18.5 E-Mail Forgery and Tracking
18.5 E-Mail Forgery and Tracking
It is often possible to track e-mail back to its source and potentially identify the sender using the information in e-mail headers. In addition to learning how to extract information from e-mail headers, it is important to understand how e-mails can be forged. The main use of forged e-mail is to give the receiver a false impression. For example, the sender might pose as the recipient's boss or friend. Some offenders forge e-mail in an effort to conceal their identity. However, this approach to anonymity is ineffective because forgeries usually contain the sender's IP address.
Before delving into e-mail forging and tracking, it is necessary to understand how a message is created and transmitted. Electronic mail is similar to regular mail in many ways. There are computers on the Internet, called Message Transfer Agents (MTA) (Figure 18.4), which are the equivalent of post offices for electronic mail. When an e-mail message is sent, it first goes to a local MTA. Just as a post office stamps letters with a postmark, the local MTA puts the current time and the name of the MTA along with some technical information, at the top of the e-mail message. This e-mail equivalent of a postmark is called a "Received" header. The message is then passed from one MTA to another until it reaches its destination.
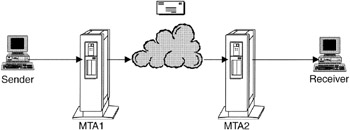
Figure 18.4: Message, Transfer Agent.
Every MTA that receives the message puts a received header at the top of the message. A simple analogy to this is a stack of pancakes; newer ones are on top. This means that the last computer to handle the message is listed at the top of the header, and the first computer is listed near the bottom. Therefore, to track an e-mail message back to the sender, simply retrace the route that the e-mail traveled by reading through the e-mail's Received headers.
One approach to preserving a complete copy of an e-mail message, including headers, is to save it to file and calculate the MD5 value of the file. Notably, printing an e-mail message will not usually show the header information unless it is displayed. Most e-mail applications can display e-mail headers. For example, while viewing an e-mail message in Netscape Mail select the View - Headers - All menu item or Options - Show Headers on older vesions, in Outlook Express select the File - Properties menu item and click on the Details tab, in Outlook select the View - Options menu item, in Eudora click on the "Blah, Blah, Blah" button at the top of the message, and in Pine type H.
E-mail forgery takes advantage of how MTAs exchange messages using Simple Mail Transport Protocol (SMTP). Remember that a protocol is just an agreed upon way of "speaking" and, as the name suggests, the Simple Mail Transfer Protocol is quite simple. In four broken English sentences (helo, mail from, rcpt to, data) one MTA (mta.sending.com) can instruct another MTA (mta.receiving.com) to pass an e-mail message on to its destination. Using the same broken sentences, an individual can command an MTA directly using Telnet on a Windows machine by clicking on the Start button, selecting Run, typing "telnet mta.sending.com 25". This instructs Telnet to connect to port 25 on the MTA and permit SMTP commands to be typed and sent to the MTA as shown here:
% telnet 192.168.201.11 25 Trying 192.168.201.11... Connected to 192.168.201.11. Escape character is '^]'. 220 mta.sending.com ESMTP Sendmail 8.11.6/8.11.6; Sat, 10 May 2003 14:58:57 -0500 helo forgery.com 250 mta.sending.com Hello forgery.com, pleased to meet you mail from: forger@forgery.com 250 2.1.0 forger@forgery.com... Sender ok rcpt to: louiscipher2004@hotmail.com 250 2.1.5 louiscipher2004@hotmail.com... Recipient ok data 354 Enter mail, end with "." on a line by itself Received: from fake.com ([10.12.227.15]) by mta.nonexistent.com (MSMTP 4.04) with SMTP id g5BK2m642810 for jane.doe@corpX.com; Sat, 10 May 2003 16:00:00 -0500 From: Joe Smith <joe.smith@corpX.com> To: Jane Doe <jane.doe@corpX.com Date: Sat, 10 May 2003 15:12:16-0400 Message-ID: <069601c31728$122ee620$9eef7222@jxsdqfofq> I am corning to get you. Joe .
In the SMTP session shown above, the helo command introduces the sending host. The "mail from:" command specifies where bounces and receipts will be delivered, regardless of what the "From" line contains. The "rcpt to:" command specifies where the e-mail message will be delivered, regardless of what the "To" line contains. The data command begins the message and fake headers can be entered here. The body of the message should be separated from any headers by at least one blank line. The body of the message is terminated by a single "." on a line by itself, resulting in the following message.
Received: from mta.sending.com ([192.168.201.11])
by mc1-f7.law16.hotmail.com with Microsoft SMTPSVC(5.0.2195.5600); Sat, 10 May 2003 13:02:26 -0700
Received: from forgery.com ([172.16.237.235])
by mta.sending.com (8.11.6/8.11.6) with SMTP id h4AK1|531700 for louiscipher2004@hotmail.com; Sat, 10 May 2003 15:01:53 -0500
Received: from fake.com ([10.12.227.15])
by mta.nonexistent.com (MSMTP 4.04) with SMTP id g5BK2m642810 for jane.doe@corpX.com; Sat, 10 May 2003 16:00:00 -0500
From: Joe Smith <joe.smith@corpX.com>
To: Jane Doe <jane.doe@corpX.com>
Date: Sat, 10 May 2003 15:12:16 -0400
Message-ID: <069601c31728$122ee620$9eef7222@jxsdqfofq>
Return-Path: forger@forgery.com
I am coming to get you.
