Appendix B. Tutorial: Access Lists
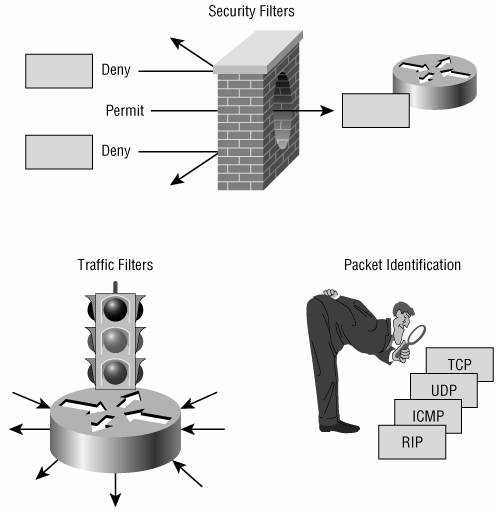
| Access lists are probably misnamed these days. As the name implies, the original intention of an access list was to permit or deny access of packets into, out of, or through a router. Access lists have become powerful tools for controlling the behavior of packets and frames. Their use falls into three categories (see Figure B-1):
Figure B-1. Access lists are used as security filters, as traffic filters, and for packet identification. |
EAN: 2147483647
Pages: 233