. With most computer networks connected to the Internet, anyone anywhere in the world can-and probably will-try to break into your network.
The most basic type of security is handled through user accounts, which grant individual users the right to access the network resources and govern which resources the user can access. User accounts are secured by passwords; therefore, good password policy is a cornerstone of any security system. Most network operating systems give you some standard tools for maintaining network security:
-
Establish password policies, such as requiring that passwords have a minimum length and include a mix of letters and numerals.
-
Set passwords to expire after a certain number of days. Doing so forces network users to change their passwords frequently.
-
Encrypt network data. A data-encryption capability scrambles data before it's sent over the network or saved on disk, making unauthorized use a lot more difficult.
Tip Good encryption is the key to setting up a virtual private network, or VPN, which enables network users to securely access a network from a remote location by using an Internet connection.
-
Issue digital certificates. These special codes are used to ensure that users are who they say they are and files are what they claim to be.