Understanding the Windows Access Control Mechanism
This section covers the high-level details of how the Windows operating system handles access control, including defining securable objects, security descriptors, ACLs, and access control entries.
| More Info | For more information about how Windows access control works, refer to http://msdn.microsoft.com/library/en-us/secauthz/security/access_control.asp . |
To determine the permission of a resource the Windows operating system needs to know the access level of the logged-on user and the permissions on the securable object. When a user logs on, the system creates an access token that contains the security identifier (SID) that identifies the user s account and all of the groups the user belongs to. The system uses the access token whenever it needs to determine the permissions for a securable object or perform a certain function that requires privileges.
What Is a Securable Object?
Objects are assets on a computer that a user can use. These objects can be used either directly, such as when a user attempts to open a file, or indirectly, such as when an application reads a registry key upon starting. If the system is able to limit the permissions or control on such objects, they are called securable objects . Examples of securable objects include the following:
-
Files and directories
-
Network shares
-
Named pipes
-
Registry keys
-
Processes
-
Threads
-
Windows services
-
Mutexes
-
Semaphores
-
Shared sections
-
Active Directory objects
-
Distributed Component Object Model (DCOM) objects
Securable objects have an associated security descriptor (SD), which is defined when the object is created.
What Is a Security Descriptor?
Security descriptors contain the security information for the securable object. Essentially, the security descriptor defines which permissions are granted for that object and can include the following information:
-
The owner and primary group of the object
-
The ACLs for the object
What Is an ACL?
A security descriptor can contain two types of ACLs:
-
Discretionary ACL (DACL) that determines the level of access to a securable object
-
System ACL (SACL) that specifies the audit policy for the securable object
Both can exist in a security descriptor, but it is the DACL that secures the resource from being accessed by unauthorized users, as shown in the following graphic:
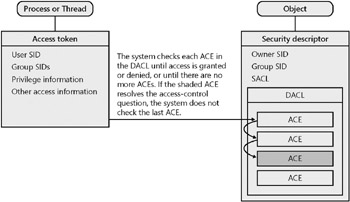
An ACL contains zero or more access control entries (ACEs). Although many operating systems have their own method of controlling permissions, the Windows operating system uses ACLs to determine the permissions a user or group has on an object.
| Important | Microsoft Windows 95, Windows 98, Windows Millennium Edition (Me), Windows CE, and Windows Mobile do not support the notion of ACLs. |
If the DACL of a security descriptor is set to NULL, referred to as a NULL DACL, no access control exists on the securable object ”meaning the object is not secure. NULL DACLs are discussed later in the chapter, but an object should never have one.
What Is an ACE?
An ACE describes who can do what. All ACEs contain the following information:
-
A security identifier (SID)
-
Access rights
-
Flag for the type of ACE
-
Flags that determine whether the ACE is inherited
As mentioned earlier, a SID is a security identifier that represents a user, group, or computer. The Windows operating system uses several well-known SIDs to represent different accounts ( http://msdn.microsoft.com/library/en-us/secauthz/security/well_known_sids.asp ). Because of the way a SID is constructed , no two SIDs are equal. Even if you delete a user named Bob and create a new user named Bob , the new account will have a different SID. Can you think of how this behavior can cause problems in an application? If an application relies on just the user name to make security decisions, it might be possible for the user name to be reassigned. As such, the new user with the reused user name will have permissions he or she should not have.
The access rights determine which operations can be performed on an object. For example, reading and writing to a file can be represented by the FILE_READ_DATA and FILE_WRITE_ DATA flags, respectively. Full Control can also be granted in an ACE, meaning that an account can do anything to the resource, such as read, write, delete, or even change the permissions. Not only can an ACL indicate which rights are allowed, an ACE can also deny access to a resource.
When creating an ACE, a flag can be set to determine how the system will propagate inheritable ACEs to child objects. Depending on the combination of inheritance flags, an ACE can be inherited by the container only, by the objects only, by both the container and objects, or by neither . For example, a directory can be considered a container and a file can be considered an object. If the directory has the CONTAINER_INHERIT_ACE and OBJECT_INHERIT_ACE flags set for an ACE, all child directories and files created under the parent directory will also inherit the ACE.
EAN: 2147483647
Pages: 156