Security QA
Security Q&AMany questions arise when you consider the security of Internet phone communications. Many of these issues have affected landline and cell phones for years, but they crop up in new and interesting ways when the Internet is involved. Let's discuss a few of these questions now. Note Although setting up a gateway for Internet security is beyond the scope of this book, good books are available to help with this task. For more information on the configuration of your gateway for VoIP, check out Chapters 4 and 6. Will VoIP open my network to intruders?Short answer? Probably not. Internet gateways are designed to open outbound connections to your VoIP provider on the demand of your TA. Attempts to communicate inbound without first being invited by the TA are not allowed. A properly configured gateway should appear as a black hole in the Internet, not responding to any attempts to access ports on the address held by the gateway (Figure 7.1). Figure 7.1. The results of a clean port scan of the author's network (image from grc.com)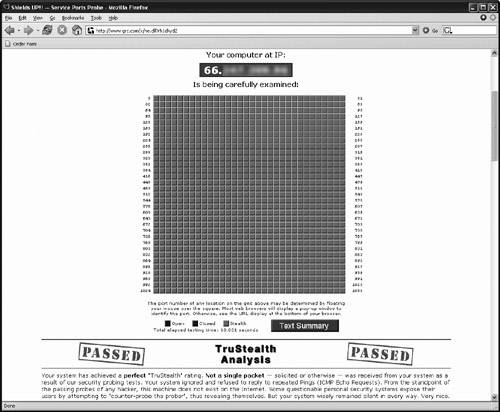 Can others eavesdrop on my phone calls?Once again, probably not. Not in real time, anyway. Most Internet services connect you and a relatively small number of local users to a router owned by your Internet access provider. When your communications reach your Internet provider, they travel across large backbone networks to your VoIP provider. The chance that anyone on those large networks would (or could) monitor your data is small. Of the users on your local node, anyone who would want to listen in must be able to capture and decode your VoIP packet stream not impossible, but beyond the ability of most of the general population. At this point, it comes down to who your neighbors are. Anyone who is that interested could just as easily place a tap on your demarcation point some dark night (Figure 7.2). It's a heck of a lot easier to tap the local line of your telephone company than it is to configure a sniffer to catch your VoIP calls. Figure 7.2. This $5 phone tapping device is available online. What other types of attacks are VoIP phones subject to?Those with too much time on their hands (crackers) have a number of attacks at their disposal that they can use to disrupt your Internet phone conversations. Notice that I say "disrupt." Though it may be difficult to listen in on a VoIP conversation, it is simple to break one up. Crackers can command vast armies of Internet bots computers that have been infiltrated with spyware and with programs that give crackers remote control, allowing them to direct traffic at specified Internet addresses. If your address is known to a cracker, he can use his bot fleet to swamp you with meaningless communications, effectively cutting off your ability to communicate with the rest of the Internet (Figure 7.3). This will definitely prevent you from using VoIP until the attack subsides. Figure 7.3. Victims of bot fleets can only wait for an attack to subside.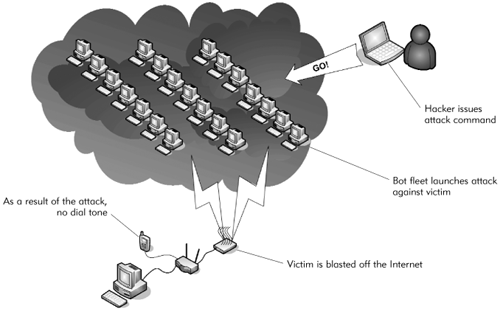 You might not even know you are under attack by a fleet of bots. You might think your Internet connection is simply down. If you do recognize the symptoms of an attack, you still might have difficulty persuading the support staff at your Internet provider to help. Although your provider can help you track down the source and block the attacks, that takes time and resources. By the time your provider has located the source, the cracker has usually lost interest and moved on to another victim. For this reason, it is sometimes best just to weather the storm. Can anyone steal my minutes?It is technically possible to craft communications that appear to come from your TA, enabling another party to access and use your VoIP minutes. This type of attack requires the attacker to know several things about you, such as your location, phone number, and IP address. Although these items can be sniffed from your communications, they require local access, and you will easily detect them when you see calls you did not make on your next bill. With this and any other type of attack, you have to consider the probability that an attacker will target you. For most of us, these types of attacks are not very likely. For those who cannot take that chance (such as CEOs and nuclear scientists), a solution like encrypted VoIP, provided by your company or Uncle Sam, would be in order. I use a wireless network. Is my VoIP secure?Much has been said about wireless network security. Recently, large strides have been made to secure wireless networks from the black hats. Today, you can buy a consumer-grade wireless network gateway that employs 802.11i (also known as WPA2) security. This level of security uses rotating encryption keys to scramble your communications. Taken individually, a single data packet captured off the air can eventually be cracked. Even if the key eventually becomes known to the hacker, by that time, it will have long since been changed. It is important to understand that these new encryption features apply only to devices released since the last quarter of 2004. Carefully read the specifications of your device to determine whether it supports 802.11i/WPA2. Older methods of encryption, such as WEP, have been cracked and are essentially no protection against a hacker who wants to see inside your network. Note Setup and configuration of 802.11i, WPA2, and WPA-PSK are too involved to deal with in these pages. For more information about these protocols, look for a book about wireless security. Make sure the book is a very recent one, as this field is always changing.
|
EAN: 2147483647
Pages: 94
