Windows 2000 Components and Features
3 4
Now that we have covered the basics of the Windows 2000 family, let's focus on Windows 2000 features. These features can be divided into several categories: reliability, security, ease of use, system administration, mobile computing, performance and scalability, Internet access, and, finally, Active Directory.
Reliability
Windows 2000 incorporates many new features to increase the reliability of your system. Let's look at a few of these key features:
- Windows file protection This feature protects the core Windows 2000 system files from being accidentally deleted or altered by either a user or an application. Windows file protection automatically verifies the source and the version of a system file before it is installed.
- Driver certification Each member of the Windows 2000 family implements certification of drivers and other system-level files. This certification ensures that the device drivers on your system have not been tampered with and that the device driver you are using is the one intended by the manufacturer of the hardware or software component.
- Microsoft Installer This tool works with Windows Installer Service and helps users install, configure, track, upgrade, and remove software programs correctly. This interface provides users with an intuitive and easy-to-use method for installing and removing diverse applications. In addition to providing interface support, Microsoft Installer can repair damaged applications. Microsoft Installer examines a large collection of components—such as the registry, files, and external resources—and monitors all component modification tasks. If a user accidentally deletes a critical component of an application, Microsoft Installer detects the missing component when the application is started again and restores the missing files. This feature protects only applications that are labeled "Certified for Windows 2000" or that have been installed with Microsoft Installer.
- Kernel-mode write protection This feature puts up a "fence" between applications and the critical kernel of the operating system. It protects the kernel from rogue device drivers that might cause a Windows NT 4 system to crash.
- Fewer reboot requests Previous versions of Windows frequently required you to reboot the system when you added or removed device drivers, applications, and so forth. With Windows 2000, these reboot requests have been dramatically reduced—to the point that many software installations do not require you to reboot.
- Microsoft Internet Information Server (IIS) application protection This feature isolates Web-based applications from the actual Web server code, ensuring that an application cannot crash the Web server. This feature does not apply to Windows 2000 Professional.
- Windows 2000 logo program Microsoft has developed a comprehensive set of standards for Windows 2000 applications. An application that carries the Windows 2000 logo is guaranteed to meet these standards and has therefore been certified for use with Windows 2000. The standards were developed with the cooperation of customers and third-party developers.
Security
Today's computing environments have differing security requirements. Windows 2000 allows you to customize the level of security to meet your needs. The following features assist you in securing both your computer and network access:
- Windows NT file system (NTFS) The Windows NT file system is the core security technology in Windows 2000. NTFS provides file security at a group or user level.
- Windows NT security model This feature permits only authorized users to access system resources. This model controls which user or users can access objects, such as files and printers, as well as which actions individuals can take on an object. In addition, you can enable auditing to track and monitor actions taken, as well as to track actions that a user attempted that would have violated a security policy.
- Encrypting file system (EFS) This feature encrypts files with a randomly generated key. The encryption and decryption processes are transparent to the user. EFS requires your disks to be formatted with NTFS.
- IP Security (IPSec) support IP Security helps protect data transmitted across a network. This is an integral component for providing security for virtual private networks (VPNs), which allow organizations to transmit data securely across the Internet. Figure 2-1 displays the IP Security configuration dialog box.

Figure 2-1. The IP Security dialog box.
- Kerberos support This feature provides an industry-standard, highly secure authentication method for single-logon support for Windows 2000—based networks. The Kerberos protocol is an Internet standard and is highly effective when you are integrating Windows 2000 systems into an environment with a different operating system, such as UNIX.
Ease of Use
Some of the most important features of Windows 2000 are its ease-of-use features. Without these features, Windows 2000's myriad and complex functions would be extremely difficult to use. The operating system incorporates many new features that make it one of the most easy-to-use operating systems. Some of these features are listed here:
- Plug and Play This feature allows you to install hardware components with only minimal configuration. More than 12,000 devices support the Plug and Play standard.
- Multilingual support Windows 2000 allows complete flexibility in language selection to match a user's requirements.
- Peer-to-peer support Your Windows 2000 system can operate seamlessly with earlier versions of Windows on a peer-to-peer level. You can share all resources, including folders, printers, and other peripherals.
- Personalized menus Windows 2000 dynamically adapts the Start menu options to the way you work on your system. Your most-used applications stand out on the menu because infrequently accessed items are not immediately displayed.
- Troubleshooters These wizards are similar to the other wizards you might have seen, and they help you configure, optimize, and troubleshoot your system. Using troubleshooters results in fewer help desk calls, which increases productivity.
