10.1. FTP Operation
| | ||
| | ||
| | ||
10.1. FTP Operation
FTP operation requires two software components : a client and a server. Any Telnet client can be used to connect to the server's port 21 and enter commands from the command line. But in these times of graphical interfaces, users desire more convenience than the command line can provide. My favorite FTP client for Windows is CyD FTP Client XP (available from www.cydsoft.com ). Its main window is shown in Fig. 10.1.
Figure 10.1: The main window of CyD FTP Client XP
If you urgently need to test the protocol but have no FTP client installed, you can use a simple browser for this, like Internet Explorer or Netscape. This is done by entering the address in the URL field in this format: ftp:// name :password@address . For example, you could enter ftp://flenov:mypassword@ftp.my_server.com or ftp://flenov:mypassword@192.168.77.1 .
FTP uses two ports for its operation: One port is used to transfer control commands, and the other is used to transfer actual data (files). The client program connects to port 21 and starts sending commands. This port is used by all users and the service that listens to the channel works simultaneously with several connections.
When a client requests data, another connection is opened for the specific user , over which the file is transferred. This is makes the programmer's work convenient, but it is in- convenient for the administrator, who has to configure the firewall.
Most FTP commands are similar to those used in Linux to work with files. This is because when the protocol was developed, the main network operating system was UNIX. Now we have Windows everywhere, but 20 years ago things were different.
10.1.1. FTP Commands
Listing 10.1 shows an example of a client program exchanging commands with an FTP server. Lines originating from the client start with the > character; those originating from the server start with the < character.
| |
< 220 Flenov Michael FTP Server > USER Anonymous < 331 Anonymous access allowed, send identity (e-mail name) as password. > PASS your@mail.com < 230 Anonymous user logged in. > PWD < 257 "/" is current directory. > TYPE A < 200 Type set to A. > PASV < 227 Entering Passive Mode (127,0,0,1,13,20). > LIST < 125 Data connection already open; Transfer starting. < 226 Transfer complete.
| |
The first line is the server greeting. It is issued right away to port 21. Most often, this line describes the server and its version. In this case, instead of a specific server name, I placed my name. A real server with the default configuration setting will display a line similar to the following:
220 flenovm.ru FTP server (Version wu-2.6.2-5) ready.
Why did I change the greeting text? I did so because by default it showed the domain name, the name and version of the FTP server, and the prompt message. Do you see anything dangerous in this information? I do: All hackers have to do for finding out what FTP server they are dealing with is to connect to port 21.
Their further actions are easy to predict. If I were those hackers, I would search all Bugtraq databases for information about bugs in the given version of the Washington University FTP daemon (wu- ftpd ) service. It is more likely than not that I would find some. Then the administrator of the server can only pray that I do not find exploits to take advantage of the discovered bugs or that the bugs discovered are minor and do not let anything serious be done with the system.
After the server displays the prompt, the client can start sending commands to it. But before this, the client has to introduce itself to the server. This is done by executing first the USER and then PASS FTP commands, specifying the user login and password as the parameter for each, respectively.
FTP servers allow operations with three types of authorization: real, guest, and anonymous. In the first case, you have to pass to the server the real login and password of a user allowed access to the server. After the USER command is executed, the server prompts you to enter the password for the specified user:
331 Password required for flenov.
When logging in as an anonymous user, the login is given as anonymous ( USER anonymous ). The server will answer with the following message:
331 Anonymous access allowed, send identity (e-mail name) as password.
The password to log in as an anonymous user is an email address. The address does not have to be a real one; the server cannot check this. Some servers do not even check the validity of the format of the entered email address, and any text can be entered as the password.
Anonymous user access gives minimal file and directory handling capabilities and is used only to access open file archives. The anonymous access is most often used to publish documents for public access using FTP. For example, software developers set up FTP servers with anonymous access to let users download the software updates or new software versions.
A real user can traverse the entire file system of the server, being limited only by the access rights of the user account chosen to connect to the server.
