Низкие держатели
. , , . — , , , , , , , , . .
. , . , , . , , , , .
, . , , . . , , , , ( ) 15, 15 .
, , . , . ' , ( ) , .
( ), , , ( , ) . .
, .
, , . , - .
. , , , . . , - .
. 7.1 , . , .
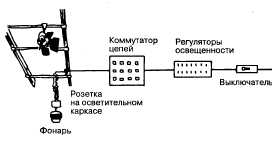

. 7.1. , , .
, , , , . , , .
, , - . .
, , . .
, , . -
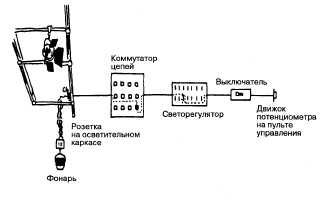
. 7.2, . .
( . 7.2, ). . . . . 7.2, , , 12 4 12.
, , . , , , . 2 10 . , , .
100%- ,
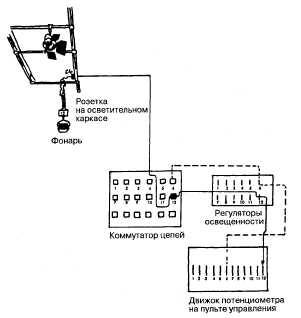
. 7.2, . , 4 6 , 12 12 6.
5 , 23 , 2 . , , 5 10 , ( ) .