- Windows Multimedia Previewer This feature allows you to view a snapshot of a multimedia file while browsing in Windows Explorer before you actually open the file.
- More and enhanced wizards These wizards provide step-by-step prompts for performing both routine and challenging tasks on your system. Figure 2-2 shows a Windows 2000 wizard that can assist you in the backup and restore process.
- IntelliMirror The IntelliMirror feature enhances users' access to their information and software. This technology greatly benefits mobile users by allowing their computer resources to "follow" them regardless of the point from which they log on to the network. One example of IntelliMirror's benefits is the use of Offline Folders. These folders allow a user to keep working on key documents even if the network connection fails. One note: this feature requires folders to be on a server running Windows 2000 Server.
Figure 2-2. The Windows 2000 Backup/Restore Wizard.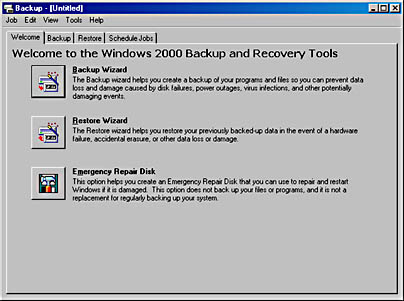
- Support for universal serial bus (USB) Windows 2000 provides native support for USB components. This allows you to connect USB devices to your system without configuring or rebooting it.
- Graphical user interface (GUI) Windows 2000 builds on the user interface of Windows 98. This interface provides users with consistent and intuitive access to even complex operations. The Windows 2000 GUI is illustrated in Figure 2-3.
Figure 2-3. The Windows 2000 graphical desktop.
- Network printer access Any user can easily access printers across a network with Windows 2000. After a printer has been "published" in Active Directory, users can search for it based on criteria such as location, ability to print color, speed, or type. Figure 2-4 shows a dialog box from the Add Printer Wizard.
Figure 2-4. A dialog box from the Add Printer Wizard.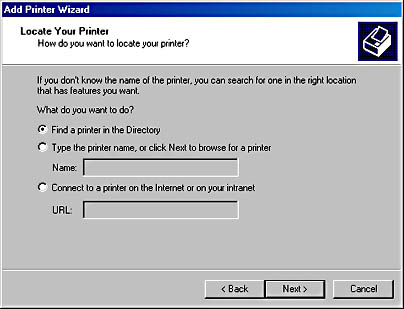
System Administration and Deployment
The Windows 2000 operating system family offers several features that enhance administration and deployment. These features aid in large-scale rollouts of the operating systems as well as in ongoing administration and maintenance. These features include the following:
- System Preparation tool This tool allows a system administrator to easily clone computer configurations, systems, and applications. SysPrep provides simpler, faster, and cost-effective deployment of Windows 2000 systems.
- Setup Manager This tool is a graphical wizard that guides system administrators through the process of designing and testing installation scripts for system deployment.
- Remote operating system installation This tool allows system administrators to standardize a desktop environment and rapidly deploy it across a network.
- Microsoft Management Console (MMC) This tool provides a consistent environment for each administrative and management tool from Microsoft as well as from third-party providers. An example of an MMC environment is shown in Figure 2-5.
Figure 2-5. The Microsoft Management Console environment.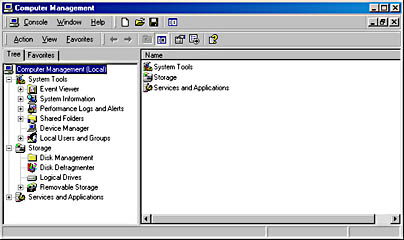
- Windows Management Instrumentation (WMI) WMI provides a standard infrastructure for monitoring and managing all system resources. This allows third-party providers to develop consistent applications to monitor and control systems.
- Group Policy Editor Group Policy Editor allows system administrators to define customized rules for virtually every facet of a user's computer environment. These policies cover areas such as security, user rights, desktop settings, and applications. The Group Policy editor window is shown in Figure 2-6.
Figure 2-6. The Group Policy editor window.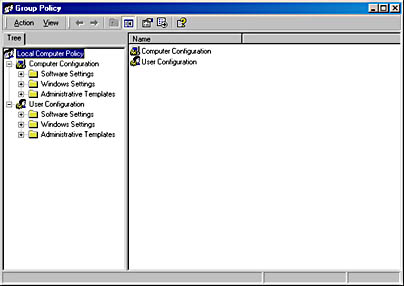
- Internet Explorer Administration Kit (IEAK) IEAK enables system administrators to quickly deploy a customized version of Microsoft Internet Explorer 5.01 across multiple platforms. Administrators can install only the components and custom applications they need.