Guest login access rights are something between anonymous and real login access rights. A guest login has more rights than an anonymous login and it has rights to upload files, but unlike a real login, a guest can only work in its own directory. For example, if a guest is given access to the /home/robert directory, he or she can have full access to its files and subdirectories but will not be able to go above this directory. You can designate any name as guest.
Note that the password in the PASS command is sent in plaintext, which presents a serious problem. Every time some service is considered in this book, you run into the plaintext data transmission issue. It can't be helped now that nobody thought about hackers at the dawn of the Internet. Now you have to develop various methods to hide passwords.
If your server services only anonymous logins, it does not matter that passwords are sent in plaintext. With this type of authentication, any user can connect to the server by specifying any email address as the password. But these servers are only used to store public resources. When a server contains confidential information, access to it is through real password authentication. In this case, the password must be encrypted. You can do this using the stunnel program or SFTP, which was considered in Section 5.3.8 .
I saw an excellent solution on a public Web server about 10 years ago. To upload data onto the server, a user had to register by filling out a Web form with personal data. Afterward, the user would be issued a password valid for that session only. Files could only be uploaded into a special directory, which could only be written to. The permissions for the uploaded files were given only for read and write, not for execute. With this arrangement, the password can be transmitted in plaintext. Even if a password is intercepted, it cannot be used to log into the server again.
It is easy to implement a one-time password arrangement if your server uses PAMs (see Section 3.3.3 ).
After a successful login to the server, you can execute any FTP commands. However, there is a problem with this the command set depends on the server. All developers provide the main commands described in the Requests For Comments (RFC). But because the capabilities provided by the standard no longer meet today's requirements, Web server developers add their own functions, which may differ from one developer to another. Thus, if a client program does not behave as you would expect it to in some situations, it does not necessarily mean that there is something wrong with it; it simply may be incompatible with the server it is trying to communicate with.
The main FTP commands are listed in Table 10.1. They may be of use to you when working with Telnet or testing the server.
| Command | Description |
|---|---|
| USER login | Used to enter the login during the authorization procedure |
| PASS password | Used to enter the password during the authorization procedure |
| SYST | Returns the system type |
| HELP | Returns a list of available commands |
| LIST | Displays files and directories of the current directory |
| PWD | Displays the current directory |
| CWD directory | Changes the current directory to the specified one |
| TYPE type | Specifies the data transfer type: A for ASCII files, I for binary files |
| RETR file | Retrieves the specified file from the server |
| STOR file | Uploads the specified file to the server |
| ABOR | Aborts the last FTP command or data transfer |
| QUIT | Terminates the FTP session and exits |
10.1.2. Server Messages
The FTP server responds to the commands it receives with messages that provide information about the results of the command execution. Responses consist of a three-digit code followed by optional text. When a response requires more than one line, the code and the text parts are separated with a hyphen in the nonterminal lines and with a space in the terminal line.
You should know the meaning of the response codes to be able to determine the type of errors they indicate .
The meanings of the first and second digits of FTP server response codes are listed in Tables 10.2 and 10.3, respectively.
| Code | Description |
|---|---|
| 1 | The command has been launched successfully but has not terminated yet; the user has to wait for the command to terminate before issuing new commands. This type of response is given when executing lengthy operations (e.g., file transfer). Another response will be issued when the command terminates. |
| 2 | The command execution has been successful; the user can issue new commands. |
| 3 | The command execution has been successful, but another command is needed to complete the operation. These responses are given when executing operations involving several actions for example, during the authentication procedure, which takes two commands. A response code starting with 3 is issued after the USER command during a login authentication procedure. |
| 4 | Execution failed, but it may be successful if another attempt is made later. This response may be issued when the server cannot execute the command right away because it is busy executing another operation. |
| 5 | Execution failed. This response may be produced by incorrect command syntax or parameter specification. |
| Code | Description |
|---|---|
|
| A syntax error |
| 1 | A human-oriented help message |
| 2 | A connection establishing or terminating message |
| 3 | An authentication message |
| 4 | Not defined |
| 5 | A file system message |
Consider an example. Suppose that you see the following message from the server and are thinking about what to do next :
331 Anonymous access allowed.
Knowing what the code digits mean will help you handle this situation. The first digit, 3, tells you that the previous command was executed successfully but that another command is needed to complete the transaction. The second digit is also 3; that is, the response is an authentication message. When can this response be issued? Of course, after the login was entered. The FTP server is waiting for the password and has informed about this with the 331 message.
