10.3 Types of Firewalls
| Firewall is really a generic term that covers many different types of devices used to separate network traffic. Most firewalls are simply a server, with a hardened operating system, and a software-based firewall providing the protection. Some firewalls, known as embedded firewalls, have the operating system and firewall programmed directly onto the system CPU. Three types of firewalls will be covered in this section:
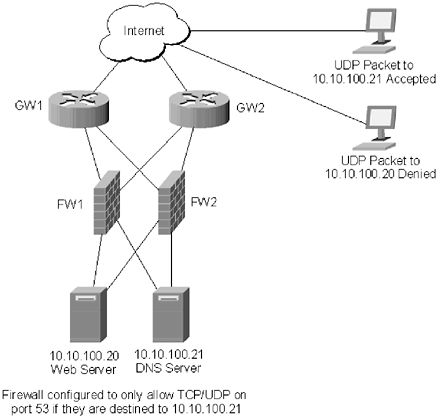
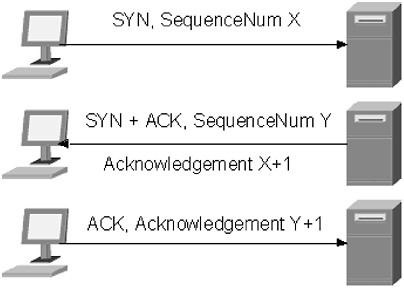
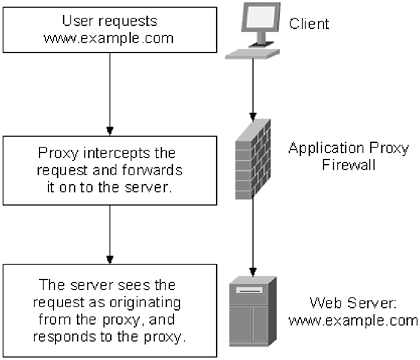
The most basic type is the packet filtering firewall. A packet filtering firewall sits between the public and the private network, as shown in Figure 10.1. All network traffic, both ingress and egress, has to pass through the firewall. The firewall determines what happens to packets based on one of four criteria: source IP address, destination IP address, source port, and destination port. The four criteria can be combined in the firewall rule set to determine what type of traffic will be allowed through. For example, if an organization maintains a primary DNS server on the private network, UDP and TCP traffic destined for Port 53 has to be allowed for that server, but it should not be allowed to any other device on the network. This is shown in Figure 10.3. Packets destined for the DNS server are allowed, while the same packets destined for the web server are denied . Figure 10.3. Packet filter firewalls can be configured to allow/deny traffic based on source or destination IP address, as well as source and destination port Generally, destination IP address and destination port are the criteria used by administrators to filter. Unless all external traffic is being denied by the firewall ”such as on the private side of a DMZ ”firewall administrators have the most control over these two criteria. Most of the time when a hole is opened through the firewall, it is to grant access to a public server. DNS, web, and mail servers are the most common examples of public servers. Because these servers are public, any IP address may connect to them. Rather than try to filter a source IP address, or addresses, it is easier to deny all traffic unless it is destined to the IP address of a server running the public service. The same process applies to the source port. When an HTTP, DNS, or SMTP request is made, the source port is usually one of the higher, unreserved ports. The destination should always be the same, Port 80 for HTTP, Port 53 for DNS, and Port 25 for SMTP. An administrator cannot filter out the higher ports, so it makes more sense to deny based on the destination port. This type of strategy makes configuring the firewall a lot easier, and it makes the rule set simpler. For most firewalls, this is the default policy: Deny all services, except for those explicitly allowed. Stateful packet filters offer the same features as packet filtering firewalls, with some expended functionality. A stateful packet filtering firewall keeps track of session information between two devices. Specifically, the stateful packet filter tracks the current session state of all transactions. As shown in Figure 10.4, all TCP sessions initiate with a three-way handshake. The device initiating the connection sends a request with a sequence number. This is known as a SYN request. The device on the other end of the connection responds with a SYN/ACK. It acknowledges the request, increases the value of the initial sequence number by one, and sends its own sequence number (independent of the original sequence number). The device that originally initiated the session responds to the SYN/ACK with an ACK. The ACK contains the sequence number of the remote device, incremented by one. Figure 10.4. A TCP session initiates with a three-way handshake Attackers will often attempt to trick servers, and other machines, by sending packets that have the incorrect bit set. This is especially common when port scanning: An attacker attempts to see what ports are open on a server by sending packets that have the ACK bit set, tricking the server into thinking that it is an open session. A stateful packet filtering firewall maintains a state table. The state table is simply a database that tracks current connections, and what state they are in. If the firewall receives a packet in an unexpected state, the packet is dropped. Another common ploy used to bypass a regular packet filtering firewall is to forge a response packet to a machine behind the firewall. Even though the machine did not initiate the request, the firewall will allow it through, giving an attacker access to the internal network. A stateful packet filtering firewall does not understand the application that the two devices are using to communicate; it only understands the packet structure, so it won't filter based on any information other than packet structure. This can still leave a network vulnerable to some types of attacks. The third type of firewall, the application proxy, sits between the client and the server and responds to all requests. This is different from a packet filtering firewall, which simply forwards requests between the two devices, in the same manner that a router would. An application proxy firewall responds to all requests, as if it were the device to which the request is made. For example, if a proxy firewall was placed, logically, in front of a web server, as in Figure 10.5, a client would make a request to the web server. The proxy firewall would intercept the request, and then make the request of the web server on behalf of the client. The web server responds to the proxy firewall, which then forwards the request to the client. Figure 10.5. A proxy firewall intercepts incoming requests, examines the packet, and forwards those requests onto their intended destination. If there is a problem with the incoming packet, it is dropped. As you can imagine, application proxy firewalls are very powerful, and are able to probe much deeper into a packet than packet filtering firewalls can. Application proxy firewalls can do pattern matching within the packet, looking for matches that might indicate an attack is in progress. If a match is spotted, the packet is dropped, and the server never knows there was a problem. This power comes with a steep price; application proxy firewalls require a lot of CPU resources and, especially on busy networks, they can often be ineffective in dealing with a large amount of traffic. Some security experts argue that application proxy firewalls don't always live up to their potential ”and don't stop as many attacks as they could. Again, the problem arises that many security administrators who use application proxy firewalls feel that they have a complete security solution and do not take steps to secure the rest of the network. Determining the type of firewall that best suits a network depends largely on the experience of the staff that will be administering the firewall, and other security precautions that are available within the network. Many firewalls can run in all three modes, giving administrators a wide range of options when selecting the firewall that best meets the needs of the network. |
EAN: 2147483647
Pages: 131