19.1 Inter-image communications
| The communicating applications or application parts can be located within one hardware machine or on separate machines that are connected by physical network components. Your choice of communication methods depends on where the applications to be connected run. Table 19-1 lists some of the more interesting options that are used today:
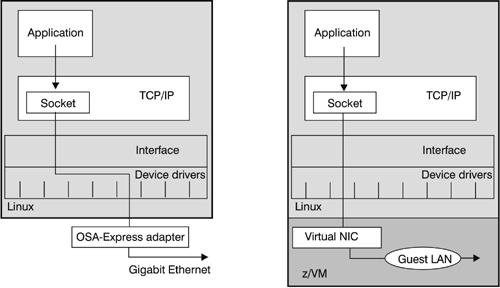
At the time of the writing of this book, Gigabit Ethernet is the mainframe's high-speed LAN adapter for connecting to the outside world (other machines). The machine's internal LPAR and z/VM-based virtual networks are even faster than Gigabit Ethernet. They work at near memory bus speed and reduce the typical network latency. They replace physical cables with virtual cables, which reduces the cost of the external cabling, control panels, switches, routers, and other physical components. Virtual cables improve security, since they defy physical attacks. This immunity to physical attacks can eliminate the need for data encryption. Virtual cables do not protect from harmful content. Firewalls might still be required. Guest LAN and Virtual CTC are unique to z/VM and can be used only among guests of the same z/VM. Guest LANs are virtual LANs that can be based on a physical LAN protocol (Gigabit Ethernet) or on the HiperSockets protocol. Apart from these recommended means of communication, applications in guests of the same z/VM can also communicate via LPAR's real HiperSockets, a real CTC, or a physical Gigabit Ethernet connection. Normally, the communication technology is transparent to an application. This transparency allows you to relocate an application's communication partner without having to change the application. Figure 19-1 illustrates two scenarios of how a Linux application uses a TCP/IP socket to communicate with an application elsewhere. Figure 19-1. Communications are transparent to the application
In the left part of the diagram, the Linux application communicates with a partner on another machine. The Linux configuration assigns the TCP/IP socket to an OSA-Express adapter card, and the communication goes through a Gigabit Ethernet LAN. In the right part of the diagram, both the Linux application and its communication partner run in guests of the same z/VM. The application talks to the same socket as before. Now the Linux configuration assigns this socket to a virtual Network Interface Card (NIC), and the communication is through a Guest LAN. |
EAN: 2147483647
Pages: 199