As you can see, minimal knowledge is sufficient to figure out what problem has arisen, and to solve it rapidly .
10.1.3. Transferring Files
Because FTP is intended to be used with different systems, two file transfer modes are supported: text (ASCII) and binary.
Suppose that you want to send a text file from a UNIX computer to a Windows computer. In UNIX, the carriage return ( <CR> , code 13) character is used as the end-of-line indicator. In Windows, two characters are used for this: <CR> and line feed ( <LF> , code 10). The transmitted file will not be quite readable, because all text lines merge into one because of the lack of <LF> characters.
Fig. 10.2 shows the contents of a sendmail.cf file transferred from a Linux server to a Windows server in the binary mode and opened in the Windows Notepad text editor. As you can see, it is difficult to make anything out of its contents, with the <CR> character printed as a rectangle instead of starting each line as a new line.
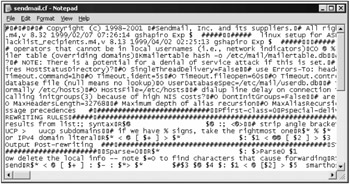
Figure 10.2: A text file transmitted in the binary mode
The end-of-line problem is solved by transferring the file in the ASCII mode. In this case, the text is transmitted line by line and the receiving operating system adds the necessary line-feed control characters itself. Fig. 10.3 shows the same sendmai.cf file transmitted in the ASCII mode. Its contents are easily readable now.
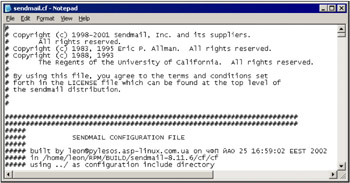
Figure 10.3: A text file transmitted in the ASCII mode
Binary files (such as images or music) must be transferred in the binary mode. In this case, it makes no difference under what operating system the file was created, because it will be properly recognized by any other operating system supporting this format.
If a binary file is transferred from Linux to Windows in the ASCII mode, Windows will replace all <CR> characters (which are a regular occurrence in binary files, although they do not indicate the carriage return operation) with the <CR>+<LF> character combination, and the binary file transmitted will become corrupted.
10.1.4. Data Channel Mode
As already mentioned, FTP operations require two ports: a control port and a data port. Port 21 is the control port, used to transfer FTP commands only. Files are transferred over another port. The process can be described as follows :
-
The client opens the port on the local computer, to which the server is to transfer the file.
-
The client sends a request to the server to download the file, and informs the server of the IP address and the port of the client computer, to which the download is to be performed.
-
The server makes a connection with the client computer and starts data transfer.
This mode, in which the connection is established by the server, is called active. The way the connection is established presents a problem. If there is a firewall installed on the client computer, it is most likely configured to prohibit any connections initialized from outside to prevent unauthorized access to the local network. Only a computer inside the firewall is authorized to establish the connection.
Thus, FTP will not work properly in the active mode if the client firewall is properly configured. If the firewall is configured to allow outside connections, it might as well be nonexistent because it no longer prevents unauthorized outside access.
This problem is solved by the passive FTP mode transfers. This is the default mode on most server and client FTP programs, because almost all modern operating systems have built-in firewalls.
In the passive mode, the connection is established somewhat differently:
-
The client asks to download a file.
-
The server allocates a port to be used for the ensuing data transfer and informs the client of the port number.
-
The client establishes a data connection with the specified port.
In this way, the server only opens its port and prepares to transfer the file; all connections are established by the client. This is more in line with the firewall rules.