Administrative Security
An Administrative Group (AG) is a container that holds other objects for the purpose of securing those objects under a common security context for administrative tasks. Administrative Groups can contain servers, routing groups, policies, and public folder hierarchies.
One of the best ways to secure your Exchange servers is to use the Administrative Groups permissions structure to limit who can make configuration changes on one or more Exchange Server 2003s. Exchange has a tight integration with Microsoft Windows Server 2003 Active Directory. Therefore, the user and/or group accounts in Active Directory can be used to secure the Administrative Groups in Exchange 2003, strictly limiting the individuals who can make configuration changes to objects (including servers) in those administrative groups.
If in your environment more than one set of Exchange servers needs to be managed by more than one team of people, the value in using Administrative Groups will become clear. In this scenario, you can use two Administrative Groups to administer each set of Exchange servers by delegating permissions for each group to each set of administrators. You set this up in the Exchange System Manager (ESM), but you delegate permissions to the Active Directory accounts. Doing this means that only the authorized Administrator for a particular set of servers can modify configuration values on those servers. Regardless of the administrative model you use—centralized, decentralized, or hybrid—you can create Administrative Groups to handle your model and secure your servers.
To create an Administrative Group, open the ESM and navigate to the Administrative Groups object. Right-click the object, point to New, then select Administrative Group (Figure 24-3).
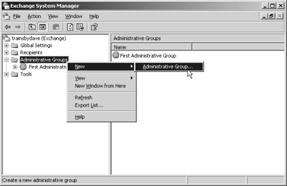
Figure 24-3: Creating a new Administrative Group in the Exchange System Manager.
The Properties dialog box will appear for the new AG. The only configuration value you can give the group is the group’s name. Enter the name and click OK. You’ll see the group appear in the ESM.
After the AG is created, you can rename the group if you desire. In our example, we have two AGs: the default group we renamed to East Administrative Group and the new group we named West Administrative Group (Figure 24-4).
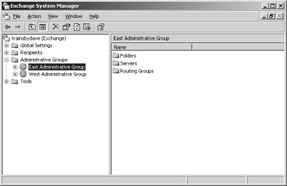
Figure 24-4: Two Administrative Groups named East and West in the Exchange System Manager.
Suppose you want to secure these two AGs with different groups from Active Directory. You want both groups of administrators to be able to manage the objects in their own AG but only view the configuration values for objects in the other AG. To set this up, create two Active Directory security groups. In our example, we’ll call the first one ExchangeEast and the other ExchangeWest. After you create these groups, use the Exchange Administration Delegation Wizard to apply Exchange View Only permissions to the Organization object for both groups. You assign permissions in this way because, as you know, the objects in Exchange have a tight integration with the security model in Active Directory and Windows Server 2003, and permissions inheritance is part of this security model. When you apply the Exchange View Only permissions to the Organization object of these groups, all the objects beneath the Organization object, including the AGs, inherit this permission. You apply the permissions to the Organization object because the Exchange Administration Delegation Wizard is available only on the Organization and AG objects in the ESM. If you right- click on any other object, you will not see this wizard available.
To open the Wizard, right-click on the Organization object and select Delegate Control. Click Next to pass the Welcome screen. On the Users Or Groups page, click the Add button and select the two Active Directory security groups you’ve created. In our example, we select the ExchangeWest and ExchangeEast security groups (Figure 24-5).
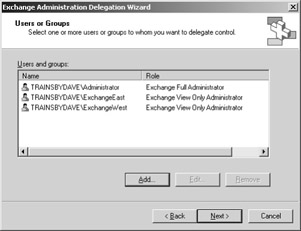
Figure 24-5: Selecting the ExchangeWest and ExchangeEast security groups in the Exchange Administration Delegation Wizard.
When you add a group using the wizard, the default security role is Exchange View Only Administrator. You can change this role by highlighting each group, and then clicking the Edit button. You will be presented with three options:
-
Exchange View Only Administrator This role allows you to view configurations on the objects, but you are unable to make any changes to those configurations.
-
Exchange Administrator This role allows you to administrate the object fully with the exception of changing the Administrator role permissions on the object.
-
Exchange Full Administrator This role allows you to administer the object fully, including the ability to change Administrator role permission assignments.
You can change the default role assignment, but for our example, we’ll use the default Exchange View Only Administrator setting because we want this setting to be inherited by the AGs so that each group has the ability to view the configuration values in the other AG’s objects.
Your next step is to run the delegation wizard on each individual AG and give Exchange Administrator permissions as follows:
-
ExchangeEast assigned to the East Administrative Group
-
ExchangeWest assigned to the West Administrative Group
Once you have finished doing this, in the properties of each AG, you’ll see that the group responsible for administrating that AG will have Exchange Administrative permissions, but the other group will have the ability to view the configuration values on the AG that they are not permitted to administrate. Figure 24-6 shows the East Administrative Group’s permissions assignments; the ExchangeWest has Exchange View Only Administrator permissions and the ExchangeEast has Exchange Administrator permissions.
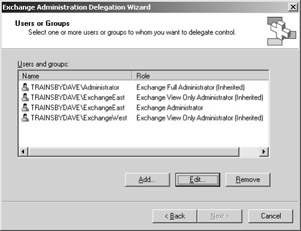
Figure 24-6: Viewing the East Administrative Group’s permissions.
You must consider two issues with this scenario. First, for a security group to have all the abilities of administration provided by the Exchange Administrator role, that group must also be a member of the Local Administrator’s security group. Second, you can’t change inherited permissions on an object. This is why the ExchangeEast group appears twice in the permissions assignments: once for the inherited permissions from the organization object, and a second time for the explicit permissions assignment on the AG itself.
Also note that the combination of permissions allows for the most liberal of the permissions to apply. Hence, in this scenario, since the same group (Exchange East) has both Exchange View Only Administrator and Exchange Administrator permissions, the administration permissions will apply.
A second way to limit administrative access to your Exchange servers is to limit who can log on locally to the Exchange servers. You can set this limit by using a Group Policy in Windows Server 2003 and assigning that policy to an Organizational Unit (OU) that hosts all Exchange server accounts in Active Directory (Figure 24-7). You can make this permission assignment by creating (or linking to) a group policy that configures the following policy: Windows Settings/Security Settings/Local Policies/User Rights Assignements/Allow log on locally.
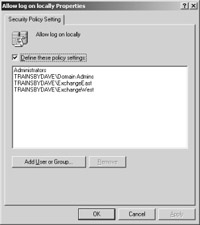
Figure 24-7: Allowing the log on locally policy setting, adding the ExchangeEast and ExchangeWest security groups.
A third way to secure access to the Exchange server is to limit who has the ESM installed on their desktops. By default, when you install only the ESM, Active Directory Users and Computers is also installed. Deploying these two snap-ins on your administrator’s desktops creates additional vectors to your Exchange servers. In some environments, this will be acceptable, but in others, it will not. Be sure that you know where all your ESM snap-ins are installed and remove those snap-ins when the administrator leaves your company or is assigned a different role.
A fourth approach to limiting administrator access to your Exchange servers is to require some type of smart card or biotechnology for logon to the servers. Entering a thumbprint, taking a retina scan, or swiping a card will help ensure that only the real Exchange administrators are logging on to your Exchange servers.
EAN: 2147483647
Pages: 254