Relationship of the Standards
| The next few chapters cover a bewildering number of standards, mostly those of IEEE 802 and IETF (RFCs). The following reference list of all the standards that we mention should help you keep track of these standards and serve as a roadmap to indicate if and where they fit into the RSN picture. You may find you want to refer back here as the picture starts to form in your mind. List of StandardsHere is a list of all the standards mentioned in Chapters 8 through 12.
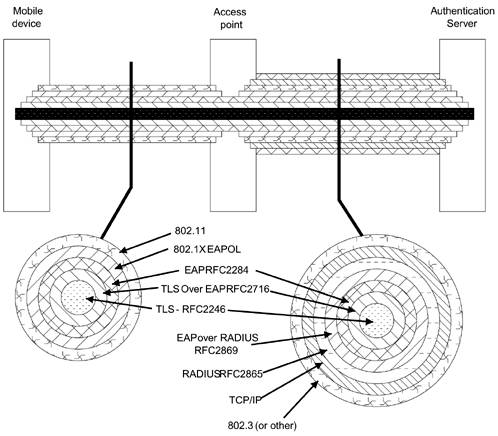
Pictorial MapFigure 7.4 shows a pictorial map of the main standards used in an RSN solution based on TLS authentication. Inevitably the picture is a bit simplistic, but it shows how the TLS authentication process is buried inside a set of standards that provide the communications first between the mobile device and the access point and then between the access point and the authentication server. The links are shown as a set of concentric tubes; the outer tube is the communications medium and successive inner tubes are the encapsulations used to transport the information. As we said at the beginning of this section, we do not expect you to understand the whole picture from looking at Figure 7.4, but we hope it will form a reference point to which you can return. Figure 7.4. Main Standards in an RSN Solution Based on TLS
|
EAN: 2147483647
Pages: 151