- Microsoft distributed file system (Dfs) Dfs enables the administrator to build a single, hierarchical view of multiple file servers and their resources on a network. Dfs makes it easy for users to locate services and resources. In addition, it can increase resource availability by maintaining multiple file copies across distributed servers.
- Disk quotas System administrators can set quotas on disk space usage per user and per volume. The Quota tab of the Local Disk Properties screen is shown in Figure 2-7.
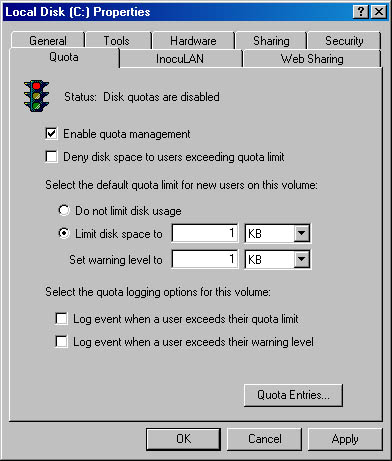
Figure 2-7. The Quota tab of the Local Disk Properties screen.
- Hierarchical storage management This feature automatically migrates data that has not been recently accessed to less expensive storage media. This maximizes high-speed, high-cost media usage for those applications and data that are the most heavily accessed.
- Dynamic volume management Windows 2000 Storage Manager allows administrators to add volumes, extend volumes, modify mirrors, or repair RAID 5 arrays while the server is on line and servicing requests, all without affecting the end user.
- Automatic restart Services such as IIS can be set to restart automatically in the event of a failure, thereby minimizing downtime and administrator intervention.
- Kill process tree If a system administrator identifies a rogue or errant application, he or she can easily kill the process and all related processes without rebooting the system.
- Windows 2000 Configure Your Server Wizard This wizard provides a one-stop location for configuring the server system. See Figure 2-8 for an illustration of the Windows 2000 Configure Your Server Wizard.
Figure 2-8. The Windows 2000 Configure Your Server Wizard.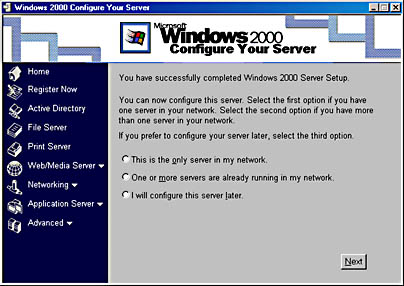
- Active Directory This component enables system administrators to manage Windows-based clients and servers through a consistent interface. See the section "Active Directory" later in this chapter for more information.
- Delegated administration System administrators can delegate sets of administrator privileges to individuals, or to groups of users, without making them administrators of the system.
- Remote management The Terminal Services component allows system administrators up to two concurrent sessions to perform remote administration on a server.
The Mobile Experience
Windows 2000 Professional was designed from the beginning to assist the notebook computer user and encourage notebook computing. Although the other Windows 2000 family members will run on a notebook system, they do not include the power management and offline features of Windows 2000 Professional. Several features were incorporated into Windows 2000 Professional that make it the desired mobile computing operating system.
- Hibernate mode This is a customizable feature that turns off the computer and monitor after a predetermined amount of time. When the system turns itself off, your desktop settings are maintained on the system hard disk drive. When you reactivate the system, the hibernate feature restores your programs and settings exactly as you left them.
- Offline Folders and Files You can disconnect from the network and work as though you were still connected. This feature allows you to create a mirror image of your documents that are stored on the network.
- Offline viewing You can make entire Web pages, including the graphics, available for offline viewing. You can later view the Web pages on your system, at your leisure, without being connected to a network.
- Synchronization Manager This tool allows you to compare and update your offline files and folders with those on the network servers.
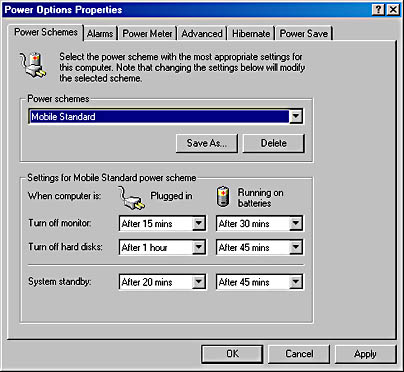
- Smart battery Windows 2000 Professional provides a more accurate view of battery life. You can easily set options to maximize battery life without sacrificing performance. The Power Options Properties window is shown in Figure 2-9.
