1.5 The Network
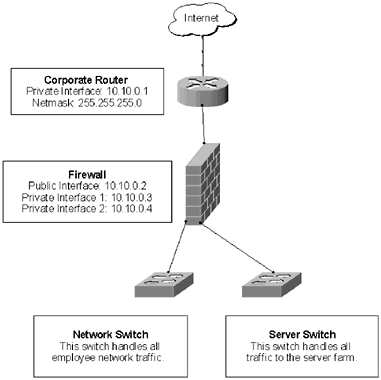
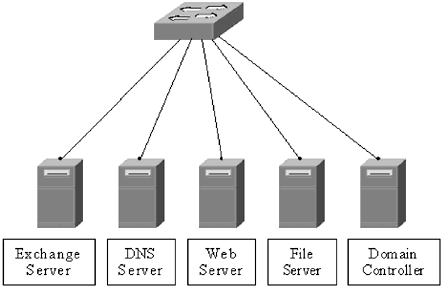
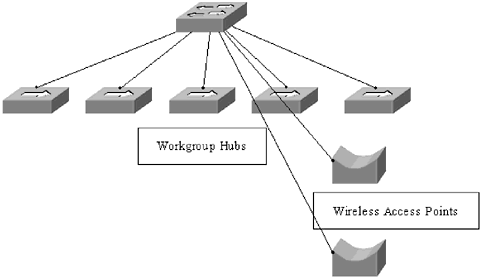
| The best way to learn is by example; to that end this section presents a typical corporate network for a 100-person company. This network is fairly insecure . Forging ahead, various chapters in the book will capitalize on the vulnerabilities in the network and demonstrate ways to correct them. Of course, there is no one correct security model. Security needs vary from company to company, but showing how to spot and correct weaknesses in corporate security helps administrators find holes in their own networks, and helps create better methods for dealing with security issues. NOTE In this example, the netblock 10.10.0.0 255.255.255.0 is used. This is one of the netblocks that has been reserved by RFC 1918 for private use. Think of it like using the 555 prefix for phone numbers in movies. The address block will function like a normal netblock, but the addresses are not routable across the wide area network (WAN). 1.5.1 The Network InfrastructureFigure 1.1 shows the network infrastructure for this company. It is fairly simple: a router connected to a firewall that has three interfaces: public ”to the router, and two private interfaces ”one to the employee network and one to the server farm. Figure 1.1. The network infrastructure The firewall rule set is also fairly simple for this network. No traffic is allowed in to the employee network, all traffic is allowed in to the server network. The rules for the server network were tighter, but as new software was added to the servers in the server farm, it became difficult to keep track of which ports needed to be opened so all ports were opened. The company uses a TCP/IP network infrastructure, but no auditing has been done to see what other network protocols are running on the machines. The netblock 10.10.10.0 255.255.255.0 (a Class C block of addresses) is assigned to the company. The IP addresses have been distributed throughout the network without subnetting them. Finally, even though they are using managed switches, the network administrators have not assigned different VLANS to the ports on their switches; all machines connected to the switches are using the default VLAN. 1.5.2 The Server FarmThe server farm (Figure 1.2) consists of five servers; all but two perform unique functions. The File server also doubles as a Remote Access Service (RAS) server that allows employees to dial in to the network from home, while the domain controller doubles as a monitoring server. Figure 1.2. The server farm The file and exchange servers and the domain controller are all running Windows NT, with service pack 4 installed. The web and DNS servers are both running Red Hat Linux 6.2. New accounts are created on an as-needed basis, and there has been no auditing of account information to date. 1.5.3 The Employee NetworkVarious employee groups, such as human resources and accounting, are connected via hubs to the network switch (Figure 1.3). The employees use a mix of Windows 98, Windows NT Workstation, and Windows 2000 Professional workstations. Again, there has been no workstation auditing to date, and no one has set a policy to limit the type of workstations that can be added to the network. There is also no password auditing or policing system in place. Figure 1.3. The employee network All workstations on the network are assigned IP addresses by the domain controller when they log onto the network. The company is also experimenting with WLAN technology. The two conference rooms have been outfitted with access points that allow anyone with an 802.11b-enabled card or computer to connect into the network. There are many gaping security flaws within this network. As each area is delved into more deeply, they should become more apparent. |
EAN: 2147483647
Pages: 131