The Common Language Infrastructure and Runtime
| The .NET Framework was designed to replace technologies such as COM (and its derivative ActiveX) and COM+. These technologies, while powerful, had many challenges, and with the emerging importance of the Internet, these challenges were proving too difficult to overcome. COM was a registry-intensive technology that only worked on Windows and that led to many configuration and installation problems. To use a COM component would require an installation, and the formation of several footprints within the Windows system registry that would allow the component to be referenced. It provided no sandbox for security after installationso once a component was installed, it could literally do anything. As a result, it became inappropriate for many Web applications and wasn't trusted by system administrators. The success of the Java Virtual Machine proved that a virtual machine at the desktop could have applications written to run on it, and these applications could be very easily distributed via a network or the Internet. As such, the architecture of a virtual platform is a natural method for running applications when the goal is easy and secure distribution. Thus the CLR was born. In the .NET world, the compilers generate a language called Microsoft Intermediate Language (MSIL) which is roughly analogous to Java bytecode. Regardless of the originating language, be it C#, VB.NET or J#, the MSIL that is produced for an application is consistent. At runtime the CLR manages this code, providing memory management, thread management and remoting, as well as enforcing type checking and other forms of code accuracy. As such, code that targets the CLR is referred to as managed code. The runtime can be hosted by other, unmanaged components whereby it is loaded into their processes to execute managed code. For example, the ASP.NET technology hosts the runtime to allow for a server-side technology that can provide managed server applications. This forms the core of the XML Web services technologies of the framework (discussed later). The architecture of the .NET Framework, including the positioning of the CLR, is shown in Figure 2-1. Figure 2-1. The .NET Framework architecture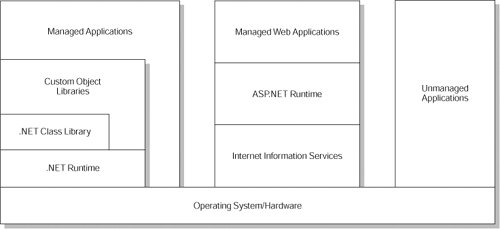 With regard to security, components are awarded trust credentials based on several factors, such as their origin (Internet, trusted network, or local computer), so a managed component works within a sandbox and may be restricted from operations such as file or registry access, even if it is being used within an application that has different security characteristics. This is termed as Code Access Security (CAS) and requires code to have the requisite permission or credentials to access system resources or other code. |
EAN: 2147483647
Pages: 170