Упражнение 3
1:
, . . , , . , , , ,' . . .
, - , , . , , - . , .
, , , , . .
, , , - , , ( ).
, , , . , , , , . , , — , .
:
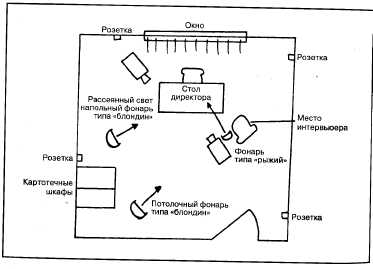
, . . , , . , , , ,' . . .
, - , , . , , - . , .
, , , , . .
, , , - , , ( ).
, , , . , , , , . , , — , .
| · | , ( ) ? |
| · | , ? |
| · | , ? ' |
:
