13.2 Collection and Examination of Handheld Devices
13.2 Collection and Examination of Handheld Devices
In addition to collecting a handheld device itself, it is important to look for associated items that might contain data or help extract data from the device. Removable memory and SIM cards can contain more data than the device itself and interface cables and cradles may be needed to connect the device to an evidence collection system. As with any other computer, document the types of hardware and their serial numbers, taking photographs and notes as appropriate. If a device is on when it is found, leave it on if possible because turning it off may activate password protection, making it more difficult to extract data from the device later. Also, document any information visible on the display including the date and time of the system clock.
Since data in RAM will be lost if it does not receive power, adequately charged batteries are crucial. Even when the device appears to be off, it is consuming some battery power. If there is any indication that the batteries in the device are low, consider replacing them with fully charged batteries. Also, to protect the device against damage or accidental activation, package it in an envelope or bag. Keep in mind that some devices can receive data through wireless networks that might bring new evidence but might overwrite existing data. Therefore, an investigator must make a calculated decision to either prevent or allow the device to receive new data over wireless networks.[8]
After taking precautions to preserve data on the device, examine it for physical damage or suspicious modifications. In most cases, a cursory examination of the exterior of the device will suffice. However, when dealing with a very technically savvy or dangerous offender, some investigative agencies X-ray devices to detect internal damage or modifications. Be aware that a blank display may simply indicate that the screen is damaged and it may still be possible to extract evidence via cable or replace the screen if a manual examination is necessary. A manual examination is sometimes sufficient if investigators only need a particular piece of information from the device. Before performing a manual examination of a device, it is advisable to become familiar with its operation using an identical test device. For this reason, and to enable tool testing and tool development, forensic laboratories that specialize in this type of examination maintain an extensive collection of handheld devices. When performing a manual examination, it is important to record all actions taken with device to enable others to assess whether the examination was performed satisfactorily.
When investigators require all logical files or deleted evidence from a device, special tools are used to acquire and examine this data. Some of these tools are described in the following sections. A more in-depth coverage of tools and techniques for processing evidence on handheld devices and other embedded systems is available in the Handbook of Computer Crime Investigation, Chapter 11 (Van der Knijff 2001).
13.2.1 Palm OS
There are several tools for acquiring digital evidence from devices running Palm OS, each with their own advantages and limitations. Some of these tools can only perform full memory dumps, while others can also extract logical databases. Some of these tools can only acquire evidence through a serial connection, while others can also acquire evidence via a USB connection. Some of these tools require the device to be placed in console debug mode, causing a soft reset after collection. Recall from the previous section that a soft rest triggers heap compaction, which overwrites deleted records, so this method only allows one chance to acquire deleted data from the device.
The two most versatile tools for acquiring and examining digital evidence from a Palm OS device are Pilot-link[9] and PDA Seizure. Both of these programs can interpret Palm databases, enabling examiners to view data in their logical form.
13.2.1.1 Unix-Based Tools
Although not specifically designed for evidence processing, the Pilot-link package contains UNIX utilities that can be used to acquire and examine data from a Palm OS device. These utilities include pi-getram and pi-getrom for obtaining memory dumps, pilot-xfer for accessing and copying data logically, and the previously mentioned pilot-file for interpreting and examining logical Palm databases. The following output shows pi-getram in the process of obtaining a physical copy of data in RAM. Unfortunately, pi-getram does not always capture the full contents of RAM, a severe limitation that may be corrected in the future.
examiner1% pi-getram /dev/cua1 pda1-evidence Please insert the Palm in the cradle and press the HotSync button. Generating pda1-evidence3.1.0.ram 299264 of 2097152 bytes
The resulting memory dumps do not provide any structure to the data they contain, leaving it to the examiner to extract any information they can, such as passwords, hidden data, and deleted items. The following output shows pilot-xfer being used to make a logical copy of databases in RAM.
examiner1% pilot-xfer -p /dev/cua0 --Illegal --sync pda1-evidence Please press the HotSync button now... Connected... Synchronizing pda1-evidence/Unsaved Preferences.prc Synchronizing pda1-evidence/AddressDB.pdb Synchronizing pda1-evidence/MemoDB.pdb Synchronizing pda1-evidence/ToDoDB.pdb Synchronizing pda1-evidence/MailDB.pdb Synchronizing pda1-evidence/DatebookDB.pdb Synchronizing pda1-evidence/Saved Preferences.prc Synchronizing pda1-evidence/NetworkDB.pdb Synchronizing pda1-evidence/Secret!.prc Synchronizing pda1-evidence/Secret2.pdb <cut for brevity> Synchronizing pda1-evidence/ROM Transfer.prc Synchronizing pda1-evidence/FlashPro.prc Synchronizing pda1-evidence/FlashPro Setup.prc Synchronizing pda1-evidence/FlashPro Uninstall.prc RAM backup done.
The "--Illegal" option instructs pilot-xfer to extract the "Unsaved Preferences" database that contains the password protecting private data on the device. The pilot-xfer utility has several other useful options including "--Flash" to copy not operating system files from FLASH and "--archive" to recover deleted records that have their archive bit set. Making a logical copy of databases does not recover records with their delete bit set, even if the data is still in memory. These deleted data are preserved in a full memory dump.
Notably, the pi-getram and pi-getrom utilities use a HotSync conduit and therefore do not require the device to be in console debug mode. Interestingly, although they use the HotSync feature, these utilities do not change the Last HotSync date on the device. So, although the Pilot-link package was not designed specifically for processing digital evidence, it does not alter data on the device by causing a soft reset or updating the Last HotSync date.
13.2.1.2 Windows-Based Tools
PDA Seizure was specifically designed to collect and examine digital evidence on personal digital assistants and can also be used to extract databases from a Palm device as shown in Figure 13.2. To capture this logical structure, PDA Seizure uses the HotSync feature of Palm OS devices.
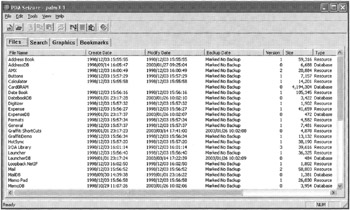
Figure 13.2: Print screen of PDA Seizure showing logical databases.
Although earlier versions of PDA Seizure changed the Last Hotsync date-time stamp, this has been remedied in version 2.5. By default, extracted databases only include deleted records that have the archive bit set. Other deleted entries are not recovered using the PDA Seizure logical copy feature, even if they still exist in memory. A full memory dump will preserve these deleted data. PDA Seizure can dump the contents of RAM and ROM into a file. Also, PDA Seizure calculates hash values of all digital evidence it collects for future integrity checking and provides several useful features including a report generator and search function.
Aspects of another tool called pdd have been incorporated into PDA Seizure. One advantage of pdd is that it obtains the actual size of ROM from the CPU rather than relying on the Palm Application Programming Interface (API). This is significant because the Palm API only reports the amount of ROM that the device uses rather than the actual size of the ROM chip, thus misinforming any program that relies on the API for information. Therefore, a tool that relies on the Palm API may miss any data that has been stored in portions of ROM that are not used by Palm OS.
EnCase provides the basic ability to dump RAM and ROM, performing integrity checks and initiating chain of custody as usual. The features of each of these tools are compared in Table 13.2. The RAM and ROM memory sizes detected by each tool are compared in Table 13.3.
| TOOL | MEMORY DUMP | ACTUAL RAM SIZE | ACTUAL ROM SIZE | LOGICAL COPY | SOFT RESET | MD5 | USB |
|---|---|---|---|---|---|---|---|
| EnCase 4 | x | x | x | x | x | ||
| PDA Seizure 2.5 | x | x | x | x | x | x | |
| pdd 1.11 | x | x | x | x | |||
| Pilot-link | x | x | x | x |
| TOOL | RAM DETECTED (BYTES) | ROM DETECTED (BYTES) |
|---|---|---|
| EnCase 4 | 4194304 | 1212416 |
| PDA Seizure 2.5 | 4194304 | 1572864 |
| pdd 1.11 | 4194304 | 2097152 |
| Pilot-link | 4063232 | 2097152 |
An advantage to having a logical copy of data from a Palm OS device is that databases acquired from the evidentiary system can be exported from PDA Seizure and loaded into the Palm OS Emulator (POSE) where they can be viewed as they were seen by the user (Figure 13.3). This is particularly useful for viewing and presenting evidence because it displays information in a familiar form.

Figure 13.3: Image/data being viewed using Palm OS Emulator (POSE).
To import evidentiary Palm databases into POSE, save it to disk using Pilot-link or PDA Seizure's export features, and simply drag and drop the database into POSE.
13.2.2 Windows CE Devices
Like Palm OS devices, Windows CE devices store data in RAM (divided into heaps) and operating system files in FLASH. However, Windows CE arranges data in memory using a different format from Palm OS. Windows CE stores data in an "object store" comprised of a file system, databases (Address book), and a system registry. These devices are capable of accessing the Internet and other remote resources like SQL databases. Therefore, they may contain data relating to an individual's network activities. As with Palm OS, developer kits for Windows CE contain emulators and debugging tools that are useful for learning more about these systems. Additionally, tools like FlashBack enable individuals to save data into Flash memory on Windows CE devices. Currently, PDA Seizure is the only tool for capturing evidence from a Pocket PC and Windows CE devices.
