The TCPIP Protocol Suite
The TCP/IP Protocol SuiteThe Transmission Control Protocol/Internet Protocol Suite (TCP/IP) has become the de facto standard for the Internet, and most organizations use it for network communications. TCP/IP includes both network-communication and application-support protocols. As stated earlier, the TCP/IP protocol suite was developed and in use before the ISO/OSI model was developed and, as such, does not match directly with the layers of the OSI model. The TCP/IP protocol is defined as follows:
FirewallsA firewall is a device (hardware/software) that restricts access between networks. These networks might be a combination of an internal and external network (organization's LAN and the Internet) or might be within internal networks (accounting network and the sales network). A firewall is implemented to support the organizational security policy, in that specific restrictions or rules are configured within the firewall to restrict access to services and ports. If configured correctly, the firewall is the gateway through which all traffic will flow. The network traffic (or packets) then is monitored as it comes into the firewall and compared against a set of rules (filters). If the traffic does not meet the requirements of the access control policy, it is not allowed access and might be discarded or redirected. Firewalls started out as perimeter security devices and protected the organization's internal networks from external (such as, from the Internet) networks, similar to the way a moat was used to protect a castle. Often you will hear of this type of network security that "the network is hard and crunchy on the outside (perimeter firewall), and soft and chewy on the inside (organization's internal network). Perimeter security is an important component of a comprehensive security infrastructure, but it is not the complete answer. Perimeter security assumes that a vast majority of the threats are external to the organization, which is not always the case. It is important to keep in mind that the firewall can be considered a "choke point" on the network because all traffic must be checked against the rules before gaining access. As a result, the rules that are created for the network must take into account performance as well as security. Firewalls can filter traffic based on a variety of the parameters within the packet:
The level of granularity and types of rules that can be implemented vary among vendors. As an auditor, you will find that a wide variety of parameters can be configured, based on vendor implementation. A number of risk indicators are associated with firewalls:
Packet-Filtering FirewallsThe first generation of firewalls is known as packet-filtering firewalls, or circuit-level gateways. This type of firewall uses an access control list (ACL) applied at OSI layer 3. An ACL is a set of text-based rules on the firewall that the firewall can apply against incoming packets. A simple access control list could stipulate that all packets coming from a particular network (source address) 192.168.0.0 must be denied and discarded. In this instance, the firewall might have a text-based rule DENY ALL 192.168.0.0. Another type of rule might state that all packets trying to access a particular port, such as a web page request (port 80), be routed to a particular server, in this case, 172.168.1.1. In this instance, the firewall might have a rule that looks like PERMIT FORWARD ALL TCP Port 80 172.168.1.1. Packet-filtering firewalls can compare the header information in packets only against their rules. As a result, they provide relatively low security compared to other options. The creation of rules in packet filtering involves both permit (or allow) and deny (or block) statements. Permit statements allow packets to be forwarded; deny statements discard the packet. Access lists are sequential: Statements are processed from the top of the list down until a statement condition that matches a packet is found. When the statement is found, no further statements are processed. As an IS auditor, you should review the access lists for completeness and correctness. This example shows both a correct and an incorrect access list: Access list A (correct): access-list 1 permit host 192.168.32.1 access-list 1 permit host 192.168.32.2 Access list B (incorrect): access-list 1 deny 192.168.32.0 0.0.0.255 access-list 1 permit 192.168.32.1 access-list 1 permit 192.168.32.2 access-list 1 deny 192.168.40.0 0.0.255.255 In this scenario, we want to permit two IP addresses access to the internal network while denying the remainder of the subnet. In access list A, we allow both 192.168.32.1 and 192.168.32.2 to access the network. By default, routers and firewalls that can be configured to filter based on IP source or destination addresses deny traffic by default, and will not allow traffic unless it has been explicitly permitted. This default characteristic is referred to as the "implicit deny" statement at the end of every access control list. The list will be read in sequence from top to bottom, and because of the implicit deny statement at the end of the access list, any IP addresses that do not meet the criteria of the rules will be denied. In access list B, we are denying the entire subnet of 192.168.32.0, which includes 192.168.32.1 and 192.168.32.2. Because the first statement in access list B would technically match hosts 192.168.32.1 and 192.168.32.2, the later permit statements meant for these hosts would not be processed, and the packets from these source hosts would be discarded. Granular statements must precede global statements. The last rule in access list B is redundant with the first rule in the access list. Because no valid permit statements exist in access list B, no traffic from any source will be permitted due to the implicit deny statement at the end of every access list.
