IPsec VPNs and the Cisco Security Framework
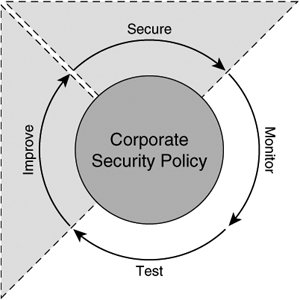
| Cisco's end-to-end security strategy is summarized comprehensively by the Cisco Security Wheel (illustrated in Figure 1-20). A corporate security policy should exist at the center of every end-to-end corporate security strategy. Cisco Systems builds solutions to comprehensively and securely enforce security policies in today's business environment. Figure 1-20. VPN Implementations and the Cisco Security Wheel This book explores many secure designs relying on IPsec for confidentiality, authentication, non-repudiation, and data authenticity. Those designs will incorporate many of the products that fit within various segments of the security wheel comprising Cisco's end-to-end security product line, including firewalls, intrusion detection systems, authentication, authorization and accounting (AAA) technologies, policy management, and, most importantly, encryption technologies. With respect to Cisco's overall security strategy, this book focuses on how the existence of IPsec helps to improve a corporate security policy and how IPsec can be deployed effectively to secure a network within the scope of that security policy. Note The security wheel is a common framework for developing a security policy. Cisco builds components enabling effective and comprehensive enforcements of all components of the security wheel. The Cisco Security Wheel is a component of the Cisco's SAFE architecture. For more information on SAFE, please refer to the following URL: http://www.cisco.com/go/safe |
EAN: 2147483647
Pages: 113
- Chapter I e-Search: A Conceptual Framework of Online Consumer Behavior
- Chapter III Two Models of Online Patronage: Why Do Consumers Shop on the Internet?
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter VII Objective and Perceived Complexity and Their Impacts on Internet Communication
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites