| The combination of organizational structure, policies and procedures, and best practices that are implemented to reduce risk is called internal controls. Internal controls are used by the organization to provide a reasonable assurance that the business objectives will be met and risk will be prevented, detected, or corrected. Preventative control objectives detect problems before they arise, monitor both operations and inputs, and prevent errors, omissions, or malicious acts from occurring. Using an access-control system (think user/password combination) is an example of a preventative control. Detective controls are used to detect and report the occurrence of an error, omission, or malicious act. Using audit trails is an example of a detective control. Corrective controls minimize the impact of threat, identify the cause of a problem, and modify the system to minimize future occurrences of the problem. Using a rollback facility in a database environment is an example of a corrective control. When evaluating the collective effect of preventative, detective, or corrective controls within a process, an IS auditor should be aware of the point at which controls are exercised as data flows through the system. Internal controls operate at all levels of the organization and should be continuously monitored to ensure their effectiveness. The auditor should be primarily concerned with the overall strength of the control or combination of controls to ensure that it meets its stated objective. Control procedures can be manual or automated and generally fall into three categories: Internal accounting controls Primarily used in accounting operations. They apply to safeguarding the assets and reliability of financial data and records. Operational controls Used in day-to-day operations to ensure that the operation is meeting business objectives. Administrative controls Used to ensure compliance with management policy.
As an example, access controls are implemented to ensure confidentiality, integrity, and availability of information systems and their associated data. Confidentiality is the assurance that the information will not be disclosed to unauthorized individuals, programs, or processes. Integrity ensures that the data is not altered in an unauthorized way. Availability ensures timely access to information by authorized users, programs, or processes. Table 1.4 identifies specific controls, how they are implemented, and their classification (preventative, detective, corrective). Table 1.4. ControlsArea | Transaction Type | Control Objective | Control Activity | Audit Procedure | Class | Method |
|---|
Information systems operations | Safeguard IT systems | Network access is restricted to authorized users and restricts unauthorized activity | Examine access policy. Users must fill out a system authorization form and be granted access by IS management. | Gather and review samples of the system operations form. Compare the form to identify users who have current access and current employees of the organization. | Preventative | Manual | | | | | IS management verifies users with access to a department listing provided by department managers, to ensure that access is appropriate and accurate. | Review previously completed access verification audit results, and determine that appropriate IS management approval was obtained and that exceptions were properly resolved. | Detective | Manual | | | | | Audit logging is enabled for both successful and unsuccessful access, and access to the logs is restricted to IS management. | Compare access logs against a list of current employees and users, and determine whether there are patterns of unsuccessful access (password guessing) or successful access during inappropriate hours or from unauthorized systems or networks. | Corrective | Manual |
Internal control objectives define the desired purpose or desired outcome associated with the implementation of the control. Table 1.5 outlines control objectives, their associated activities, and the audit procedures. Table 1.5. Example of a Control MatrixControl Objectives | Control Activities | Audit Procedures |
|---|
1. Independent Management Reviews | | Management should perform periodic independent reviews (including internal and external audits) of IT operations, to ensure that policies and procedures have been implemented and are working effectively. | Management establishes a schedule for periodic independent reviews of the IT operations. Management establishes formal follow-up procedures, to ensure that identified deficiencies are addressed in a timely manner. | a. Evaluate IT's policies and procedures, internal review schedules, and so on, to determine whether they provide periodic independent reviews of the IT operations and follow up on identified deficiencies. | 2. Organization | | | Duties and responsibilities should be adequately segregated so that no one person can perpetrate and conceal material errors or misstatements. | Management ensures that duties and responsibilities are segregated within the information systems department, to avoid perpetration and concealment of errors. | a. Evaluate the organization structure to determine whether the information technology (IT) department reports at a high enough level to allow it to act independently.
This procedure does not evaluate the existence of the control activity described in the same row. A more appropriate audit procedure is to review the organizational structure, review the job descriptions within the IT department, and evaluate whether duties are adequately segregated. | 3. Software Acquisition, Development, and Modification | | System and application software should be consistent with management objectives, should operate within specifications, should be tested before implementation, and should not be susceptible to unauthorized modification. | Management establishes and maintains a standard development methodology that contains the following control elements: • Written requirements/specifications reviewed and approved by application users and management • Participation of appropriate user and management personnel throughout all phases of software acquisition, development, and modification • Documentation for all software programs, including purchased software and modification to existing software • Validation, verification, and testing by management and information systems personnel, to determine that software operates in conformity with design specifications and meets user requirements • Final written approval from management, users, and information systems personnel before implementation | b. If the preliminary risk assessment indicates that further audit effort is necessary, examine at least one recent major software acquisition, development, or modernization project to determine the following: (1.)Whether written requirements and specifications were reviewed and approved by applicable users and management (2.)Whether appropriate IT user and management personnel participated throughout all phases of the software acquisition, development, or modification (3.)Whether all software programs, including purchased software and modifications to existing software, are documented (4.)Whether validation, verification, and testing was performed by management, users, and IT personnel, to determine that the software operates in conformity with design specifications and meets user requirements (5.)Whether final written approval from management, users, and IT personnel was obtained before implementation |
The first step in aligning IT with an organization's corporate goals is having and working on an appropriate level of planning. The IT department should have long-range (three- to five-year) and short-range (one-year) plans. These plans should provide specific solutions that ensure the growth and profitability of the organization, as well as identify both internal and external opportunities and controls that meet the organizational objectives. Establishing a sound IT management methodology through sound project management and IT organizational policies ensures that organizational goals are fulfilled and business risks are reduced. IT managers must define roles and articulate the value of the IT function. The roles and responsibilities must have clearly defined job descriptions and authority levels, and must incorporate proper segregation of duties. A high-level steering committee should be formed to ensure that the IS department closely supports the corporate mission and objectives: The committee should include various senior managers representing all organizational business areas. Duties and responsibilities should be defined in a formal charter. The committee should not become involved in routine operations. The committee should monitor major projects and the status of IS project plans and budgets; establish priorities; approve policies, standards, and procedures; and monitor overall IS performance. The committee should act as a liaison between the IS department and user departments. Formal minutes of the IS steering committee meetings should be maintained to document the committee's activities and decisions, and to inform the board of directors of IS activities.
IS structures reflect the requirements of the organization. Figure 1.3 outlines a common structure to provide you with a definition of roles, responsibilities, and job types. Figure 1.3. IS audit structure. 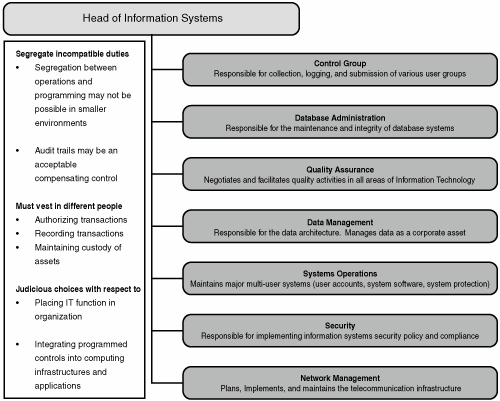
|