- Hot docking This feature allows you to dock or undock your notebook computer without changing your hardware configuration or rebooting your system.
- Infrared Data Association (IrDA) support This feature lets you share data in a secure, wireless environment between two Windows 2000-based computers using a standard infrared protocol.
- Digital device support Windows 2000 Professional supports removable storage devices such as digital video disk (DVD) and Device Bay peripherals.
Performance
Operating system performance is a critical plank in the Windows 2000 platform. Extensive performance testing was done at both the operating system level and the SQL Server level. Several features are included in Windows 2000 to address performance:
- Overall faster performance Windows 2000 increases the performance of most systems. Smaller and more efficient memory footprints enable a Windows 2000 system to run up to 25 percent faster than a comparable Windows NT 4 system.
- Faster multitasking The underlying architecture of Windows 2000 is full 32-bit. This architecture allows you to better use and manage the computing resources of your computer, so you can run more programs and perform more tasks simultaneously.
- Scalability of memory and processors The Windows 2000 operating system family supports up to 64 GB of memory and up to 32 processors.
- Cluster Services Available in Windows 2000 Advanced Server and Datacenter Server, Cluster Services allows the linking of multiple systems to provide increased availability and performance. In its simplest form, Cluster Services enables two servers to be clustered to provide an automatic backup if one system fails. Cluster Services can also be configured in a "scale-out" mode, where up to 32 servers running Windows 2000 Server are linked to provide processing power.
- Network Load Balancing Windows 2000 Advanced Server and Datacenter Server support Network Load Balancing (NLB). NLB allows the operating system to dynamically and evenly distribute incoming requests across a cluster of servers running Windows 2000 Server. Administrators can add capacity to their systems by simply adding NLB-configured servers as workloads demand it. Figure 2-10 illustrates a system configuration with NLB. In this example, four servers running Windows 2000 Advanced Server are configured as a virtual server group running Internet Information Server 5 and NLB. As requests from the Internet arrive, they are apportioned to the four servers to maximize performance and utilization.
Figure 2-10. Network Load Balancing sample configuration.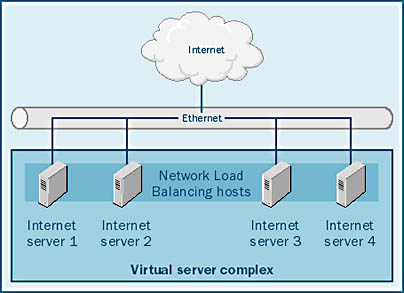
- Enhanced Active Server Pages (ASP) performance IIS 5, included with Windows 2000 Server, Advanced Server, and Datacenter Server, includes many enhancements that streamline ASP processing. The flow of an ASP Web page through the system has been improved and Fast Path was added for those ASPs that do not require any script processing.
- IIS CPU throttling For configurations that combine Web-serving applications with other applications, system administrators can limit the amount of CPU time the Web application or applications can consume. This ensures that all concurrent applications can acquire processor time when required.
Internet Access
Internet support is another key component of the Windows 2000 operating system family. Internet technologies were designed as core components of the operating system to ensure high levels of integration and performance. Some of the Internet features of Windows 2000 are listed here:
- Integrated Internet Explorer 5.01 The latest incarnation of Internet Explorer is included on all editions of Windows 2000.
- Internet Information Services 5 The Server, Advanced Server, and Datacenter Server editions of Windows 2000 all include IIS 5. The integration of this component allows users to easily host and manage Web sites. IIS 5 includes Internet Information Services Manager, a graphical environment for configuring and managing one or more Web sites. Figure 2-11 illustrates the Internet Information Services manager console.
Figure 2-11. Internet Information Services 5 Internet Information Services Manager.
- Strong development platform Internet Explorer supports a wide range of Internet programming languages, including Dynamic HTML, ASP, Java, and XML.
- Automated proxy Internet Explorer 5.01 will automatically locate your proxy server and configure itself for Internet connection.
- AutoComplete The browser remembers previously accessed sites and will complete a URL as you begin to type the first characters.
- Web Folders Also called Web Document Authoring and Versioning (WebDAV), the Web Folders feature allows an Internet content creator to easily use drag-and-drop operations to publish Web pages on IIS 5.
- Internet printing support Windows 2000 allows system administrators to share printer resources across the Internet so users can print to those printers via a URL.
Active Directory
Active Directory, a new feature in Windows 2000 Server, is the core management component for data and resources on a Windows 2000 network. This section provides an overview of Active Directory technology.
