The Physical Network
Besides the logical structure of domains, trees, and forests discussed earlier, there are other considerations when you're planning a network. One of these is the layout and configuration of the actual physical network. This involves two primary considerations:
-
Geographical placement of domain controllers
-
Bandwidth availability and management
Sites
A site is generally defined as a part of the network that is connected by high-speed local area network (LAN) links. The advantage of multiple sites is that replication traffic and other server-to-server communications can be configured to occur at certain times, or at certain frequencies, using a Site Link.
local area network (LAN)
A LAN is contained within a single building or campus and can operate independently of any outside connection.
Site Link
A logical connection that links two sites and controls the flow of traffic over WAN links. Just as a trust regulates the flow of permissions and resources, a Site Link regulates the speed and type of traffic that is allowed across the WAN. Site Links therefore enable an administrator to optimize bandwidth usage.
In the following example, your headquarters in Fargo has branch offices in Los Angeles, Atlanta, and New York. Each of the sites has a 512Kbps connection back to headquarters. To save bandwidth during the day, you may create each office as a separate site, and use Site Links to configure them to replicate information only in the evenings. Also, the central site will pass the configuration changes on to all sites, so connectors do not need to be created between Atlanta and Los Angeles, and so on.
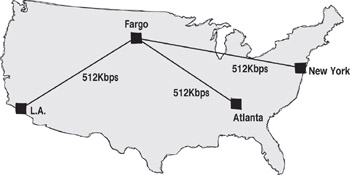
| Tip | Remember that the logical and physical structures of the network do not have to be the same. A network with a physical connection structure like the one above still can easily use a single Windows 2000/Windows Server 2003 domain. |
Domain Controllers
Domain controllers are servers that contain information about users and the security structure of the network. In previous versions of NT, Microsoft used a hierarchical domain controller plan centered on a PDC. Only the PDC could process changes to the security database, and replication would then transfer these changes down to one or more BDCs. Although this has advantages, it also has problems. A user wanting to change their password in Los Angeles would request a password change. The change would be made on the PDC in Fargo, but the user would find that, until the next replication cycle, their own BDC (in L.A.) would not register the change.
replication cycle
The means by which a group of machines synchronize their information; replication is usually done on a preconfigured schedule that can be adjusted due to network or organizational need.
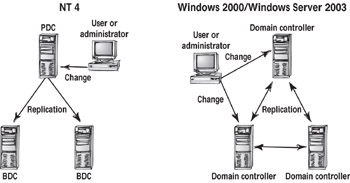
Windows 2000/Server 2003 changes this, allowing for a multimaster domain controller model. PDC and BDC distinctions are irrelevant, since all domain controllers contain a read-write copy of the entire domain's Active Directory. All domain controllers are peers and therefore essentially equal, expect for a few minor special roles held by one domain controller in the forest and one domain controller in any domain. Users in L.A. can now make changes locally and have the L.A. server replicate them outward. The basic functions of a Windows 2000/ Windows Server 2003 domain controller are to:
-
Keep a copy of the security database
-
Process changes to the database
-
Alert other domain controllers of changes through replication
| Note | If you have a network with 10 Windows 2000/Windows Server 2003 servers in a single office, you probably do not want to make them all domain controllers. At least one domain controller is required to create a domain, and a second is recommended for fault tolerance. More than two in a location will probably serve little purpose and just generate unnecessary replication traffic. |
Specialized Domain Controllers
Besides the purposes listed earlier, some Windows 2000/Windows Server 2003 domain controllers can be assigned specific roles to play on the network. Domain controllers can take on the following roles:
-
Global Catalog Master
-
Schema Master
-
Domain Naming Master
-
Relative Identifier Master
-
PDC Emulator
-
Infrastructure Master
Global Catalogs
One of the primary functions of a domain controller is the authentication of users, which could be accomplished by any domain controller on the network In Windows 2000/Windows Server 2003, only domain controllers that have been designated Global Catalog server (GC) can perform this task. The first domain controller in any domain is always a GC, but additional domain controllers have to be specifically configured if you want them to provide this functionality.
| Note | The global catalog has information on the entire forest, not on only one domain. On large networks, the global catalog can significantly speed up the process of finding resources in other parts of the forest. |
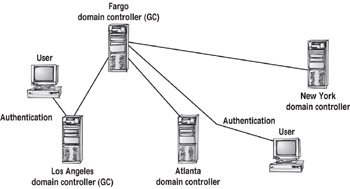
In the following example, for instance, the network on the left has only two GCs. Users from Fargo, New York, and Atlanta all authenticate to the Fargo GC, and if the network connection is down, users from N.Y. and Atlanta will not be able to log on to the domain. Because Los Angeles has its own GC, users authenticate locally, and a break in the WAN connection would not prevent domain logon. Adding Global Catalog can, therefore, increase network performance and save valuable WAN bandwidth. In the example below, a Los Angeles user can authenticate directly to a local GC, while an Atlanta user must authenticate across the WAN to Fargo.
Flexible Single Master Operation Roles
Besides GCs, several other domain controller roles can be assigned to specific machines. Each of these functions must be performed by one-and only one-server within the forest. All were new with Windows 2000 and are still used with Windows Server 2003. There are five types of specialized domain controllers, collectively known as Flexible Single Master Operation (FSMO) roles. Initially, all these roles are given to the first server in the forest, but they may be reassigned to other domain controllers later.
Schema Master Holds the master reference as to the objects in the forest and the way objects are organized. Also manages all updates to the schema.
Domain Naming Master Manages the addition or deletion of the forest.
| Note | There is only one Schema Master and one Domain Naming Master in the entire forest. There is one RID Master, PDC Emulator, and Infrastructure Master in each domain. |
Relative Identifier Master In Windows 2000/Windows Server 2003 domains, an object's security identification number is referred to as a security identifier (SID), just as in NT 4. In 2000/Server 2003, though, the SID consists of a domain SID (which uniquely identifies the domain) and a relative identifier (RID) that uniquely identifies the object in the domain. Together, these two numbers distinguish an object from all other objects in the forest. The RID Master assigns and tracks these numbers.
PDC Emulator If users must connect to or from Windows NT domains, the PDC Emulator manages replication changes and other server-to-server communication between NT 4 and 2000/Server 2003.
Infrastructure Master This domain controller manages the update and tracking of domain groups, and which users are in them. Updates then move through the forest as they are replicated to other Infrastructure Masters.
security identifier (SID)
A unique number used by NT/Windows 2000 Server and Windows Server 2003 to represent a user or a computer on the network.
|
|