Introduction to Virtual Private Networks
|
| < Day Day Up > |
|
You start a used bookstore called Rag-Tag Books. To control inventory and sales, you establish an internal network with internal IP addresses. As time goes by, your little bookstore expands, first past its existing walls, and then to a remote store within the same town. To connect the computers between the stores, you secure private dedicated data lines. You still have a private network.
As Rag-Tag Books becomes more and more popular, you find that you are opening branches all over town. Your store-to-store network becomes very complex, with dedicated private lines between all of your buildings in what is known as a “mesh network” (see Figure 7.1).
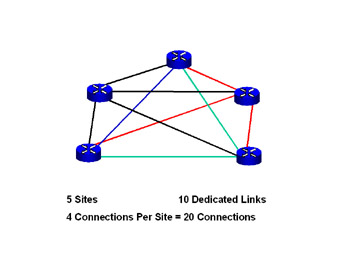
Figure 7.1: Mesh VPN Network
You need the privacy that dedicated lines give you, but the expense of private lines becomes a problem. You decide to look into a Virtual Private Network (VPN). A VPN is a network of computers that uses public carriers to interconnect the individual computers (see Figure 7.2).
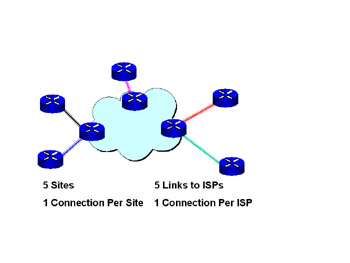
Figure 7.2: VPN Using a Service Provider
Virtual Private Networks
In days gone by companies would establish networks between their sites. They would own, manage, and control every aspect of these private networks. The ownership of their networks ensured a high level of security. As firms moved toward becoming more cost-conscious, they started to outsource network ownership and operations; however, the reduced operational costs came with increased security risk. Firms found that their data was exposed to being diverted, copied, read, and even played back.
To overcome these risks, the virtual private network (VPN) was born. A VPN is a network with the characteristics of a private network that offers protection from data modification, data interception or disclosure, and denial of service while operating on a public network (see Figure 7.3).

Figure 7.3: VPN Requirements
In order to build a secure VPN, firms with strict security requirements need to acquire special software and hardware that builds secure paths or tunnels from end to end. The software and hardware should allow for end-to-end data encryption; however, end-to-end encryption and security bring their own challenges and management issues (see Figure 7.4).
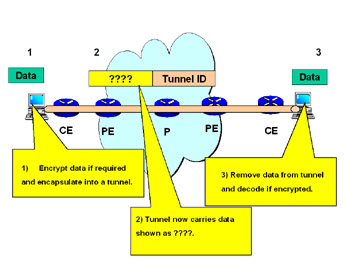
Figure 7.4: End-to-End VPN Using a Secure Tunnel
In a VPN, data is tunneled through a network. A tunnel is nothing more than an additional encapsulation process. The purpose of the tunnel is to forward the encapsulated traffic without needing to read the contents of the packets. In Figure 7.5, the basic VPN tunnel drawing illustrates the following steps:

Figure 7.5: Types of VPN Tunnels
-
The system on the left side (ingress) will encrypt data (when required and able to do so) and encapsulate data into a tunnel.
-
The tunnel will carry the data within an encapsulated packet. In the case of the drawing, the data is marked as “????.” It might be encrypted depending on the type of tunnel selected and the security needs of the organization.
-
At the far right side (egress), the system removes the data from the tunnel and removes the encryption (if the packet was encrypted), delivering data back to the end user.
Regardless of which tunnel protocol is used, we can simplify the understanding of VPNs by knowing that VPNs establish some type of tunnel from end to end. The characteristics of the tunnels that are used will determine operations and security features of the VPN.
There are several different tunneling options available that offer encryption or non-encryption. Some examples of VPN tunnels are Generic Routing Encapsulation (GRE), IP to IP (IP-IP), IP Security (IPSec), Layer-2 Tunnel Protocol (L2TP) and MPLS.
Generic Routing Encapsulation and IP-IP
These tunnel protocols are used strictly for encapsulation. They are not encryption tunnels so they offer very limited security. The GRE tunnel provides limited authentication while the IP-IP tunnel provides no authentication.
The GRE header is 16 words consisting of flags, routing, acknowledgement, and source sequence numbers. Figure 7.6a shows the GRE header and Figure 7.6b shows an IP datagram encapsulated in GRE tunnel. For a detailed explanation of the fields contained within the GRE header, see RFCs 1701 and 2890.
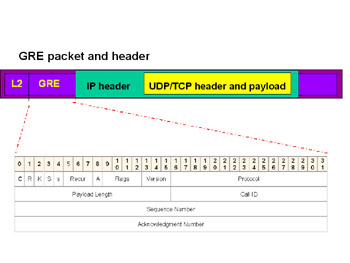
Figure 7.6: GRE Header and GRE Packet
The IP-IP tunnel is encapsulates IP packets in an additional IP header. It does not perform authentication or encryption (see Figure 7.7).
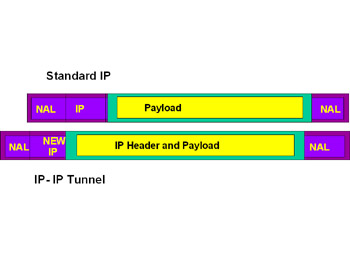
Figure 7.7: IP-IP Header
IP Security (IPSec)
The IPSec protocol was developed as a security standard for Internet traffic. It can operate in two modes: tunnel (see Figure 7.8a) and transport (see Figure 7.8b). In the tunnel mode, data encryption is not provided; however, in the tunnel mode data encryption is provided.
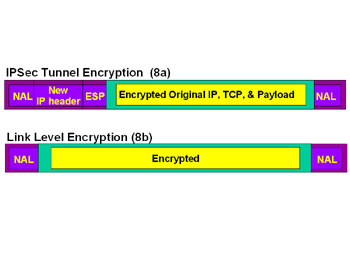
Figure 7.8: IPSec Frame
IPSec tunnel-mode tunnels have lower overhead and higher performance compared to running IPSec on tunnels created some other way; however, they are usable only for IP.
IPSec in transport mode offers a very powerful encryption algorithm to encapsulate IP data. In IPSec transport mode, endpoint addresses are encrypted. For a detailed explanation of IPSec, refer to RFC 2401.
Layer-2 Tunnel Protocol, Version 3 (L2TPv3)
The Layer-2 tunnel protocol (L2TP) has several versions; the version currently in use is version 3 (L2TPv3).
This protocol tunnels Layer-2 information across Layer-3 networks. L2TPv3 does not have built-in security, but can work with other VPN protocols, including IPSec.
As shown in Figure 7.9, the L2TPv3 header consists of a session ID and a cookie. Details on the L2TP can be found at RFC 2661.
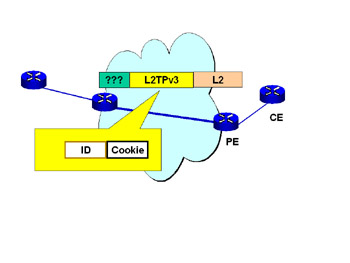
Figure 7.9: L2TPv3
MPLS Tunnels
MPLS is a tunneling and switching technology. The switched tunnels that MPLS offers provide for multiplexing or aggregation, QoS assignment, and traffic engineering. MPLS tunnels can be used standalone or in conjunction with the previously covered VPN tunnel protocols. There has been wide acceptance of MPLS with GRE tunnels.
MPLS offers a variety of VPN services that will be covered in greater detail further into the book. MPLS offers both end-to-end and edge-to-edge tunnels. Figure 7.10 illustrates MPLS with an end-to-end tunnel.
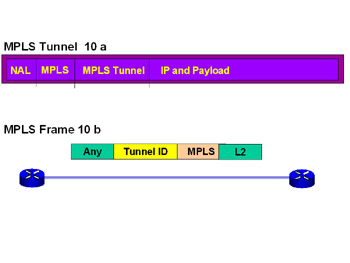
Figure 7.10: MPLS Tunnel and Frame
Now that we have briefly discussed several prominent tunnel methods, let’s look at the features of each in relationship to the other. Table 7.1 gives an overview of the tunnel protocols. Reviewing the table, we see that if it full security is needed, then IPSec might be the tunnel of choice. However, if multiplexing is needed, then L2TPv3 might be an alternative tunnel of choice.
| Features | GRE | IP-IP | IPSec | L2TP3 | MPLS |
|---|---|---|---|---|---|
| Encryption | N | N | In transport mode only | N | N |
| Authentication | Y | N | Y | N | N |
| Multiplexing | Y | N | N | Y | Y |
| QoS | N | N | N | Y | Y |
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 138