CMS Authentication and Authorization Process
| As we have already seen, CMS processing involves several layers, as follows:
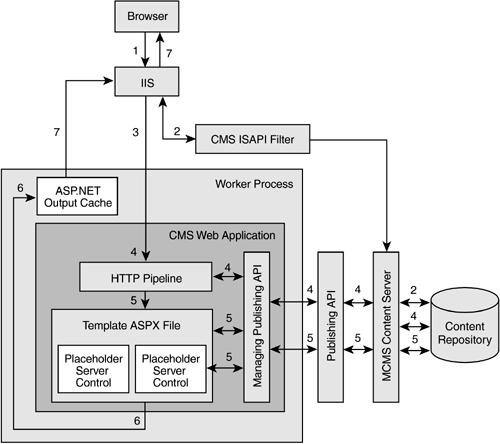
A diagram showing the logical architecture of CMS page processing is shown in Figure 19-1. Figure 19-1. Logical architecture of CMS page processing
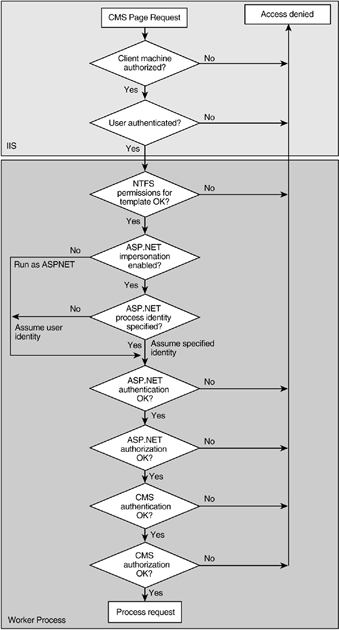
NOTE: For a detailed discussion of CMS page processing in different modes, refer to Chapter 11. As a CMS request passes through multiple layers on the server side, it is authenticated and authorized. Authentication and authorization of a CMS request consists of multiple steps and involves several technologies; it makes use of IIS and ASP.NET security mechanisms. The logical sequence of steps involved in CMS authentication and authorization is shown in Figure 19-2. Figure 19-2. IIS and ASP.NET security mechanisms used in CMS authentication and authorization
A browser has a role to play as well. Within the CMS Web application, the authentication state information is stored in a CMS authentication cookie; if cookies are disabled or not supported in the browser, the CMS application may not function properly. We will look into each layer, starting with reviewing IIS security because the CMS application may rely on IIS for initial authentication of the user. We will then concentrate on the ASP.NET settings for authentication, impersonation, and authorization, and how their use affects the CMS Web application. Then, we will focus on CMS user authentication and authorization, and discuss the configuration required for Windows authentication and forms-based authentication in the CMS Web application.
|
EAN: 2147483647
Pages: 298