Improper configuration of traffic rules or access lists is the most common and critical error in firewall implementations. Stateful Packet-Inspection FirewallsStateful packet-inspection firewalls are considered the third generation of firewall gateways. They provide additional features, in that they keep track of all packets through all 7 OSI layers until that communication session is closed. The first-generation packet-filtering firewalls receive a packet and match against their rules; the packet is forwarded/discarded and forgotten. Remember from the discussion of the OSI model that a single communication (such as sending an email) can be broken down into several packets and forwarded to the receiving station. A stateful firewall is a bit more sophisticated because it tracks communications (or sessions) from both internal and external sources. A first-generation packet-filtering firewall can be set up to deny all packets from a particular network (as in the previous example), but a stateful firewall with the same rules might allow packets from that denied network if the request came from the internal network. Proxy FirewallsProxy firewalls, or application-layer gateways, are used as the "middlemen" in network communications. The difference between a proxy-based firewall and packet filtering is that all packets passing to the network are delivered through the proxy, which is acting on behalf of the receiving computer. The communication is checked for access authorization according to a rulebase, and then passed to the receiving system or discarded. In essence, a proxy impersonates the internal (receiving) system to review packets before forwarding. Any communication that comes from the receiving computer is passed back to the proxy before it is forwarded externally. The actual process that takes place is that the proxy receives each packet, reviews it, and then changes the source address to protect the identity of the receiving computer before forwarding. Proxies are application-level gateways. They differ from packet filtering in that they can look at all the information in the packet (not just header) all the way to the application layer.
An application-layer gateway, or proxy firewall, provides the greatest degree of protection and control because it inspects all seven OSI layers of network traffic. The firewall architecture for the organization depends on the type of protection the organization needs. The architecture might be designed to protect internal networks from external; it might be used to segment different internal departments and might include packet filtering, stateful packet inspection, proxy/application gateways, or a combination of these.
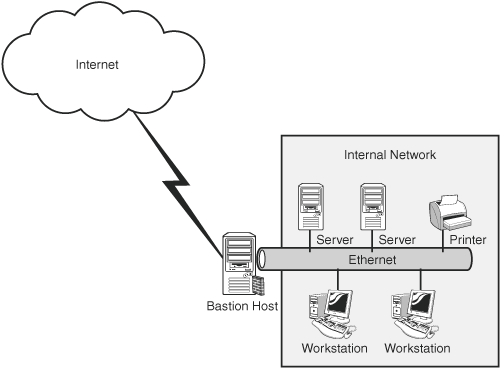
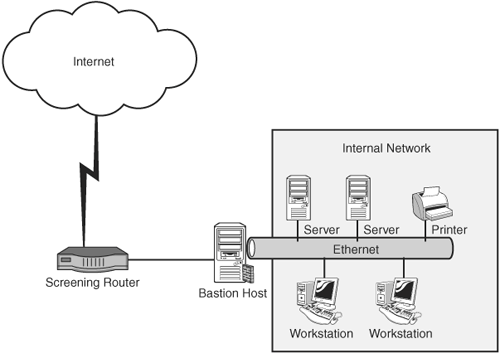
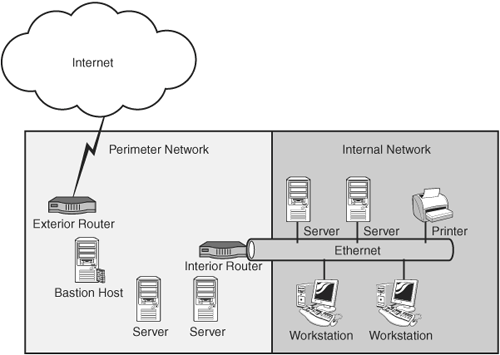
Securing an internal network from external threats requires a firewall to be situated at the perimeter of the network, acting as a gateway for communication between all internal hosts and servers (SMTP, web, and FTP) and external hosts. In general, there are three basic types of firewall configurations:
Layering perimeter network protection by configuring the firewall as a screened host in a screened subnet behind the bastion host provides a higher level of protection from external attack. Firewall architecture is quite varied. The organization might decide on hardware- or software-based firewalls to provide network protection. In the case of software-based firewalls, it is important to remember that they will be installed on top of commercial operating systems, which may have their own vulnerabilities. This type of implementation requires the IT organization to ensure that the operating system is properly locked down and that there is a process in place to ensure continued installation of security patches. Any unnecessary services or applications, as well as unneeded protocols, must be removed or disabled from the operating system. Because the objective of a firewall is to protect a trusted network from an untrusted network, any organization that uses external communications must implement some level of firewall technology. The firewall architecture should take into consideration the functions and level of security the organization requires. Firewalls are potential bottlenecks because they are responsible for inspecting all incoming and outgoing traffic. Firewalls that are configured at the perimeter of the network provide only limited protection, if any protection, from internal attacks; misconfigured firewall rules could allow unwanted and potentially dangerous traffic on the network.
Installing firewall software onto an otherwise robust and fully functioning operating system poses a greater risk of firewall compromise. To mitigate this risk, firewall software is often installed onto a system using an operating system that has very limited functionality, providing only the services necessary to support the firewall software. |