Chapter 13: Finding Weak Permissions
When you were a child, you probably had to ask for permission to go outside, watch television, play a video game, and so forth. If you weren t granted permission, you couldn t do that activity. OK, so that might not always have been true, but you get the point. In application security, permissions limit who can access certain resources and what can be done to them. For instance, a file can have permissions set to allow Tom to read it and write to it, while everyone else is denied access.
In this chapter, we discuss how to find weak permissions on objects and how malicious users can take advantage of such security bugs to attack. Even though this chapter focuses mainly on systems that run the Microsoft Windows operating system, the concepts apply to other operating systems. Also, the Windows operating system is capable of protecting resources, such as files and registry keys, but applications might define more specific permissions for objects that cannot be protected by the operating system. An example is a peer-to-peer file sharing application: the application might use its own permissions to restrict who can connect to the client and which files it can share. In such cases, you should still look for weak permissions that attackers can take advantage of to compromise the security of the application.
Understanding the Importance of Permissions
To make sure a product is secure, you have to protect its resources and the operations it performs . Although it might seem like the concept of permissions is simple, permissions are a frequent source of security vulnerabilities ”it takes only a single mistake to enable your system to be compromised.
Setting incorrect permissions can lead to all types of attacks. Sometimes it is possible for an application to lead to an elevation of privilege (EoP) in which attackers are able to gain a higher level of access to the system than they should be allowed. For example, imagine an application that is running as a high-privilege user has a bug that allows arbitrary code to run. Attackers can take advantage of the flaw to elevate their privileges on the machine when executing malicious code.
Beware of multiple-stage elevation of privilege attacks. Often, when you are looking for permission problems in an application, you might not find a single bug that leads to a direct EoP to a high-privilege account. Instead, you might notice a slight EoP that seems harmless by itself. Do not be fooled by this falsity. An attacker can use this weakness to chain together multiple EoP attacks to achieve a higher level of privilege.
In the example shown in Figure 13-1, a piece of software allows Everyone to read and write to a registry key. This registry key specifies the path to a dynamic-link library (DLL) that was loaded by a service the software installed. The service runs as Local Service (a low privileged account), which loads the DLL. Because an attacker can control the registry key of the DLL path, the attacker can control the code that it runs (by pointing the registry key to an attacker-supplied DLL that contains malicious code). Normally, the service would then write properly formatted data to a directory that only Local Service and System (a high privileged account) are granted permission to access. Another process running as System could then parse any log files found in the directory. Because the attacker can run any code inside the malicious DLL, that attacker can write malformed files to the log directory. If there was buffer overflow in the parser for the log files, the attacker could chain the multiple stages together to run arbitrary code as the System account.
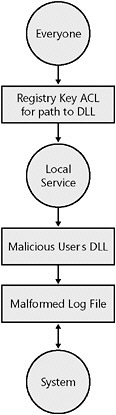
Figure 13-1: An example of a multiple-stage attack that elevates privilege to the System account
Although the developer might not have given much thought to how flaws in the parsing logic would affect the system because of the restrictive permission set, using this chaining technique could lead to an EoP attack. If you find a weakness in your permissions, do not make assumptions as to whether or not an attacker could take advantage of the weakness. The bug should be fixed so there is no question as to whether it allows an attack.
| Important | It is an important best practice always to run an application or Windows Service using an account with the least privilege, as well as to secure the permissions as much as possible on objects. Doing so helps protect against certain vulnerabilities by limiting what an attacker could access. For example, if there is a buffer overrun an attacker could exploit in a service running as Local System, the attacker would have Full Control of the system. However, if the service was running as an account with a lower privilege, the attacker would be limited to whatever the account s permissions are. Several viruses have spread because people tend to log on to the Windows operating system and run their programs with an administrator account. Microsoft Windows Vista helps with this problem by introducing the User Account Control (UAC) to distinguish between administrators and regular users. You can read more about the security improvements in Windows Vista by visiting http://www.microsoft.com/technet/windowsvista/evaluate/feat/secfeat.mspx . |
EAN: 2147483647
Pages: 156