Joe
The alert examiner will see that the forged Received header is not consistent with the other headers. First, the date-time stamp in the forged header is 1 hour later than the other date-time stamps in the message. Second, the forged header indicates that the message was accepted by "mta.nonexistent.com" in which case the next Received header should show the message being passed from "mta.nonexistent.com" to "mta.sending.com." However the next header contains no reference to "mta.nonexistent.com" and instead reveals the sender's actual IP address (172.16.237.235). The ISP responsible for the sender's IP address could use this information to determine which user account was used to send the message. To hide their IP address, some e-mail forgers send messages by connecting to an SMTP relay via a proxy as shown here:
% telnet proxy.isp.com 3128 Trying proxy.isp.com... Connected to proxy.isp.com. Escape character is '^]'. CONNECT smtp.relay.com:25 HTTP/1.0 [hit return twice] Host: smtp.relay.com:25 HTTP/1.0 200 Connection established HELO [YOUR DOMAIN] MAIL FROM: [YOUR EMAIL ADDRESS] RCPT TO: [YOUR EMAIL ADDRESS] DATA Testing for an open squid proxy .
This approach makes it even more difficult to determine the originating IP address because the Web proxy effectively conceals this information. Although some Web proxies add a "X-Forwarded-For" header containing the sender's IP address, this information is not retained in an e-mail header.
18.5.1 Interpreting E-Mail Headers
Unless a re-mailer or advanced forging technique has been used, a key piece of information that can lead to the sender's identity will be stored somewhere in the message. The trick is to find that key piece of information among the mass of misleading information. For e-mail tracking purposes, the two most useful e-mail headers are the "Message ID" and "Received" headers. A Message-ID is required to be globally unique - no two different messages will ever have the same Message-ID. Some MTAs construct the Message-ID using the current date and time, the MTA's domain name, and the sender's account name. For instance, a message sent on December 4, 1999 from mail.corpX.com by user13 might have the following Message-ID header:
Message-Id: <user13120499152415-00000153@mail.corpX.com>
The Message-ID cannot always be relied on since it can be forged as shown in the previous section. Although forged Received headers can be inserted into a message to confuse investigators, some of the headers at the top of the message must be valid because they were added by MTAs that delivered the message.
In some cases, a Received header will contain the sender's e-mail address. In other cases, a Received header will contain the IP address of the originating computer and it may be necessary to contact someone at the ISP responsible for the IP address to find out who was using the computer in question at the time the message was sent. For instance, many individuals attain "pseodonymity" by using non-identifying e-mail addresses (e.g. Hotmail, Netaddress) but they are unaware that the e-mail headers of these messages contain the IP address of the originating computer. For instance, the following Hotmail message contains the originating IP address in two places.
Return-Path: <louiscipher2004@hotmail.com>
Received: from hotmail.com (f14.pav1.hotmail.com [64.4.31.14])
by mta.receiving.com (8.9.3/8.9.3) with ESMTP id UAA06245 for <john.doe@receiving.com>; Wed, 28 Aug 2002 20:42:17 -0500
Received: from mail pickup service by hotmail.com with Microsoft SMTPSVC;
Wed, 28 Aug 2002 18:42:08 -0700
Received: from 192.168.12.48 by pv1fd.pav1.hotmail.msn.com with HTTP;
Thu, 29 Aug 2002 01:42:08 GMT
X-Originating-IP: [192.168.12.48]
From: "Louis Cipher" <louiscipher2002@hotmail.com> To: john.doe@receiving.com
Subject: Look behind you
Date: Wed, 28 Aug 2002 21:42:08 -0400
Message-ID: <F148Bi89QtpfTYSl1q400015c21@hotmail.com>
X-OriginalArrivalTime: 29 Aug 2002 01:42:08.0339 (UTC)
FILETIME=[494ED230:01C24EFD]
I'm watching you
Louis Cipher
__________________________________________________________
Send and receive Hotmail on your mobile device: http://mobile.msn.com
Hotmail and many other similar services keep logs that can be useful for identifying the sender. In one case, by tracing a Hotmail message to a library computer in Berkeley, investigators located a fugitive named Troy A. Mayo who was wanted for questioning in the death of a pregnant teenager. Keep in mind that a Web proxy can be used to hide the IP address of the originating computer making it much more difficult to determine the actual source of the message. When a proxy is used, the message header will contain the IP address of the proxy server and it would be necessary to obtain access logs from the proxy server to determine the actual origin of the message.
EAN: 2147483647
Pages: 279