Chapter 4: Using Built-in Tools and Settings to Improve Windows Vista Security
Question anyone with even a basic awareness of computer security and privacy issues about the most important tasks to secure a Windows Vista system, and you'll almost always get a lecture on how critical it is to install both firewall and antivirus software. Although there's no denying that the protection these programs offer is absolutely necessary, properly securing a Windows Vista system goes far beyond these essential basics. To secure any Windows Vista system to a high level, you must take advantage of both third-party security programs and the Windows Vista built-in tools and settings.
Window Vista users have no shortage of useful and powerful tools and settings at their disposal - even tools and options not specifically designed with security-related functions in mind are powerful allies in keeping your Windows Vista system locked down and protected. As a Windows Vista user, understanding the arsenal of defensive tools at your disposal is simply essential - although you may not use every available utility or setting on a regular basis, it's important to know what Windows Vista can and can't do before you start looking elsewhere for security solutions.
In this chapter you'll learn more about the native tools and settings that help in your quest to create the most secure Windows Vista system possible. From keeping track of key security settings to using the power of policy to implement user and computer restrictions, Windows Vista really can help to get the job done. The biggest issue, however, is finding and then knowing how to take advantage of many of the not-immediately-obvious security features in Windows Vista.
Exploring Running Processes with Task Manager
Every program and service that runs on a Windows Vista system does so in the context of what is known as a process. If you open Microsoft Word, for example, the WINWORD.EXE process runs until you close the program. Similarly, every time you open a new Internet Explorer browser window, another instance of the IEXPLORE.EXE process starts up. Sometimes a program runs many processes simultaneously, and it's not unusual for Windows Vista to use a single process to carry out many different tasks.
From a user's perspective, a running program is generally considered to be one that can be seen onscreen. For example, when you click the shortcut to open Internet Explorer, a new browser window opens, and the program is obviously running. Not every process that runs on a Windows Vista system does so in a visual manner, however. Many programs and processes run silently in the background, doing their thing without any user interaction whatsoever.
Unfortunately, most users don't recognize that there are a number of processes running in the background on their Windows Vista system. Some of these processes are absolutely required in order for Windows Vista to function. Others may be related to programs you've installed, which start automatically along with Windows Vista. Still others may be silently tracking your online activities, capturing personal details from your computer, or even using your Windows Vista system as a gateway for sending spam e-mail messages. These more malicious processes are usually referred to as mal-ware or spyware, but can also be the result of infections by viruses, worms, and Trojan horse viruses.
Outside of relying on the capabilities of antivirus and antispyware programs to detect rogue programs, you can also use the Windows Vista Task Manager tool to review all processes running on your system. By reviewing the list of running processes in Task Manager you can determine exactly what's running on your computer and the amount of resources that are consumed on a process-by-process basis. The names of different running processes are especially valuable from a security perspective - if you think that malware or another pest might be infecting your Windows Vista system, an unrecognizable or unusual running process name may provide the clue that something is amiss. Ultimately, a web search for the process name helps you to determine whether it's legitimate and necessary, or a security risk that you need to address.
Follow these steps to review running processes with Task Manager on a Windows Vista system:
-
Right-click the Windows Vista taskbar and click Task Manager from the shortcut menu.
-
When the Task Manager window opens, click the Processes tab and then click Show Processes From All Users, as shown in Figure 4-1.
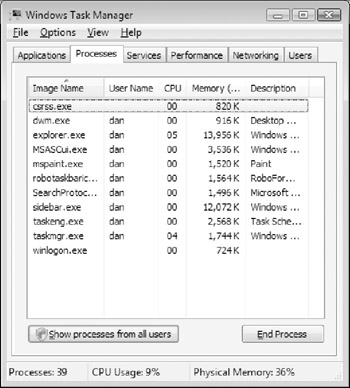
Figure 4-1: The Task Manager Processes tab displays information on all running processes, including those running quietly in the background. -
Click Continue when the User Account Control dialog box appears. The Processes tab now displays all processes on your Windows Vista system that are currently running, and includes details about their memory and CPU usage.
-
To close a process that you believe to be a security risk (see the Tip below for details on determining whether a process is dangerous or not), click the process name, and then click End Process. When the Windows Task Manager window appears, click End Process to end the process.
| Tip | When reviewing running processes in Task Manager, you'll notice that their image names are often fairly cryptic, for example svchost.exe. This can make it very difficult to determine whether a running process is a legitimate process, or something that represents a security risk like malware or a Trojan horse. When in doubt about the purpose of a process, fire up your web browser and go to http://www.processlibrary.com. The http://www.ProcessLibrary.com web site enables you to search for Windows processes by name in a quest to determine the real deal behind unfriendly process image names. |
EAN: 2147483647
Pages: 135