Hack 28 Encrypt Your Temp Folder
Keep prying eyes out of your temporary files. Many Windows applications will create intermediary files while they do their work. They typically store these files in a temporary folder within the current user's settings directory. Most often these files are created world-readable and aren't always cleaned up when the program exits. How would you like it if your word processor left a copy of the last document you were working on for anyone to come across and read? Not a pretty thought, is it? One way to guard against this situation is to encrypt your temporary files folder. To do this, open an Explorer window and go to the C:\Documents and Settings\<username>\Local Settings folder. In this folder you should see another folder called Temp. This is the folder that holds the temporary files. Right-click the folder and bring up its Properties dialog. Make sure the General tab is selected, and click the button labeled Advanced. This will bring up an Advanced Attributes dialog, as seen in Figure 2-6. Here you can choose to encrypt the folder. Figure 2-6. The Temp folder's Advanced Attributes dialog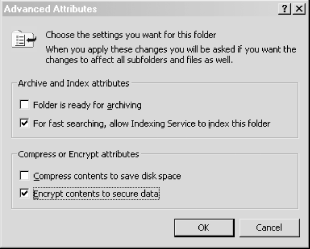 Check the "Encrypt contents to secure data" box and click the OK button. When you have done that, click the Apply button in the Properties dialog. Another dialog (as seen in Figure 2-7) will open asking you whether you would like the encryption to apply recursively. Figure 2-7. Confirm the choice of encryption and make it recursive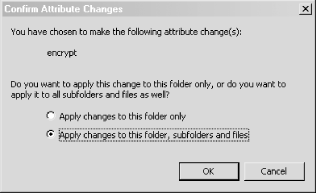 To apply the encryption recursively, choose the "Apply changes to this folder, subfolders and files" option. This will automatically create a public-key pair if you have never encrypted any files before. Otherwise, Windows will use the public key that it generated for you previously. When decrypting, Windows ensures that the private keys are stored in nonpaged kernel memory, so that the decryption key will never be left in the paging file. Unfortunately, the encryption algorithm used, DESX, is barely an improvement on DES and is nowhere near as strong as 3DES. However, it serves the purpose of transparently encrypting temporary files very well. If you want to encrypt other files, it is suggested you use a third-party utility such as GnuPG (http://www.gnupg.org), which has Windows binaries available on its web site. |
EAN: 2147483647
Pages: 158
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XII Web Design and E-Commerce
- Chapter XV Customer Trust in Online Commerce