Chapter 6: IIS Authentication
This chapter focuses on the Internet Information Services (IIS) 6.0 authentication methods. Microsoft has made radical changes to its Web server in Windows Server 2003. Some of these changes and their impact on the over- all security quality of the Web server are explored in Section 6.1. The rest of the chapter focuses on the authentication methods supported in IIS 6.0.
6.1 Secure by default in IIS 6.0
Windows Server 2003 is Microsoft’s first enterprise operating system that ships with the label “secure by default.” One of the most visible effects of this is that IIS is now an optional service and is not installed by a default Windows Server 2003 installation.[1] This really makes sense if you keep in mind the numerous IIS security exploits that have occurred over the past years. Domain administrators can even prevent other administrators from installing IIS 6.0 on a server in a Windows Server 2003 domain using the following GPO setting: “Prevent IIS installation,” which is located in the Computer Configuration\Administrative Templates\Windows Components\ Internet Information Server GPO container. Note that this setting will not prevent an administrator from installing an IIS 5.0 or earlier Web server on a Windows Server 2003 machine.
Like Windows Server 2003, when IIS 6.0 is installed, it will be in a locked-down state. By default, IIS 6.0 is only capable of providing static Web page support (“static” meaning: plain html files). The dynamic content (for example, active server pages) that can be served by IIS is controlled using a new administration feature called Web Service Extensions in the IIS Manager MMC snap-in (also known as the Internet Services Manager [ISM]).
Other features illustrating IIS 6.0’s secure by default are the fact that URLscan-like functionality has been implemented as an integral part of the Web server and that stronger access control settings are set on the IIS log files and cache directories. URLscan is a tool that scans all incoming HTTP requests to IIS. If it spots suspicious URLs, it blocks the HTTP request. Many Web server hacks consist of sending a URL to the Web server that contains a string that can be interpreted by the Web server as an instruction to execute a particular command. For IIS 4.0 and 5.0, URLscan is available as an add-on tool.
Perhaps the most fundamental change that makes IIS 6.0 more secure by default is its brand-new architecture: Microsoft completely reengineered the HTTP portion[2] of the Web server. The key characteristic of this architecture is isolation. IIS 6.0 supports an operation mode that is known as Worker Process Isolation Mode (WPIM), which enables different Web sites (and their worker processes) that are running on the same physical server to operate completely independent of one another—much like a logical firewall has been set up between them. This enables a per Web site configuration of security parameters (e.g., the security identity used by a Web site) and performance parameters (e.g., the amount of system resources that can be consumed by a Web site). This architecture also provides better protection against denial-of-service (DOS) attacks: An attack on one Web site can never bring down the complete Web server and all the other Web sites running on it.
Figure 6.1 illustrates the new IIS architecture. The entities providing application and Web site isolation are the application pools. As Figure 6.1 shows, an application pool can host several Web applications and sites. Each application pool can be assigned different security and performance parameters—application pools are logically separated from one another. Each application pool shows up in the Windows task manager as a separate instance of the w3wp.exe process. In IIS 6.0 Microsoft also provides separate processes for the administration and housekeeping of the Web server (the Web Administration Service [WAS] or the svchost.exe process) and the treatment of incoming and outgoing HTTP messages (the kernel-mode HTTP.sys driver).
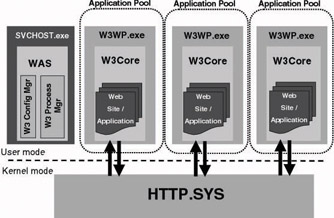
Figure 6.1: IIS 6.0 architecture.
[1]This is not true for Windows Server 2003 Web Edition, the OS’s edition that is specifically targeting Web servers.
[2]This new architecture does not apply to the SMTP, NNTP and FTP portions of the web server.
EAN: 2147483647
Pages: 137