4.4 Authentication in the Windows machine startup and user logon sequences
4.4 Authentication in the Windows machine startup and user logon sequences
In the following sections, we will look at where the Windows authentication sequence fits in the Windows machine startup and user logon sequence. We will see that authentication is performed more than once during machine startup and that machine startup and the user logon feature includes much more than just user and machine authentication.
4.4.1 Machine startup
Figure 4.6 shows the different processes that take place during a Windows machine startup. The machine runs Windows 2000 Professional or later and is a member of a Windows 2000 or Windows Server 2003 domain. The different processes are listed next:
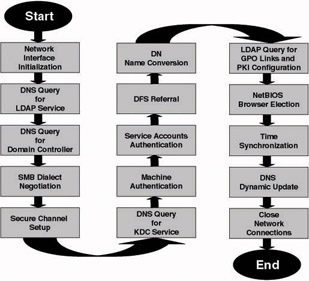
Figure 4.6: Machine startup.
-
The client starts up. The network interface is initialized. If the machine is not configured with static IP configuration information, it will run through the Dynamic Host Configuration Protocol (DHCP) configuration process to obtain its IP configuration.
-
Once the client’s network interface has been configured and the network protocol stack has been initialized, the machine will launch a DNS query for an LDAP service (read domain controller) to one of its configured DNS servers. The DNS query will look for an _ldap._tcp.default-first-site-name._sites.dc._msdcs.main.local service (SRV) record. The site name used in this SRV record depends on the one registered on the machine; by default, it is “default-first-site- name.”
-
When an LDAP service (read domain controller) has been located, the client will launch an LDAP query for a domain controller belonging to the machine’s definition domain to the LDAP server.
-
The client will then negotiate an SMB dialect with the domain controller.[2] The Server Message Block protocol (SMB) is an important file sharing protocol used in all Windows versions. It is used to provide remote file services in a distributed client-server environment. Later on in the startup, it will be used by the client to download configuration information (including GPO settings) from the domain controller.
-
Next, the client will set up a secure channel with the domain controller. To do this it will connect to the domain controller’s Netlogon service. The secure channel is needed to send confidential information, such as authentication data, from the client to the domain controller. Secure channels were explained in Chapter 3.
-
Once the secure channel has been set up, the client will launch another DNS query to its DNS server to find an authentication server (in Windows 2000 and later, a domain controller running a KDC service). The DNS query will look for a _kerberos._tcp.defaultfirst.site-name._sites.dc._msdcs.main.local SRV record. The site name used in this SRV record depends on the one registered on the machine; by default, it is “default-first-site-name.”
-
The machine Kerberos authentication phase takes place.
-
The Kerberos authentication takes place for every service that is not running using the local system account.
-
The client will then connect to the IPC$ share on the domain controller and start the Distributed File System (DFS) referral process. The DFS referral process downloads DFS configuration information from the domain controller to the client (downloading happens using the SMB protocol).
-
The client launches an RPC call to the domain controller to convert its name into a Distinguished Name (DN).
-
Using the DN the client can then perform an LDAP query against its DC to find out the group policies applied to it. The group policy information is downloaded using the SMB protocol.
-
The client then launches another LDAP query to the domain controller to find out PKI configuration information (e.g., what are the Enterprise CAs available in the forest?).
-
If NetBIOS is enabled on the client, it will start a browser election.
-
The client performs time synchronization with its domain controller using the Simple Network Time Protocol (SNTP).
-
Finally, the client launches a DNS query for the start of authority of its DNS domain. The client then performs a dynamic update of its DNS records on the DNS server returned from the previous query.
-
The client startup will be completed by closing down the connections with the domain controller.
4.4.2 User logon process
Once a machine has been started up, a user can log on to it interactively. Figure 4.7 shows the different processes that take place during a regular Windows 2000 or Windows Server 2003 domain user logon process from a Windows 2000 Professional or later workstation. As we will see, the user logon process is much shorter than the machine startup process. The different processes are listed next:
-
After the machine has started up successfully, a CTRL-ALL-DEL screen will be displayed on the screen, permitting the user to start an interactive logon session by pushing CTRL-ALT-DEL.
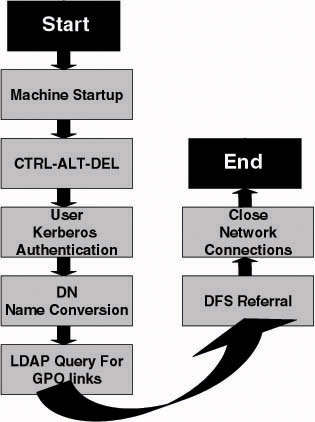
Figure 4.7: User logon process. -
The user presses CTRL-ALT-DEL, fills in a set of credentials, and presses OK or Enter.
-
The user Kerberos authentication sequence takes place.
-
The machine launches an RPC call to the domain controller to convert the user name to a DN.
-
Using the DN the client can then perform an LDAP query against its DC to find out the group policies applied to the user. The user group policy information is downloaded using the SMB protocol. At the same time DFS referral information linked to the user will be down- loaded.
-
The user logon will be completed by closing down the connections with the domain controller.
An Easy Way to Find Out a User’s Authenticating Domain Controller The easiest way to find out the authenticating DC is to check the content of the environment variables that are available in the user’s logon session. To do so, open a command prompt window, then type “set l”; this will bring up all environment variables starting with an l (see Figure 4.8). The user’s authenticating DC is listed on the LOGONSERVER= line.
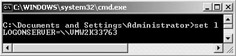
Figure 4.8: Finding out the authenticating DC using “set l.”
[2]An important detail is that Windows Server 2003 has SMB signing enabled by default. This won’t cause problems when using a Windows 98 or Windows 2000 Professional or later client, but may prohibit NT4 and Windows 95 clients to log on to your Windows Server 2003 infrastructure. Installing NT4 Service Pack 4 (SP4) or the Directory Services Client (dsclient.exe) on top of Windows 95 resolves this problem.
EAN: 2147483647
Pages: 137
- Challenging the Unpredictable: Changeable Order Management Systems
- ERP System Acquisition: A Process Model and Results From an Austrian Survey
- Enterprise Application Integration: New Solutions for a Solved Problem or a Challenging Research Field?
- Context Management of ERP Processes in Virtual Communities
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement