5.1 The Switch on the Network
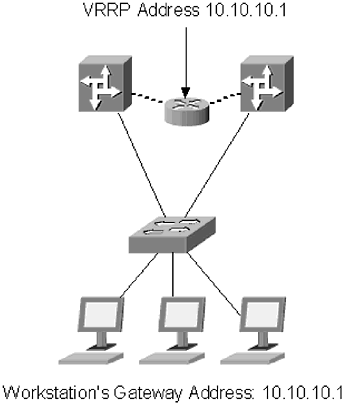
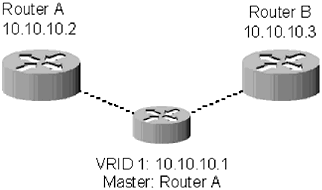
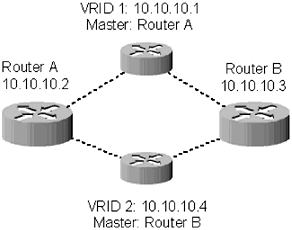
| Switches make up the core of an enterprise network. Depending on the type of switch it can be used to route traffic between internal networks, and out to the Internet. There are two types of switches that should be used in your network: (1) managed Layer 2 switches and (2) multilayer switches ”which will be discussed in greater detail in the next section. Traditional Layer 2 switches, also called workgroup switches, are fairly static and reliable. They are the networking devices closest to workstations and servers, and they simply act as forwarders to send TCP or UDP requests to their ultimate destinations. Depending on how employees are spread throughout the building, a typical 100- user network will have four or five workgroup switches plugged into two core switches, which will make routing decisions. Figure 5.1 shows a typical network layout using a combination of workgroup and core switches. The workstations are all assigned a gateway of 10.10.10.1; they connect to the workgroup switch, which has two connections, one to each of the core switches. The core switches have configured a VRRP address of 10.10.10.1. Traffic flows to the core switch that is active for the address 10.10.10.1 and on to its destination. Figure 5.1. A typical network design using Workgroup 2 switches in conjunction with multilayer switches Should something happen to the primary core switch, the second one would take over and start answering queries for the address 10.10.10.1. 5.1.1 Redundancy ProtocolsBefore continuing the discussion of the core network, it is a good idea to discuss redundancy protocols. VRRP, defined in RFC 2338, is a way to increase availability by allowing two devices to share an IP address. VRRP is based on the Cisco proprietary protocol Hot Spare Router Protocol (HSRP) and the Digital Equipment Corporation proprietary protocol IP Standby Protocol (IPSTP), although many other networking companies also have their own proprietary redundancy protocols. VRRP is an excellent way to increase availability within a network while still maintaining security. Prior to VRRP, the only way to provide redundancy within a network was to use dynamic routing protocols, such as OSPF or RIP. Obviously, trying to manage a large network with every node belonging to an OSPF or RIP area would be a logistical and security nightmare. VRRP allows a network administrator to configure static routes on workstations and servers, only relying on dynamic routing to move traffic through the network core. Configuration of VRRP is surprisingly simple. A virtual router is configured between two or more interfaces that are part of the same subnet. Each virtual router is assigned a virtual router ID (VRID), so an interface can be part of multiple virtual routers. One of the interfaces participating in a virtual router is declared the master; the rest are backups . Figure 5.2 outlines a typical VRRP network design. Router A and Router B are both part of 10.10.10.0/24 netblock. They are also both participating in VRRP for 10.10.10.1. The master, in this case Router A , can be automatically determined, or an administrator can assign a priority between 1 and 255 to each interface during the configuration process. The virtual router responds to all ARP requests with a special MAC address designated for VRRP. The address is 00-00-5E-00-01-[VRID]. Using a special MAC address means that the routers will not have to wait for the ARP cache of the switches to expire before the new device takes over. When the backup device begins responding to requests, it responds using the same MAC address, so the flow of data does not need to be interrupted . Figure 5.2. A typical VRRP configuration The master router sends multicast packets every second announcing that it is alive . If the backup devices do not receive this multicast packet, they will begin the negotiation process to determine which device should become the new master. The new master will remain the master until the older master returns to service ( assuming it is configured with a higher priority). Where VRRP falls short is that it is not a load-balancing protocol. While the master router is responding to queries, the backup router is not doing anything. From a cost perspective it is hard to justify a $10,000, $20,000, or more expensive device that sits on the network and does not pass any traffic unless there is a problem. Many administrators have overcome this limitation by creating multiple VRIDs that are shared by the same interfaces. Some workstations will use the first VRID as their gateway, while others will use the second VRID as theirs. Figure 5.3 demonstrates configuring two virtual routers. Each router has a different VRID, even though both are served by the same set of routers. Assuming the DHCP server on the network is configured to return the two gateways, traffic will be load balanced between the two devices, so resources are not wasted . Figure 5.3. A VRRP configuration with two virtual routers VRRP is a great protocol when creating a redundant gateway within a network that is not homogenous. On the other hand, if you are using the same devices throughout your network, you probably want to consult your vendor's documentation about the enhancements they have made to VRRP. NOTE These enhancements are sometimes called *SRP. You already know Cisco has the HSRP, but Extreme Networks has the Extreme Standby Router Protocol (ESRP), and Foundry Networks has the Foundry Standby Router Protocol (FSRP). 5.1.1.1 Redundancy SecurityVRRP provides for several levels of security within the protocol. At its most basic level, there is no authentication of VRRP packets. Of course, this is unacceptable, so the developers of the VRRP standard have included several levels of packet authentication. In addition to packet authentication, interfaces will ignore VRRP packets that originate from other networks. This means that VRRP should not be susceptible to remote attacks. Unfortunately, VRRP is still susceptible to local attacks. Similar to the dynamic protocols discussed in Chapter 4, VRRP allows administrators to force either clear text password or MD5 header authentication. If you choose to use clear text authentication on your network, understand that the password will be broadcast from the master router every second. Since the password is clear text, anyone who has gained entry to your network may be able to sniff it. While passwords may make life more difficult for an attacker, it will be only marginally more difficult. MD5 header authentication provides significantly more security. Unfortunately, network devices are not required to support MD5 header authentication to be considered VRRP compliant. Check with your vendor to ensure that they will support this type of authentication. |
EAN: 2147483647
Pages: 131