16.2 Linking the Data-Link and Network Layers - Encapsulation
16.2 Linking the Data-Link and Network Layers - Encapsulation
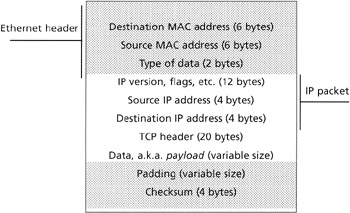
In addition to connecting computers to the network, the data-link layer prepares data for their journey through the physical layer. For example, before sending an IP packets, Ethernet adds a header and checksum (a number used to verify the integrity of the data), encapsulating the packet in an Ethernet frame. Table 16.2 shows the segments of an IP packet encapsulated in an Ethernet frame.
|
|
Why are two types of addresses required - an IP address and a MAC address? Each address serves a different purpose. Put simply, Ethernet enables communication between hosts on the same network using MAC addresses while TCP/IP enables communication between hosts on different networks using IP addresses. Computer applications use TCP/IP to communicate, regardless of the network technology involved and computers themselves use the local network technology to exchange data. So, before an IP packet can be transmitted through the physical and data-link layers, it must be encapsulated in the local language (e.g. Ethernet, ATM, FDDI). For instance, at the data-link layer, Ethernet uses a particular kind of MAC addresses (e.g. 08-00-56-12-97-A8) to direct data, encapsulating IP packets into Ethernet frames as shown in Table 16.2.
Recall from Chapter 14, when a computer on one Ethernet network needs to send information to a computer on another network, it must send the information through a router.
In Figure 16.3, to deliver data to host Z, host A must first encapsulate data from the application layer, addressing packets and delivering them to the router. So, host A puts the data in an IP packet addressed to host Z and then encapsulates the IP packet in an Ethernet frame addressed to the router. When it receives the frame, the router peels off the Ethernet header and sees host Z's IP address. Once it sees that the IP packet is addressed to host Z on an ATM network, the router re-encapsulates the packet in an ATM cell (the ATM equivalent of an Ethernet frame) and sends it directly to host Z.
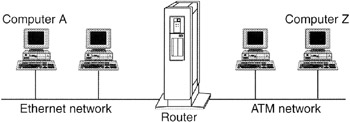
Figure 16.3: Computer A sending data to computer Z.
When host Z receives the ATM cell, it does the opposite of what host A did to send the data. The data-link layer on host Z peels off the ATM header and passes the IP packet to the TCP/IP software. Then, the TCP/IP software peels off the TCP and IP headers and passes the data to the appropriate application (e-mail, Web, Usenet, IRC, etc.).
One key point about MAC addresses is that they do not go beyond the router. Unlike IP addresses, MAC addresses are only used for communication between computers on the same network. Therefore, when a packet is sent through the Internet, it does not contain the MAC address of the computer that created it, only that of the local router that delivered it. If logs of network traffic are kept (e.g. Argus logs), investigators may be able to track data back to their source using MAC addresses.
CASE EXAMPLE
An organization noticed a large spike in their outbound network traffic, indicating that a denial of service attack was being launched from one of their hosts (192.168.0.7). However, when this host was examined, nothing unusual was found, suggesting that the attack had been launched from a different host, using the IP address 192.168.0.7 to misdirect investigators. Fortunately, the following Argus logs were available (only a small selection of the thousands of log entries are shown here).[1]
% ra -m -t 01:00 - 08:00 -r /var/log/argus/argus.out - udp and host 192.168.0.1 01:03:17 udp 0:0:e2:7a:c3:5b 0:10:2f:1d:cd:ef 192.168.0.7.32769 <-> 172.16.102.45.80 03:03:19 udp 0:0:e2:7a:c3:5b 0:10:2f:1d:cd:ef 192.168.0.7.32769 <-> 172.16.102.45.80 03:21:16 udp 0:0:e2:7a:c3:5b 0:10:2f:1d:cd:ef 192.168.0.7.32769 <-> 172.16.102.45.80 05:03:24 udp 0:0:e2:7a:c3:5b 0:10:2f:1d:cd:ef 192.168.0.7.32769 <-> 172.16.102.45.80 07:03:25 udp 0:0:e2:7a:c3:5b 0:10:2f:1d:cd:ef 192.168.0.7.32769 <-> 172.16.102.45.80 07:51:58 udp 0:0:e2:7a:c3:5b 0:10:2f:1d:cd:ef 192.168.0.7.32769 <-> 172.16.102.45.80
These logs show a computer with MAC addresses (00:00:e2:7a:c3:5b) using the IP address in question. This system was located - an IBM Thinkpad running Linux that had been compromised and used as a launch pad for the denial of service attack. The other MAC address in these Argus logs belongs to the local switch, not the target of the attack.
MAC addresses can also sometimes be used to classify the type of machine. For instance, Ethernet MAC addresses comprise 12 hexadecimal digits (e.g. 00-10-4B-DE-FC-E9). The first six hexadecimal digits, called the Organizationally Unique Identifier (OUI), refer to the vendor of the NIC and the last six digits are the serial number for the particular NIC. Table 16.3 lists a small selection of vendors and their associated Ethernet MAC address prefix.[2] Note that large companies such as Cisco and 3Com use different identifiers for different product lines.
