Data Flow Diagrams
DFDs are extremely useful when you are attempting to find security threats against an entire application or pieces of it. Creating an accurate and reasonably complete DFD forces the software creator to have a clear understanding of the application and how all of the data moves between different components in the DFD.
The team on which Tom Gallagher and Lawrence Landauer, two of the authors, work performs security reviews for Microsoft Office products. Part of the team s role involves meeting with individual application teams within the Office organization, understanding what they are building, and giving them security advice. After the product team gives the security review team a brief explanation of what they are creating, the security review team looks at the DFD created by that product team. The DFD quickly clarifies exactly how particular software features work and how a user (or attacker) can interact with the feature. By studying the DFD, the security review team can begin to understand the product at a deeper level. This deeper understanding enables the team to uncover threats to the system more easily.
Figure 2-1 shows an example of a small Web application s DFD. The DFD represents a server application that allows a user visiting a Web page to click a link on that page and e-mail a copy of the page to other users, a feature we call the e-mail Web page feature, although it sometimes goes by other names . This functionality is common on news sites. The user can request that an e-mail message containing a brief note from the user and a link to a news article on the Web site be sent to an arbitrary e-mail address. Because the Web server doesn t record any identifiable information about the requester, the requester s actions are largely anonymous.
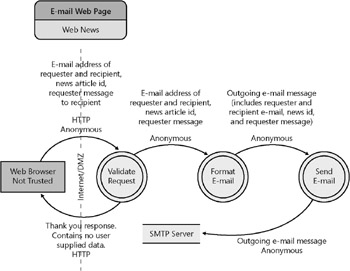
Figure 2-1: High-level data flow diagram for the functionality that enables a user to send a link to a Web page to a specific e-mail address
Figure 2-1 is a high-level and simple DFD. Often, more detailed DFDs are created to examine specific parts of the high-level DFD. Even with this high-level DFD, you have a much better idea of how the system works. Simply knowing some of the technologies that are used can enable you to identify some attacks that are relevant and that require testing in this application. Did you notice that the feature accepts anonymous Web requests with untrusted data? Can you follow the untrusted data through the application? Did you notice this feature sends e-mail to user-supplied addresses with user-supplied content by using Simple Mail Transfer Protocol (SMTP)? What else can you see based on this DFD? Can you spot any potential problems based on this DFD? We look at a few later, but before we do, let s look at ways an attacker might enter the application.
| Important | Many functionality testers would simply verify whether the application works from an end user s perspective. DFDs give testers a better understanding of how the application actually works. This understanding enables testers to develop more specific test cases tailored to the technologies used. For thorough security testing, this level of knowledge is imperative because attackers will take the time to understand the application at this level. |
EAN: 2147483647
Pages: 156