Active Directory Architecture
Active Directory is a place to store information about all network-based entities, such as applications, files, printers, and people. Active Directory provides a consistent method to describe any entity on a network, no matter how diverse the entities are. You can think of Active Directory as the main switchboard. It is a central authority that manages all the relationships among the distributed resources of a network. Active Directory contains management tools as well as security tools to maintain complete integrity and privacy of a network.
Active Directory is both a management tool and a user tool. Active Directory provides consistent user interaction with and access to the diverse and widespread resources of a network. The user no longer has to be concerned with determining a network resource location or name. With Active Directory, resources are "advertised" to those users who have been granted access. This advertisement is done via the Add/Remove Programs Wizard or the Add/Remove Printers Wizard.
Active Directory provides system administrators with a consistent set of components and controls to manage network resources. Active Directory simplifies management issues that characterize large, diverse networks; strengthens overall system security; and extends the interoperability of a network.
Active Directory provides a single point of management for all Windows-based user accounts, client systems, server systems, and applications. It also aids in organizing and integrating non-Windows systems. Active Directory allows organizations to further extend their systems to the Internet in a highly secure manner.
Active Directory is based on a hierarchical structure, which Figure 2-12 illustrates. Objects are used to represent users, groups of users, systems, devices, applications, and other network entities. Objects are kept in containers, which represent organizations, such as the legal department, or collections of related objects, such as printers.
Active Directory also manages the relationships among the various objects and containers. This allows system administrators to view the entire network as a comprehensive entity rather than looking in one place for resources and in another for resource relationships.
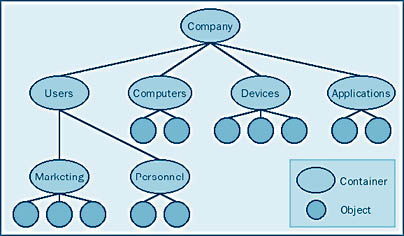
Each object in the Active Directory structure contains attributes that can describe a wide variety of characteristics. These attributes are secured so that potentially sensitive information can be hidden from everyone except those users or administrators who have a need to know. Each attribute attached to an object can have access rights assigned to it. In addition, a global access setting can be set for an object.
To maintain performance, availability, and flexibility, Active Directory uses multimaster replication. Administrators can create multiple copies of the directory, known as directory replicas, and locate them throughout their network. When a change is made anywhere on the network to any replica of the directory, the change is automatically replicated throughout the network.
Why Use Active Directory
We learned earlier that Active Directory simplifies management, strengthens network security, and eases interoperability. Let's look at each of these benefits in a little more detail.
Simplifies Management Today's networks are often distributed across a large geographical area. Managing these diverse and widespread networks can become a time-consuming process. In addition, as the network becomes geographically larger, administrative functions are often replicated in several locations, leading to redundancy and coordination issues. Active Directory provides a single point of control for managing the diverse resources of a network.
Active Directory also aids in the deployment of applications and other software to user systems. In the past, a technician had to visit each user workstation that required a piece of software. This process was costly and slow. Later, tools were developed to allow application deployment from a central server. Though this technique was better, it lacked the integration into the overall network management process. Active Directory allows system administrators to deploy software within the existing security and management framework, thereby easing the burden of using separate tools for deployment and management.
Active Directory also allows administrators to delegate some administrative functions to a user or an organization, where appropriate. This is a secure delegation process and can allow those "power users" to provide IT skills at a departmental level, thus freeing the IT staff for other duties.
Strengthens Security A critical component of Active Directory is the security services. Active Directory centralizes user authentication and management and enforces a role-based security model. Users and organizations are given roles that have predefined, yet editable, security aspects and rules. Administrators can choose to enable strict security on certain users and resources or to lessen it when appropriate. The security model of Active Directory supports security protocols such as the Kerberos protocol, X.509 certificates, and smart card technology. The security model also provides consistent security whether a user is locally connected to the network or dialed-in via a remote connection.
Extends Interoperability As networks evolved, a diverse collection of resources and technologies evolved along with them. These technologies must work together to maximize the investment in their development and deployment. The current environment of most networks includes a collection of disparate directories for e-mail, applications, network devices, Internet/intranet firewalls, and e-commerce applications. Active Directory addresses this diversity by providing a set of standard interfaces for integrating applications and a set of open synchronization mechanisms to ensure that the Windows operating system components can actively interoperate with a wide variety of non-Windows operating system devices and applications.
EAN: N/A
Pages: 264