| PREFIX | MANUFACTURER | PRODUCT (WHEN APPLICABLE) |
|---|---|---|
| 001007 | Cisco Systems | Catalyst 1900 |
| 00100B | Cisco Systems | |
| 00100D | Cisco Systems | Catalyst 2924-XL |
| 001011 | Cisco Systems | Cisco 75xx |
| 00101F | Cisco Systems | Catalyst 2901 |
| 001029 | Cisco Systems | Catalyst 5000 |
| 00102F | Cisco Systems | Cisco 5000 |
| 00104B | 3Com | 3C905-TX PCI |
| 00105A | 3Com | Fast Etherlink XL in a Gateway 2000 |
| 006097 | 3Com | |
| 080020 | Sun | |
| 0001AF | Motorola | |
| 080056 | Stanford University | |
| 08005A | IBM | |
| 0001E6 | Hewlett-Packard | |
| 3C0000 | 3Com | Dual function (V.34 modem + Ethernet) card |
| 444553 | Microsoft | Windows95 internal "adapters" |
Ethereal uses this OUI information to classify network addresses. For instance, Figure 16.4 shows Ethereal being used to monitor traffic between a Nokia Wireless Access Point and several hosts, including an Apple system (OUI 003065).
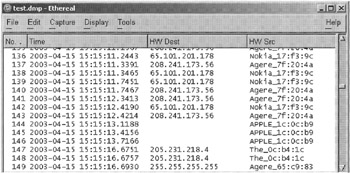
Figure 16.4: Ethereal classification of NIC addresses.
This type of class characteristic can be useful for narrowing a search on a network - knowing that the suspect used an Apple system can make it easier to locate the computer in question.
16.2.1 Address Resolution Protocol (ARP)
Computers on a network do not necessarily know each other's MAC addresses. For example, when a computer wants to send an IP packet, it only knows the IP address of the destination host. To discover the MAC address of the destination host, a computer simply asks every other host on the network: is this your IP address? The host with that IP address responds with its MAC address. This simple exchange is called the Address Resolution Protocol (ARP).
Although ARP is part of TCP/IP, it is generally considered a part of the data-link layer. The easiest way to think about ARP is to imagine it straddling the network and data-link layers (Figure 16.5).
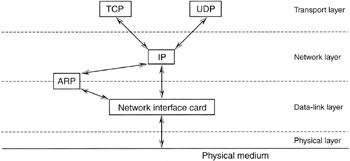
Figure 16.5: Summary diagram of TCP/IP separated by OSI layer.
This address discovery process might seem like a lot of effort that could be replaced by a list of IP → MAC address associations. However, every computer would have to have such a list and whenever a computer was added to the network, the list on each computer would have to be updated. As a compromise, computers keep a temporary list of IP → MAC address associations. So, two computers that communicate frequently will not have constantly to remind each other of their respective IP addresses. This temporary list is called an ARP table (a.k.a. ARP cache) and can be viewed on Unix and Windows NT/2000/XP machines using the arp -a command as shown here:
:~% arp -a Net to Media Table Device IP Address MAC Addr ---------- ------------------------------ ------------------- e0 192:168.1.1 08:00:20:75:d3:fb e0 192.168.1.3 08:00:20:1c:1f:67 e0 192.168.1.4 08:00:20:1c:6a:ff e0 192.168.1.9 00:60:83:24:1f:4d e0 192.168.1.23 08:00:20:7d:40:9c e0 192.168.1.33 08:00:20:80:fe:34 e0 192.168.1.39 08:00:20:7f:17:3c e0 192.168.1.45 08:00:20:7d:e3:94 e0 192.168.1.53 00:04:ac:44:3f:4e e0 192.168.1.75 08:00:20:1c:5b:df e0 192.168.1.103 08:00:20:87:2c:73 e0 192.168.1.144 08:00:20:86:4a:cf e0 192.168.1.134 08:00:20:87:a5:bb e0 192.168.1.232 08:00:20:86:e2:5c e0 192.168.1.234 08:00:20:7e:2d:ef
So, if a criminal reconfigures his computer with someone else's IP address to conceal his identity, the local router would have an entry in its ARP table showing the criminal's actual MAC address associated with someone else's IP address. If the record in the ARP table is not used for a while (usually between 20 minutes and 2 hours), it is deleted. Notably, IPv6 addresses contain the MAC address of the network interface they are associated with.
16.2.2 Point to Point Protocol and Serial Line Internet Protocol
The use of modems to connect computers to the Internet deserves a quick mention here. Many people dial into an ISP to connect to the Internet - transmitting data over a copper telephone line instead of an Ethernet or fiber optic cable. This type of connection is much less sophisticated than network technologies like Ethernet, FDDI, and ATM. An addressing scheme is not required since the modem in a person's home is connected directly to one of their ISP's modems through telephone wires. All that is required is a simple method of encapsulating IP packets and sending them over the telephone wires. Several protocols do just this, including Point to Point Protocol (PPP) and Serial Line Internet Protocol (SLIP). Although it is open to debate, think of PPP and SLIP as on the data-link layer and the serial line that they use as on the physical layer in a dial-up connection. Notably, many broadband Internet providers are using PPP over Ethernet (PPPoE) to establish a PPP connection using a variation of the Ethernet protocol.
[1]In this example, Argus was installed on the same physical network segment. On larger networks, Argus can monitor multiple segments using proxy ARP and can record Virtual Local Area Network (VLAN) tags that identify which VLAN the data relate to.
[2]A more complete list can be found at http://www.cavebear.com/CaveBear/Ethernet/vendor.html and a searchable database of these vendor codes can be found on the IEEE Web site at http://standards.ieee.org/regauth/oui/index.shtml. Keep in mind that vendors sometimes use other vendor's cards, such as a 3COM card in a Cisco device.
EAN: 2147483647
Pages: 279
- Chapter II Information Search on the Internet: A Causal Model
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XI User Satisfaction with Web Portals: An Empirical Study
- Chapter XV Customer Trust in Online Commerce