Configuring Cisco Devices for Performance Monitoring
| To measure performance variables such as network latency, no configuration is needed on the Cisco devices. The only requirement is that ICMP should not be blocked by firewalls or access control lists. However, to monitor the rest of the performance statistics, SNMP should be configured on the monitored devices. Most Cisco devices are SNMP aware, but SNMP is turned off by default. The following sections deal with configuring the SNMP agent on these devices:
Enabling the SNMP Agent on Cisco RoutersThe commands for configuring the SNMP agent on an IOS-based device, such as a router or switch, are listed in Table 6-5. Note that these commands should be executed in global configuration mode.
Based on the commands discussed, Example 6-3 shows a sample configuration for enabling the SNMP agent on an IOS device. Within the example, note the highlighted comments that explain some of the relevant configurations. Example 6-3. Configuring the IOS-Based SNMP AgentRouter-Dallas#config terminal Enter configuration commands, one per line. End with CNTL/Z. Router-Dallas(config)#access-list 10 permit 192.168.0.30 Router-Dallas(config)#access-list 10 permit 192.168.0.35 Router-Dallas(config)#snmp-server contact spope@abcinvestment.com Router-Dallas(config)#snmp-server location Dallas office 4th floor Router-Dallas(config)#snmp-server chassis-id 123456 Router-Dallas(config)#snmp-server community read ro 10 Router-Dallas(config)#exit Router-Dallas# show running ! Access-list will restrict SNMP agent to ! respond to queries from the following 2 hosts only access-list 10 permit 192.168.0.30 access-list 10 permit 192.168.0.35 ! the snmp community is set to "read" ! snmp agnet will only respond to manager ! permitted by Access-list 10 snmp-server community readw RW snmp-server community read RO 10 snmp-server location Dallas office 4th floor snmp-server contact spope@abcinvestment.com snmp-server chassis-id 123456 ! end Router-Dallas# show snmp Chassis: 123456 Contact: spope@abcinvestment.com Location: Dallas office 4th floor 16527 SNMP packets input 0 Bad SNMP version errors 15 Unknown community name 0 Illegal operation for community name supplied 0 Encoding errors 33534 Number of requested variables 0 Number of altered variables 6981 Get-request PDUs 9531 Get-next PDUs 0 Set-request PDUs 16512 SNMP packets output 0 Too big errors (Maximum packet size 1500) 66 No such name errors 0 Bad values errors 0 General errors 16512 Response PDUs 0 Trap PDUs SNMP logging: disabled Router-Dallas# Note Routers often use access lists (also called access control lists, or ACLs) to block SNMP requests from the rest of the network. If your SNMP server cannot communicate with the router despite a correct configuration, use the show access-list or show running-configuration command on the router to verify the access lists. Additionally, the firewall between the SNMP server and the router might be blocking SNMP traffic. Enabling the SNMP Agent on Cisco SwitchesTo configure the SNMP agent on a CatOS-based Catalyst switch, use the privileged-mode commands listed in Table 6-6.
Example 6-4 shows the commands for configuring the SNMP agent on the Catalyst switch. Example 6-4. Configuring the CatOS SNMP AgentConsole> (enable) set snmp community read-only read SNMP read-only community string set to 'read'. Console> (enable) show snmp RMON: Disabled Extended RMON: Extended RMON module is not present Traps Enabled: Port,Module,Chassis,Bridge,Repeater,Vtp,Auth,ippermit,Vmps,config,entity,stpx Port Traps Enabled: 1/1-2,4/1-48,5/1 Community-Access Community-String ---------------- -------------------- read-only read ---------------------------------------- Enabling the SNMP Agent on a Cisco PIX FirewallTo configure the SNMP agent on a Cisco PIX Firewall version 5.3 and higher, use the privileged-mode commands listed in Table 6-7. Note that unlike routers and switches, the PIX Firewall does not provide read/write access through SNMP. For the sake of security, the PIX Firewall only provides read-only access through SNMP.
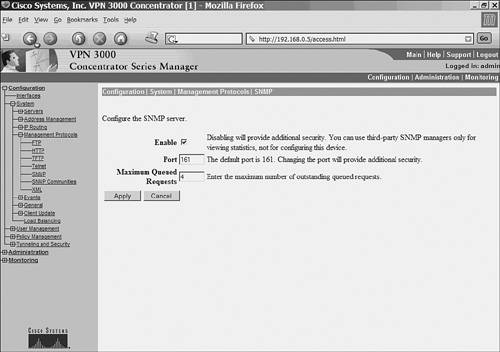
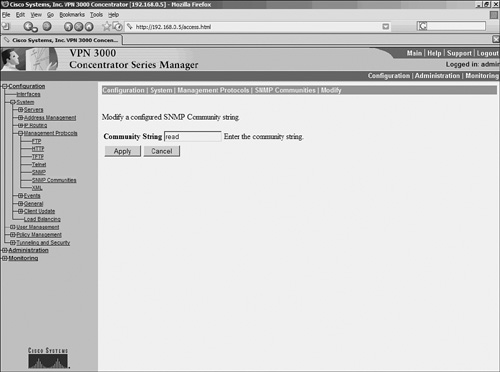
Example 6-5 shows the commands for configuring the SNMP agent on a PIX Firewall. Example 6-5. Configuring the PIX SNMP AgentFirewall-Dallas# config terminal Firewall-Dallas(config)# snmp-server host inside 192.168.0.30 Firewall-Dallas(config)# snmp-server location DALLAS Firewall-Dallas(config)# snmp-server contact SPOPE Firewall-Dallas(config)# snmp-server community read Firewall-Dallas(config)# exit Firewall-Dallas# show snmp snmp-server host inside 192.168.0.30 snmp-server location DALLAS snmp-server contact SPOPE snmp-server community read no snmp-server enable traps Enabling the SNMP Agent on Cisco VPN 3000 ConcentratorsCisco VPN 3000 Series concentrators contain a built-in SNMP agent with read-only capabilities. As a security measure, this feature only allows viewing the statistics of the concentrator but does not facilitate configuring through SNMP. To configure the SNMP agent on a VPN 3000 Series concentrator, follow these steps:
Securing SNMPSNMP was originally designed as a quick-and-easy way to monitor devices. Earlier versions lacked security features such as encryption and authentication. Additionally, the SNMP stack suffers from a series of security vulnerabilities. To enhance the security of their networks, Netadmins should take the following actions:
|
EAN: 2147483647
Pages: 106