Market
Market
There is a large market potential for collaborative applications, and peer-to-peer models will probably comprise a portion of this overall market. The Aberdeen Group and AMR Research expect corporate spending on collaboration software to triple from $10.6 billion in 2001 to $33.2 billion by 2004. Collaborative processes represent one of the three fundamental requirements for conducting electronic business: content, commerce, and collaboration. In this market section, we'll look at the evolution of the peer-to-peer computing market and several of the major players and standards initiatives in the space. These include initiatives such as SETI@home and various projects from Intel and Sun Microsystems. We'll also look at some of the drivers for adoption of this computing model within the corporate world and profile a company named Groove Networks, one of the startup companies in the field of peer-to-peer collaboration.
Evolution
Peer-to-peer technologies have evolved as an additional architectural solution for distributed computing where multiple networked computers are applied to solve a certain business task. They allow intelligent client computers to be connected to share computing resources in terms of files, processing power, and storage space. The Internet and the World Wide Web were originally a collection of computer servers linked together and operated in a client-server manner with information such as Web pages and other documents stored centrally and delivered upon request to client desktops. This request-response paradigm was a natural continuation of centralized mainframe technologies and client-server computing technologies. In all these scenarios, the bulk of the intelligence and control resided at the core of the network at the computer servers. The servers held the data and the business logic and the client machines simply made requests and rendered the content on screen. As the Internet has expanded and an ever-increasing number of devices such as desktops, personal digital assistants, cell phones, pagers, and other smart appliances and objects have been connected, the opportunity has arisen for any device to communicate with any other device and share their resources and information directly without going through a central point of control. A personal computer on the Internet may connect with another personal computer on the Internet, or even with a wireless device. The collective processing power or storage capability can be leveraged between peers as opposed to relying on a centralized server which must handle all requests and scale accordingly as usage increases.
Some of the early landmarks in the evolution of peer-to-peer computing were the peer-to-peer local area networks (LANs) such as Microsoft Windows for Workgroups, Novell Personal NetWare, and IBM peer-to-peer SNA networks running their Advanced Peer-to-Peer Networking (APPN) protocols. All these company examples allowed users on local area networks to share resources on their computers and to access the shared resources of others on the network. More recent and well-known examples of peer-to-peer computing have included the SETI@home project, Napster, Intel's peer-to-peer initiative, and Sun's Project JXTA.
SETI@home is a UC Berkeley program that allows regular Internet users to become involved in the analysis of data collected as part of the SETI sky survey at the National Astronomy and Ionospheric Center's radio telescope in Arecibo, Puerto Rico. SETI is a scientific program seeking to detect signs of intelligent life outside the planet Earth. Internet users can use their spare computing power, when their computers are not in use, in order to process portions of data collected from the telescope. The data are sent to end users' machines as one-quarter megabyte "work-units." Once these work units are processed by the peer computer, the results are sent back to the SETI@home program for merging in a database with the results from other peer computers on the network. The SETI@home program connects only to peer computers in order to transfer data. End users simply download a special screen saver program that contains the logic to perform the file transfers and processing when the local machine is left unattended. The number of users and the total CPU processing time collected by the program are impressive. As of the time of this writing there were over 3.5 million end users engaged in the program over time with a collective CPU processing time of nearly 900,000 years. In terms of computing power, the program has exceeded the rating of IBM's "ASCI White" supercomputer in terms of floating-point operations per second at less than one percent of the overall cost. It has obtained 15 TeraFLOPS (1012 floating-point operations per second) as opposed to IBM's rating of 12 TeraFLOPS at a cost of $500,000 compared to $110 million for the IBM machine.
Intel Corporation's involvement in peer-to-peer computing has included the formation of the Peer-To-Peer Working Group, the Peer-to-Peer Trusted Library (PtPTL), and the Intel Philanthropic Peer-to-Peer Program. The Peer-To-Peer Working Group was formed in August 2000 to foster standards and protocols for peer-to-peer computing. The group is comprised of member companies such as Intel, Fujitsu PC Corporation, Groove Networks, Hewlett-Packard, Hitachi Ltd., J.D. Edwards, NextPage, OpenCola, and O'Reilly & Associates. The working group has released best practices related to issues such as firewall traversal, taxonomy, security, file services, and libraries. The Peer-to-Peer Trusted Library is an open-source developers' toolkit for peer-to-peer security released by Intel that is tailored for the creation of peer-to-peer applications. It supports digital certificates, peer authentication, secure storage, public key encryption, digital signatures, and symmetric key encryption all important elements in helping to make peer-to-peer computing a trusted infrastructure for corporate developers.
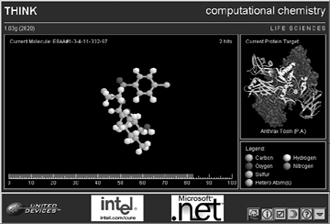
The Intel Philanthropic Peer-to-Peer Program was announced in April 2001 to help combat life-threatening diseases, such as cancer and Alzheimer's, by using personal computer processing power in a distributed network environment in a similar manner to the SETI@home program. Additional members of the program include the American Cancer Society, the National Foundation for Cancer Research, the University of Oxford, and United Devices Inc. The number of personal computers participating in the program is more than one million, with more than 700 million hours of processing time already completed to date. One of the programs available to end users is the United Devices Anthrax Research Program designed to help develop drugs to render anthrax ineffective as a lethal disease or weapon even after antibiotics have been unable to stop the progression of the disease. From an end-user perspective, the research programs present software that can be downloaded and run on a variety of personal computer operating systems, taking advantage of unused processing cycles. When running on a desktop computer, the programs either appear as a screensaver or run in the background with no screensaver apparent. The programs are available from the Intel Web site, www.intel.com/cure, and are free downloads that are easy to install and run. They typically consume about 50 percent of the free CPU cycles on a computer. The program is fun for end users since it allows them to view the computing statistics of the ongoing program such as top ranked members by processing time contributed and by geography. Users who select the screen saver, as opposed to the background process, can also view graphics showing the current computing tasks being performed on their computers. For example, the THINK-Anthrax project shows graphics representing the modeling of the interaction between drug candidate molecules and a component of the Anthrax toxin. Figure 3-1 shows a sample screen from this program.
Figure 3-1. Screen Saver from the United Devices Anthrax Research Program Showing Current Processing Activity. Source: United Devices.
JXTA was announced by Sun Microsystems in April 2001. It is an open-source initiative for the developer community that aims to provide a set of open, generalized peer-to-peer protocols that allow any connected device on the network to communicate and collaborate with any other. Connected devices may include personal computers, servers, personal digital assistants, and cell phones, among others. The project started as a research project incubated at Sun with guidance from Bill Joy, Sun's chief scientist, and others. Source code for developers is posted at the JXTA Web site at www.jxta.org. The code provides three layers of service: a core layer, a services layer, and an application layer. It provides protocols and building blocks for discovery of peers, transport of content through firewalls, creation of peers and peer groups, generic services for searching, sharing, and security, and finally, application level services for file sharing, resource sharing and distributed storage. The JXTA project supports Java as the initial programming language, and, like the Peer-to-Peer Trusted Library, it is helping to advance standardization and ease of development of peer-to-peer business applications that require solid technical underpinnings.
Drivers for Adoption
Some of the drivers for adoption of peer-to-peer computing have included the rapid increase in the number of personal computers, the increase in their computing capabilities in terms of processing speed, cache, and disk storage, and the increase in readily available broadband networks. The visibility of peer-to-peer business models in the consumer world via companies such as Napster for music sharing was another driver for overall adoption and acceptance because of increased awareness. The promotion of peer-to-peer computing via companies such as Intel and Groove Networks has helped to focus attention on the possibilities for its application within the business world. The increasing computing power at the "edge" of the network has opened opportunities for distributed peer-to-peer computing for the processing of large compute jobs that can be executed in parallel on multiple workstations. The increased volume of information and content on the Internet and within the business environment has also opened opportunities for distributed file sharing and other forms of content sharing. Finally, the increased focus on cost reduction and productivity improvements for knowledge workers has served as an additional incentive for increased adoption of peer-to-peer computing for group collaboration for working on projects or meetings with minimized travel requirements. Standards organizations and best practices such as the Peer-to-Peer Working Group and the Peer-to-Peer Trusted Library have helped to reduce the technical barriers for adoption in terms of providing solutions for some of peer-to-peer's challenges such as confidence in the security model.
Value Chain
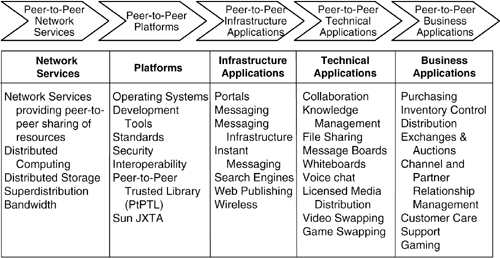
Figure 3-2 shows a high-level value chain for peer-to-peer computing. As with other technologies, peer-to-peer computing spans the entire computing "stack" from the infrastructure level to the application level. At the infrastructure level, network-based services help to enable peer-to-peer sharing of resources such as distributed computing, distributed storage, and "superdistribution." Superdistribution allows files such as antivirus updates to be distributed to end users using the peer-to-peer network instead of requiring all downloads to occur from a central location. The platform portion of the value chain includes vendors who provide development tools and low-level tools that support peer-to-peer security and interoperability standards. The infrastructure applications portion of the value chain is closely related and includes software for managing functions such as messaging, searching, and publishing using peer-to-peer techniques. The final two value chain elements include technical, or horizontal, applications that support a variety of collaborative functions and business applications that support specific vertical industry functions.
Figure 3-2. Value Chain for Peer-to-Peer Services.
Vendor Profiles
As mentioned earlier, the concept of peer-to-peer computing, while in existence for many years in the form of local area networking products, was further popularized by Napster in the consumer space with their file-sharing community for the exchange of media files. It is now becoming an increasingly important technology within the enterprise. Peer-to-peer basically leverages computers on the network "edge" (desktops) instead of centralized servers for performing various content and collaborative functions. One of the major players in this field is Groove Networks, a company whose product lets groups create workspaces to share files, use message boards, mark up virtual whiteboards, engage in instant messaging, have voice chat sessions, and much more. Groove Networks was founded in 1997 by Ray Ozzie, one of the original creators of Lotus Notes in the mid-1980s.
Peer Services ExampleGroove Networks www.groove.net Groove Networks, based in Beverly, Massachussetts, is one of the major vendors in the peer services arena. The company was founded in October 1997 by Ray Ozzie, the initial creator of Lotus Notes. Groove's product is a collaborative peer-to-peer technology that incorporates most communications technologies such as live voice chat over the Internet, instant messaging, text-based chat, document-sharing, threaded discussion, and many other tools. The company has received $117 million in funding from investors such as Microsoft, Accel Partners, and Intel Capital. The company targets a variety of industries and functional areas such as product design and development, purchasing, inventory control, distribution, exchanges and auctions, channel and partner relationship management, and customer care and support. Scenarios can also include disaster aid management, e-commerce, negotiation, merger and acquisition, pharmaceuticals, higher education, and financial services. One of the most interesting aspects of the Groove platform is that it is based upon a peer-to-peer architecture using XML-based technology. The platform acts as a client-side or "personal portal." End users download and install the Groove client on their desktops and are able to create their own "shared spaces" and invite others to join. They can select from a variety of tool sets to place into the shared space such as a calendar, contact manager, discussion, files, notepad, or Web browser. A conversation tool allows end users to engage in live voice chat that runs over their standard IP network connection. Joint activity tools allow cobrowsing of Powerpoint presentations and coediting of Microsoft Word documents. The Groove software also tracks who is online and who is active within a shared space. Beyond the collaborative functionality, some of the platform features that make Groove suitable as a robust business tool include its ability to automatically traverse enterprise firewalls by tunneling using standard Internet communication protocols, to encrypt data both over the wire and on disk to keep data confidential, and to provide an open application programming interface for custom enhancements. The platform also supports online and offline usage and synchronizes with other peers when reconnected. Groove's customers include GlaxoSmithKline and Unilever. |
EAN: 2147483647
Pages: 81