5.6 ARP Tables
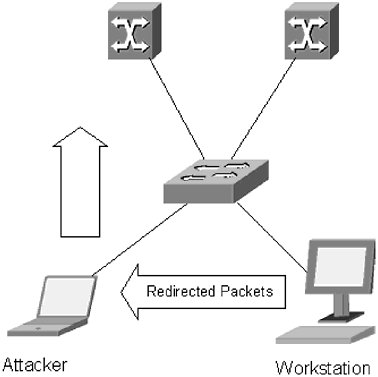
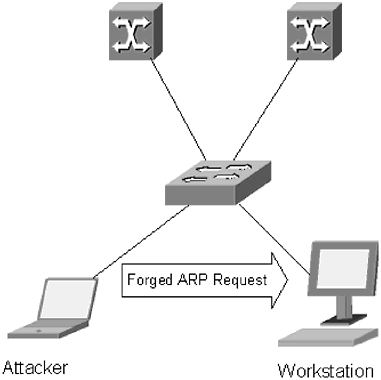
| Similar to routers, switches maintain ARP tables that map a logical address, such as an IP address, to a physical address, usually a MAC address. In a switched environment the ARP table is normally very static. The MAC address of a network card does not normally change, and the IP address associated with a machine will also remain relatively constant. Unfortunately, most switches are susceptible to ARP attacks which can render a switch unusable, or be used to gather information about the topology of a network. In November 2001, Cisco released a security warning about ARP table vulnerabilities in most versions of its IOS software. An ARP request received by a router interface, but with a different MAC address for that interface, would normally be ignored. However, if multiple ARPs were received with the different MAC address, the interface would first attempt to maintain its existing MAC address, but would eventually give up and overwrite its MAC address with the one listed in the ARP. This would effectively shut down the router or the administrative interface of the switch. This weakness was patched, and new versions of the software were released for all current code trees. This incident highlights some of the security issues associated with ARP tables which can be flooded to force a switch to broadcast traffic; they can also be poisoned with bad information, allowing an attacker to intercept packets. The basic problem with ARP tables is that they are generated dynamically, which is good and bad. This dynamic generation is what makes ARP tables so useful for generating traffic on the network, and it allows an administrator to use other dynamic protocols, like DHCP, on the network. On the downside, these same ARP tables can be used to disrupt the network, unless they are properly secured. Another trick attackers sometimes use to gain access to information is called ARP poisoning . An attacker who wants to monitor traffic for another workstation on the network will send that workstation a forged ARP packet. The workstation will receive the ARP packet and direct traffic to the attacker's network device. The attacker intercepts the packet, gathers the necessary information, and passes it on to its original destination. To get a better idea of how this works, take a look at Figures 5.7 and 5.8. Figure 5.7. Packets destined for the gateway are redirected to the attacker's machine, inspected, and forwarded to the gateway Figure 5.8. An attacker sends a forged ARP request In Figure 5.7, the attacker sends a forged request to the workstation, representing her machine as the gateway address. The workstation now sends all gateway requests to the attacker's machine. The attacker inspects the packets, and then forwards them on to the real gateway, as in Figure 5.8. The workstation does not realize that its packets are being intercepted and continues to forward traffic to the attacker for as long as the attacker remains connected to the network. One way to avoid this is to manually map MAC addresses to an IP address. Because the primary function of the ARP table is to map a logical address to a physical address, if that information is manually entered into the switch configuration, it cannot be overwritten. On a Cisco switch, you can perform this task by typing: Core1(config)# arp 10.10.0.29 xx.xx.xx.xx.xx.xx arpa 0/12 This command would map the IP address 10.10.0.29 with MAC address xx.xx.xx.xx.xx.xx to port 0/12 on a switch. The arpa entry indicates the type of traffic; this is the default for IP networks. Extreme, Foundry, and most other managed switches will give you the ability to do this. Check with your vendor for details as to how it is done. The problem with hard coding MAC addresses, as this is sometimes called, is that it forces administrators to assign static IP addresses to every device on the network. This can open other security holes. Notably, it makes it easier for an attacker to map out network topology. Hard coding MAC addresses is a good practice for switches that have network devices with static IP addresses, such as the core switches, or the server access switches. This practice generally does not make a lot of sense for areas where IP addresses are dynamically assigned. |
EAN: 2147483647
Pages: 131