Setting up Security-General Steps
|
|
A Word on Mac Address Filtering
It's true that WEP isn't the only Wi-Fi security layer available to you. Many people speak of and recommend a technique called MAC address filtering as a secondary measure worth taking, once you have WEP configured and enabled. And while it's true that MAC address filtering doesn't do any harm, it's unclear to me that it does much good.
First of all, what is it? With virtually all Wi-Fi access points, you have the ability to specify a list of computers that are permitted to associate with the access point. Any computer not on the list will be turned away by the access point, and will not be able to join your network. Since every networkable machine has its own unique MAC (Media Access Control) address (as I explain in Chapter 2) you identify machines that are permitted to use your access point by creating a list of those machines' MAC addresses. The name nails it: MAC addresses allow you control access to your network.
MAC address filtering sounds great-in fact, it sounds like a terrific way to keep drive-by hackers out of your Wi-Fi network, avoiding the significant risk of bandwidth theft and IP impersonation. However, there's a snag: When one of your machines associates with your access point, it transmits its MAC address as 'cleartext' (unencrypted) with no attempt to keep others from listening in. A hacker with a packet sniffer program can listen for the transaction by which your laptop (or one of your other machines) associates with your access point, and your laptop's MAC address will be right there for the hacker to see, without any encryption or concealment.The hacker can then use a technique called spoofing to apply your laptop's MAC address to his own machine, and immediately pretend to be the legitimate user.
The access point cannot tell the difference between two clients both presenting the same MAC address. Although having two different clients associated with a single access point under the same MAC address is a recipe for confusion, the intruder can request that the access point de-associate (in other words, break the connection) with the spoofed MAC address. The intruder can then immediately re-associate, leaving the legitimate user (who is probably non-technical at that level) to wonder what went wrong.
Spoofing kills MAC address filtering stone dead, as far as I'm concerned. Although MAC addresses are indeed burned into the hardware of every Ethernet-compatible network adapter (wired or wireless) and cannot be changed, that's just for the hardware. A piece of software can 'pretend' to have any MAC address it wants. (That's what spoofing is all about.) This is one of two reasons that MAC address filtering is useless.
The other reason is more significant: The Wi-Fi standard Wired Equivalent Privacy (WEP) encryption feature provides the same benefit and is much more difficult to break. If you use WEP, there is no additional benefit that MAC address filtering can give you. Yes, WEP can be broken, but it takes time and effort, and you can thwart WEP attacks by rotating your passwords on a regular basis.
The only case in which MAC address filtering might be (slightly) useful for security is the case where your access point cannot create a WEP-enabled connection with one of your machines. This happened more often in the very earliest days of Wi-Fi, before the standards were as well-defined and understood as they are today. With new hardware this will not be an issue. If you have this problem, consider (as a first step) upgrading the firmware in your access point and/or client adapters. (I explained how to do this in Chapter 6.) If that doesn't work, you may need to replace your client adapter or access point.
MAC address filtering does have uses outside of security, particularly in something called load balancing, in which you have multiple access points serving the same physical area, and need to control how many clients connect to each access point so that they all carry a roughly equal load. I explained this in more detail in Chapter 9.
You'll hear me say this in numerous places in this book: If you use WEP, you've gotten virtually all of the security benefit that standard Wi-Fi machinery can give you. For more security, you'll need to use a virtual private network system or a vendor-specific security solution, both of which cost additional money and may not be available to you unless you work for a company that implements the proper server to be 'the other end of the tunnel.'
If you do want to enable MAC address filtering, the place to look is in your access point's configuration screens. For example, in the D-Link DWL-900AP+ access point, the screen for entering a list of permitted MAC addresses is shown in Figure 14.1. To get to that particular screen, you must log into the configuration system, click on the Advanced tab, and then click the Filters button in the left margin.
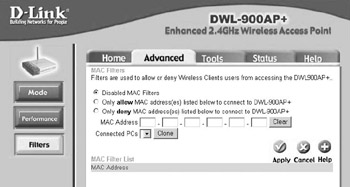
Figure 14.1: The D-Link DWL-900AP+ Mac Filter Screen.
The D-Link DWL-900AP+ is interesting because it allows you to either permit the list of devices to associate with the access point, or forbid the list from associating with the access point. It's far from clear to me how useful it is to have a list of machines forbidden to associate, especially since it's so easy for users to change the MAC address of laptops and other network adapters via spoofing.
|
|
EAN: 2147483647
Pages: 181