Protecting Yourself from Internet Attacks
If your computer is connected to a network, then by definition other computers on that network can communicate with your computer. If your network is connected to another network (that is, if it's part of an inter-network), then your exposure is potentially greater. If your computer is connected to the Internet, then it is connected to the world's largest inter-network and your exposure to potentially naughty people is about as big as it gets.
The default configuration for Mac OS X is reasonably secure from Internet attacks. Nonetheless, it is helpful to have a basic understanding of the security risks of connecting to the Internet and of how to protect your machine from attack.
If your machine is connected to the Internet, it may be exposed to unauthorized and malicious people attempting to gain control of it or to harm it in some way. We say "may be" because some ways of connecting your machine to the Internet do not expose it to attack, and there are things you can do to configure your machine to reduce its exposure.
Every machine connected to the Internet has either a public or private IP address.
Some IP addresses are actually not part of the public Internet. These addresses (known as private addresses ) are used by networks that are, well, private, and not accessible to machines on the public Internet. A machine with a private IP address may still be (indirectly) connected to the Internet. See the sidebar "Connecting to the Internet with a Private IP Address."
On the other hand, if your machine has a publicly reachable IP address, then machines anywhere on the Internet can attempt to initiate connections to it. Basically, they can knock on the door, but they only succeed in making a connection if your machine is "listening" for the type of connection being attempted. For example, if you have activated Web sharing, then other machines can connect to the Web server software running on your machine.
Packet-sniffing attacks
Packet-sniffing attacks are the most insidious type of attack you are likely to deal with. In a packet-sniffing attack, a sniffer program running on a computer examines all the data flowing on that machine's local network. This makes all the unencrypted data on that network easily available for examination: user names , passwords, credit card numbers , medical histories, you name it. Any data whatsoever that is traveling unencrypted on a network is open for examination via a packet sniffer.
There are legitimate uses of packet sniffers, primarily having to do with diagnosing networking problems, so the mere existence of a packet-sniffer program doesn't automatically mean that someone is attacking your system or network, but it is certainly something to be concerned about.
To run a packet sniffer, though, one must have full control over the machine on which it is run. On a Unix machine, that means having root access. But a user running a Mac OS 9 or Windows machine can also run packet sniffers. (The packet sniffer needs to be able to alter settings in the network interface cardthe Ethernet adapterto put it into promiscuous mode, in which it reads every packet of data passing by on the wired or wireless network.)
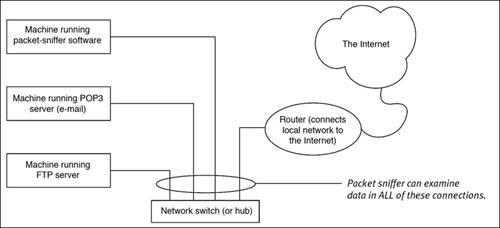
Using easily available tools (see the sidebar "Packet Sniffers and Port Scanners"), it is possible to grab user names and passwords that are being sent over the local network between machines. Figure 12.1 is a diagram of a typical local area network (LAN) connected to the Internet. The packet sniffer could be on your local network, or on a network where someone is connecting to a server on your network. In either case, the sniffer will be able to obtain unencrypted passwords (and other information) that is being sent to your server. So if you are running any services on your machine that use unencrypted passwords for access, it is possible that a user account on your machine could get sniffed, and then the attacker could log in to your machine and cause further mischief.
Figure 12.1. Diagram showing a typical LAN connected to the Internet and the reach of a packet sniffer.
What an Attack on IIS Looks LikeIf you turn on Web sharing (in the Sharing pane of System Preferences), and if your machine is connected to the Internet with a publicly accessible IP address, you can almost be certain to see entries in the server log file ( /var/log/httpd/access_log ) that reveal attacks directed at Microsoft's IIS server software. A typical attack will show up in the Web server log as 66.169.207.82 - - [13/Jul/2005:07:59:19 That line shows an attack originating from the machine with the IP address 66.169.207.82 on July 13, 2005, at 7:59 GMT. The attack attempted to run a program called cmd.exe . The Web server returned a "Page Not Found" code (404), and the attack had no effect besides using up a bit of bandwidth and creating a log entry. On the other hand, had this machine been running Windows NT with an unsecured version of IIS, the attack might have succeeded in gaining control of the machine. Seeing a dozen or more of these attacks every day is quite common. |
One defense against packet sniffing is to not run any services that allow login via unencrypted passwords (for example, not running a Telnet or FTP server). In the real world, however, you may need to run some services that use unencrypted passwords. Most e-mail programs use either the POP or IMAP protocol to collect a user's e-mail from the mail server, and the passwords are sent over the network without encryption. If you find yourself running a POP or IMAP server, you should consider setting each user's account so that he or she cannot log in and get a shell prompt from the machine. You might set all the IMAP users to have a login shell of /usr/bin/false , which allows them to use IMAP to collect their e-mail but not use the same user name and password to log in and get a shell prompt. That way, even if an IMAP user's password is sniffed, the attacker cannot use it to get a shell prompt and attempt further attacks from the "inside." (Review Chapter 11 for more on how to change a user's login shell.)
Attacks on services
Most attacks against a machine via the Internet occur when an attacker connects to a service running on the target machine and exploits a security hole in that service. For example, there may be a security weakness in Postfix, a program that provides e-mail services. An attacker might connect to the e-mail server on your machine and then attempt to exploit the security vulnerability.
The exact method of each attack is different, depending upon the exact security hole being exploited.
One common type of attack is called a buffer-overflow attack. In situations where software has a buffer-overflow vulnerability, that vulnerability can be exploited by an attacker who sends the target software more data than it was designed to handle. If the target software is vulnerable, a portion of memory the target is using gets overwritten by the excess data. The excess data occupies a part of the target's memory where legitimate commands are supposed to be, only now the data may be commands that were supplied by the attacker. Of course, well-designed software doesn't allow this, but sometimes such vulnerabilities exist and are exploited.
Other attacks, known as denial-of-service (frequently abbreviated DoS ) attacks, seek to overload a server with more requests than it can handle, causing the server to either crash or simply be unable to respond to normal requestsmuch like keeping someone's fax machine constantly busy.
Denial-of-service attacks are very hard to defend against, since they often do not rely upon any weakness in your server software but instead simply keep it too busy to be useful. Thankfully, DoS attacks are not very common, because they require a sustained effort on the part of the attacker, often from multiple machines.
In the most common attacks, software probes a network looking for server software that is known to have a particular weakness, and then attempts to exploit the weakness. Most commonly, this type of attack seeks servers running Microsoft's Internet Information Server (IIS)its Web-server softwareversions of which have been shipped with serious security flaws. Virtually every Web server on the Internet sees multiple daily attacks aimed at IIS software. Of course, since you are running Mac OS X, these attacks mean nothing to you. (See the sidebar "What an Attack on IIS Looks Like.")
An example of a problematic weakness in server software can be found in a "Vulnerability Note" from May 2005 on the US-CERT Web site (www.kb.cert.org/vuls/id/706838) concerning the Virtual Private Network daemon ( vpnd ) installed on Mac OS X. About two weeks after the problem was publicly announced, a security update was available for download from Apple. Notification and installation of the update were automatic for Mac OS X users who had Software Update turned on in System Preferences.
You can see a list of the frequent security updates Apple provides at www. info .apple.com/usen/security/security_updates.html. See "Keeping Up-to-Date," later in this chapter.
Limiting the number of services running on a machine limits both its exposure and the number of things you need to keep up-to-date. For this reason, it is a good idea not to run services you don't need.
To see which services are running:
| 1. | Check the Sharing pane in System Preferences. Open System Preferences, click the Sharing icon, and examine the Firewall settings in the Sharing pane. Deactivate any services you are not using. |
| 2. | Check which jobs are loaded into launchd : sudo launchctl list See also "To list jobs loaded into launchd ," in Chapter 11. |
| 3. | Look for active services in the /etc/hostconfig file. That would be services marked -YES- and possibly -AUTOMATIC- . Through a somewhat complicated process, scripts that are run by SystemStarter (see man SystemStarter ) use variables set in /etc/hostconfig to decide whether or not to actually start a service. Have a look at /System/Library/StartupItems/Apache/Apache . |
| 4. | Look at the currently open Internet connections. sudo lsof -i The lsof command ("list open files"; see man lsof ) is used to list files and network connections that are in use when the command is run. An example of the output is in Figure 12.2 . Figure 12.2. Using the lsof command with the -i option to show active Internet connections. |
| 5. | Look in each file in the /etc/xinetd.d directory, and in the /etc/inetd.conf file (if it exists on your system). For more about xinetd and inetd see the sidebar "The Server of Servers: inetd ." |
Besides limiting the server software you run on a machine, you should also limit which ports are accessible.
About ports and sockets
A socket is the combination of an IP address and a port number .
To understand port numbers, consider that a machine with only a single IP address (which is usually the case) can have many simultaneous Internet connections. Each connection uses a different port number. Here is an analogy: If an IP address is your machine's Internet "street address," then ports are "suite numbers" at that address.
Each Internet service running on a machine "listens" on a specific port number. (Note that "services" are provided by "servers"documentation such as man pages will sometimes use the terms server and service interchangeably.) For example, the default port for e-mail servers is port 25, for an SSH (Secure Shell) server it is port 22, for Web servers it is port 80, and so on. Table 12.1 describes the most commonly used ports, and you can see a list of virtually all the ports with commonly used names in the file /etc/services .
Table 12.1. Commonly Used Ports
| See /etc/services for an almost comprehensive list. | |
|---|---|
| P ORT | U SE |
| 20 and 21 | FTP servers use both ports 20 and 21. FTP is turned off in the default Mac OS X configuration (it can be turned on in the Sharing pane of System Preferences). FTP passwords are sent over the wire unencrypted ("in the clear"). |
| 22 | The SSH protocol. Part of the default Mac OS X configuration. |
| 23 | Telnet servers listen on port 23. Not used in the default Mac OS X configuration. Telnet passwords are sent in the clear. |
| 25 | For e-mail serversthe Simple Mail Transport Protocol (SMTP). Not turned on in the default Mac OS X configuration, but see Chapter 14, "Installing and Configuring Servers." |
| 80 | For Hypertext Transfer Protocol (HTTP) used by Web browsers and servers. Not turned on in the default Mac OS X configuration, but see Chapter 14, "Installing and Configuring Servers." |
| 109 | POP, version 2. POP servers provide remote access to your e-mail box. |
| 110 | The POP protocol, version 3. IMAP. A newer , better way of allowing users to pick up their e-mail over networks. In particular, IMAP makes it easy to read your e-mail from more than one computer. |
| 443 | HTTPS (HTTP plus Secure Socket Layer). Encrypted version of HTTP. Web sites whose URLs begin with https are normally on port 443. |
| 548 | AppleShare over TCP/IP. The latest versions of AppleShare encrypt the password before sending it. |
| 4000 | ICQ. A popular live chat system. |
Port numbers below 1024 (that is, 01023) are specialonly processes owned by root may listen on these port numbers. See the sidebar "How Do Services Get Assigned to Port Numbers?" for more information.
As we mentioned above, the combination of the IP address and port number is called a socket . When you use a Web browser to connect to a Web server, there are two (or more) sockets in use: One involves the server's IP address and port 80, and the other is your local machine's IP address and some other port number (above 1024) to which the server is sending data. So your Web browser sends a request to port 80 on the server and listens on some other port for the response. (The machine that initiates the connection tells the remote machine which port to send responses to.)
TCP? UDP?The descriptions of services shown in /etc/services include TCP (Transmission Control Protocol) or UDP (User Datagram Protocol). TCP and UDP are two different kinds of data packets that are sent over the Internet. Both protocols are part of the TCP/IP suite of protocols (which also includes Internet Control Message Protocol (ICMP) and Internet Protocol (IP). |
How Do Services Get Assigned to Port Numbers?The list of "well-known" and "registered" ports is maintained by IANAthe Internet Assigned Numbers Authority (www.iana.org). The current official list of port numbers is at www.iana.org/assignments/port-numbers, and the standard Unix file /etc/services on your machine is simply a slightly reformatted version of that same information. For many years the IANA was mainly one man: Jon Postel, a true hero of the Internet whose mantra was "Be liberal in what you accept, and conservative in what you send." He gave much good and shaped a world in which the contributions of others flourished. Postel's early death at age 55 was a great blow to the Internet community (see www.postel.org/postel.html). See also Request for Comments 2468 (as in "who do we appreciate...") at ftp://ftp.isi.edu/in-notes/rfc2468.txt. |
A common security measure involves blocking access to ports on your machine at a point closer to the outside world than where services actually listen for connections. When this is done, a connection cannot be established from a remote machine to that port on your machine. So you are protected even if there is a server (perhaps inadvertently) listening (or trying to listen) on that port.
The primary type of traffic carried on the Internet uses TCP (Transmission Control Protocol). You can test whether a particular port is open or blocked to TCP traffic quite easily by using the telnet command, described in Chapter 10, "Connecting over the Internet." Review the section "Connecting using Telnet" in Chapter 10 before proceeding with this task.
To check if a particular port is blocked for TCP traffic:
| 1. | telnet hostname port hostname can be either a name or an IP address, and port is the port number you are checking. For example, telnet localhost 25 attempts to connect to your own machine on port 25. telnet www.matisse.net 80 attempts to connect to port 80 on the machine www.matisse.net. Software that blocks ports often blocks access to some hosts (usually any host except itself) and allows access to others (usually just itself, or machines on the local network), so you should try checking from both your own machine and another machine outside your network (that means you will need a shell account on a Unix machine on another network).
|
| 2. | Stop the connection. You do this by pressing telnet> |
| 3. | quit This brings you back to your shell prompt. |
Any server software can be configured to listen on a nonstandard port, and, generally speaking, servers use "well-known ports" (01023) and "registered" ports (102449151).
The well-known ports 01023 are also called privileged ports, and only root can bind a service to a privileged port. On the other hand, any user on the system can run server software that listens on port number 1024 and above.
The following task describes a simple Perl script that reproduces the Port Scan feature of the GUI application Network Utility (located in /Applications/Utilities ).
One advantage of a script is that you can easily save its output to a file, run it automatically as a cron job (see Chapter 11), or pipe it into e-mail. Also, maybe you will come up with a useful modification of the script.
To see which ports are open:
| 1. | Create a Perl script, using the code listing in Figure 12.3 , in a file named port_scan.pl (Review Chapter 9, "Creating and Using Scripts.") Figure 12.3. Code listing of a Perl script that scans a machine and tells which ports are open. #!/usr/bin/perl # port_scan.pl # Simple port-scanning script # Pointing this script at someone else's machine could be considered # rude, like trying all the doorknobs on their house. ######################################################################### use strict; use IO::Socket::INET; use Socket; # The Well Known Ports are 1 through 1023. # The Registered Ports are 1024 through 49151 # The Dynamic and/or Private Ports are 49152 through 65535 # my $low_port = 1; # lowest port number to check my $high_port = 65535; # Highest port number to check. my $host = $ARGV[0]; _usage() unless ($host); # Gives usage message if no hostname supplied my $ip_addr = gethostbyname( $host ); $ip_addr = inet_ntoa( $ip_addr ); print "Scanning $host ($ip_addr), ports $low_port through $high_port\n\n"; for my $port ( $low_port..$high_port ) { my $socket = IO::Socket::INET->new(PeerAddr => $host, PeerPort => $port, Proto => 'tcp', Timeout => 1, Type => SOCK_STREAM); if ( $socket ) { close $socket; # Is there a standard name for this port? my($protocol,$service) = getservbyport($port,'tcp'); my $description; if ( $protocol ) { $description = " ($protocol"; if ( $service ) { $description .= ", $service)"; } else { $description .= ")"; } } print "Connected! Port $port is open. $description\n"; } } sub _usage { print STDERR <<"EOF"; Usage:
| |
| 2. | Set the file permissions to make the script executable: chmod 755 port_scan.pl | |
| 3. | ./port_scan.pl localhost The script will take a long time to run, since it is checking 65535 different ports. Figure 12.4 shows what the output would look like if you were to activate Secure Login, AppleShare file sharing, Web file sharing, and an e-mail server. (See Chapter 14 for instructions on activating these servers.) Figure 12.4. Annotated output of the scan.pl script. None of these services are active in the default Mac OS X configuration. See Chapter 14 for instructions on activation.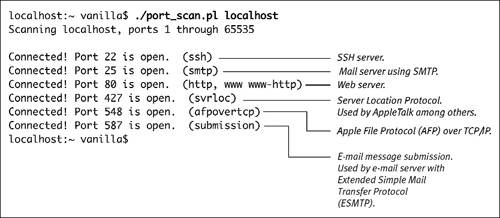 |
Blocking access to ports
Mac OS X comes with a very powerful tool called ipfw for blocking access to ports and doing other "traffic shaping" of Internet connections.
The ipfw utility is rather complex, and misconfiguring it can leave your machine in an almost unusable condition, which may force you to boot into single-user mode to fix things. Before you attempt any command-line changes using ipfw , be sure to thoroughly read the man page and preferably have an experienced person available to help.

Fortunately, the Mac OS X System Preferences include a very reasonable GUI configuration tool for ipfw , so that's what we'll show you here.
To block ports using the Sharing firewall tool:
| 1. | Open the Sharing pane from System Preferences. |
| 2. | Choose the Firewall tab. This shows how to start, stop, and configure the built-in firewall ( Figure 12.5 shows the firewall after it has been turned on). Figure 12.5. Part of the Firewall tab of the Sharing pane from System Preferences.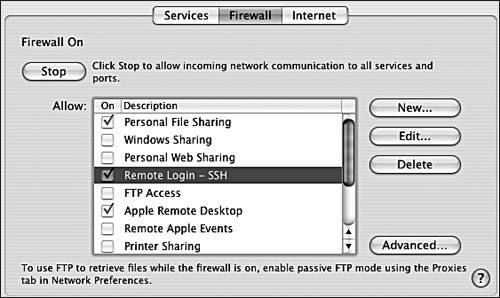 |
| 3. | Click the Start button. The built-in firewall software starts up and blocks access to every port on your machine, except for those explicitly listed and marked as On in the Allow list on this tab. |
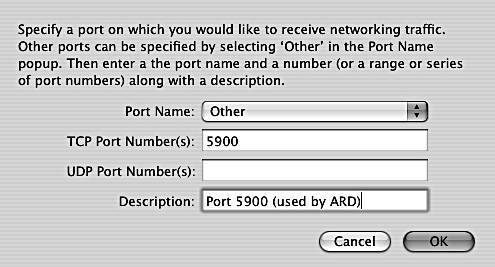
Warning: There are reports of a bug in Mac OS X 10.4.1 in which access for Apple Remote Desktop will be blocked by the firewall even when Apple Remote Desktop is enabled on the Firewall tab. The workaround is to add a rule allowing TCP traffic on port 5900. See the task below, "To add a firewall rule to allow access on a specific port."

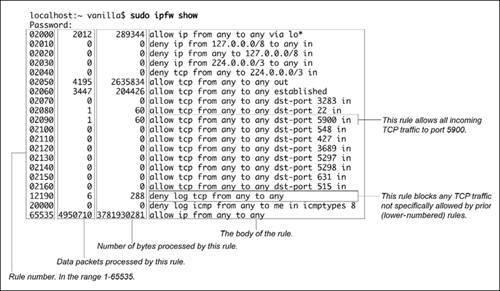
To see a list of the firewall rules:
- sudo ipfw show
This command line displays all the currently active ipfw rules.
The first column is the rule number (165535), the second is how many data packets the rule has processed , the third is bytes, and the rest of the line is the rule itself.
If the firewall is on, you will see several rules. Figure 12.6 is an annotated example of output (yours will differ slightly); see man ipfw for more details.
Figure 12.6. Listing the ipfw rules (your output will differ somewhat).
If the firewall is off, there will be only one rule:
65535 4946989 3780999653 allow ip
 from any to any
from any to any
 Tips
Tips
-
You may limit the output to a specific rule by supplying the rule numberfor example:
sudo ipfw show 2190
-
You can see a list of the ipfw rules without the packet and byte counts by using list instead of show :
sudo ipfw list
or
sudo ipfw list 2190
FirewalkAnother Firewall ToolFirewalk is a GUI application for configuring ipfw on Mac OS X. Firewalk X 2 has more features than the firewall configuration toll built into Mac OS X's System Preferences Sharing tool, including the ability to set a time when rules expire and to have alerts pop up when a rule blocks incoming traffic. Firewalk X 2 has a $34.99 license fee and is available at www.pliris-soft.com/products/firewalkx. |
The list of allowed ports in the GUI firewall tool can be easily changed.
Deleting an item from the list is a matter of selecting it and pressing ![]() . Here's how to add an item to the list (pretty obvious, but we figure we'll walk you through it for fun).
. Here's how to add an item to the list (pretty obvious, but we figure we'll walk you through it for fun).
To add a firewall rule to allow access on a specific port:
| 1. | Open the Firewall tab in the Sharing pane of System Preferences. If the lock icon is locked, click it and authenticate as an admin user. |
| 2. | Click the New button. A dialog appears ( Figure 12.7 ). Figure 12.7. A dialog drops down on the Firewall tab, where you can create a new entry in the built-in firewall tool. |
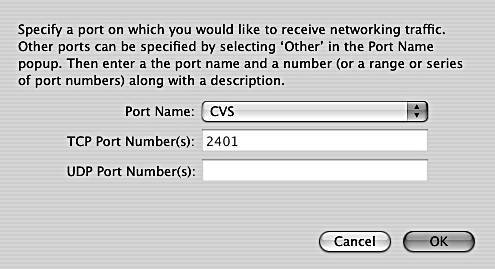
| 3. | Choose an item from the Port Name pop-up menu. If you chose Other, then you get a new dialog as shown in Figure 12.8 . Figure 12.8. A new dialog appears with an additional field if you chose Other in the Port Name menu. In our example, we show how you would allow TCP connections on port 5900. This can be done to correct a bug in the firewall that blocks Apple Remote Desktop (ARD) even when ARD is enabled on the Services tab. The two port number fields TCP Port Number(s) and UDP Port Numbers(s) can be either a single port number, such as 5900; a range, such as 60006010; or a series, such as 7000, 70023, 7034 (you can separate the items with commas, spaces, or both). If you chose a port name from the pop-up menu, the port number will be filled in for you. |
| 4. | Click OK. The new entry is added to the list of ports and is checked as On (to allow access to that port). If you wish to block access to the port, uncheck the box for the entry and make sure the firewall is actually "On." |
 Tips
Tips
-
Check that the rule was added:
sudo ifpw show
-
You can delete an ipfw rule with
sudo ipfw delete rulenumber
For example:
sudo ipfw delete 5900
The rule will come back if you stop and restart the firewall.
The Server of Servers: inetdMac OS X (like virtually all versions of Unix) comes with a special server program called inetd (the Internet daemon ) as well as the more advanced xinetd . Starting with Mac OS X 10.4, Apple has moved almost all of the services that xinetd used to handle to the Apple-created launchd system (see "About launchd " in Chapter 11) and actually uses launchd to launch xinetd . xinetd acts as a kind of dispatch office for several networked servers. It is configured using the file /etc/xinetd.conf , which typically lists one or more directories containing additional configuration files corresponding to a service handled by xinetd . The standard location (used in Mac OS X 10.2) for additional xinetd configuration files is the /etc/xinetd.d directory, where you'll find more than a dozen small configuration files. Mac OS X 10.1 and earlier had only the older inetd program (no x ). In Mac OS X 10.2, Apple added xinetd , but the inetd program may still be running, depending on your system configuration. inetd uses a single configuration file, /etc/inetd.conf , but we suggest you leave it alone. The configuration files for xinetd tell it which services (such as remote-access services) it is responsible for. xinetd can listen on multiple ports, and when it receives a connection, it starts up the appropriate software and hands off the connection to the software it started. Following the general rule of only running servers you actually need, Mac OS X comes with all the entries in /etc/xinetd.d/ disabled, because none of the services listed are required for normal operation (once again, keep in mind that a service is some useful function provided by a server ). Both xinetd and inetd do start when your Mac boots up (by the /System/Library/StartupItems/IPServices/IPservices script). Apple recommends that you use the new launchd facility instead of xinetd , and we suggest you follow that advice (see "Creating New LaunchDaemons and Startup Items" in Chapter 11). If you find that you must run something from xinetd , you will need to add in the /etc/xinetd.d directory. But until that day comes, you can just be aware that it exists and leave it alone (and of course have a look at the file and the xinetd man page). |
EAN: 2147483647
Pages: 161