13.2.3 RIM Blackberry
As with Palm OS, the Research in Motion (RIM) Blackberry handheld devices use a database structure with data in separate records. However, RIM devices differ from Palm OS and Windows CE devices in that they store user data in FLASH rather than RAM. As noted earlier, this is an advantage from a data recovery standpoint because data can only be erased from FLASH in 64-kbyte blocks, a time consuming process in computer terms (approximately 5 seconds) that is only performed when absolutely necessary. Therefore, RIM devices simply add new records and new versions of modified records to the end of the database, marking deleted or modified records as old. Only when the file system runs out of space do RIM devices perform the costly process of erasing blocks of FLASH, removing old and deleted records in the process.
RIM devices are designed to provide mobile users with remote access to Internet and corporate systems. In addition to sending and receiving e-mail and text messages, remote storage interfaces enable users to access and save files on a remote server. As a result, these handheld devices often contain e-mail and other network related data of a sensitive nature. Although some RIM devices allow secure, encrypt communication with a remote server, data on the device itself is not automatically encrypted.
Like Palm OS devices, Blackberry provides a debugger (named Programmer) and simulator in their Standard Developer's Kits (SDK) that can be used to access RIM devices. The Program Loader can be used to query the device and make memory dumps, but can cause a soft reset that usually decimates useful information on the device such as logs of recent data transfers and radio towers. Therefore, it is advisable to obtain some of this information by manually examining the device before performing a full memory dump.
13.2.4 Mobile Telephones
The variety of mobile telephones makes it difficult to develop a single digital evidence examination tool for all of them. Additionally, investigators often only want specific data from the telephone such as recent numbers called and received, and are not interested in recovering deleted data. Furthermore, the large number of phones that exist makes it prohibitively time consuming to perform a lengthy examination of each one. For these reasons, in many cases investigators are required to perform a manual examination of a telephone, reading data from the display and documenting their findings. Digital evidence examiners with specialized tools are usually only employed when deleted data is required or if password protection or encryption must be bypassed.
As a result of the growing popularity of GSM, commercial products have been developed to enable individuals to access their SIM card using their computers. The programs are not designed with digital evidence examination in mind but can be useful for collecting the types of information that are obtained during a manual examination. For instance, SIM Manager Pro can be used to read certain data from a GSM SIM card such as text messages as shown in Figure 13.4. This program does not bypass the personal identification number (PIN) that protects the SIM. Therefore, the PIN must be obtained or bypassed in some other way before the SIM can be accessed using this software.
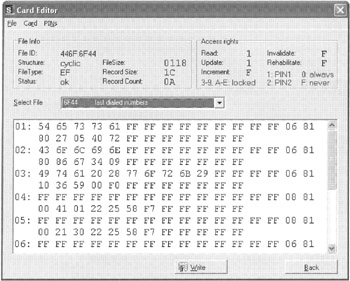
Figure 13.5: A SIM card viewed using Card Editor SIM Manager Pro.
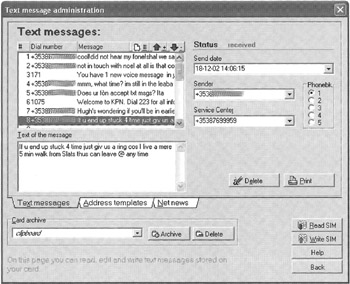
Figure 13.4: Text messages on a SIM card viewed using SIM Manager Pro.
Because this software is not designed with digital evidence examination in mind, it does not write-protect the SIM card. Therefore, when using this tool, great care must be taken not to alter the original data. In fact, SIM Manager Pro is specifically designed to facilitate data entry so that individuals can update their address book via their computer. SIM Manager Pro has a Card Editor that can be used to access and alter certain parts of a SIM card as shown in Figure 13.5. Although it can be useful to view data on the card in uninterrupted form, the Card Editor does not give access to all regions on the card and may not show all data.
The Netherlands Forensic Institute has developed tools specifically for processing digital evidence on mobile telephones, SIM cards, and PDAs, some of which have the ability to recover deleted data. These tools are described in the Handbook of Computer Crime Investigation, Chapter 11 (Van der Knijff 2001).
[8]Some devices can be reconfigured to prevent communication with the network. Devices that do not have such a feature can be isolated from radio waves by wrapping them in aluminum foil. However, this can cause the battery in the device to deplete more quickly.
[9]http://www.pilot-link.org
EAN: 2147483647
Pages: 279