Working in Stillness
| In information security, we must always be "listening" for our enemies. When someone steps across a security boundary, a log should be generated and an alarm should go off, spurring us into action. Such logs and alerts are vital elements to our overall security practices. Just like in the physical world, however, it is impossible to "hear" the enemy if there is excessive surrounding noise to confuse us. We will not notice the hacker tripping over a security checkpoint when our logs are full of millions of unimportant activities.
In security we listen; but for there to be noise, there must first be stillness. Security strategists from all ages have used silence as a key tool of defense. So much of security relies on the ability to detect enemies as they attempt to enter the castle. Thus, before we learn to combat our foes, we must first learn how to create silence within the environment.
Creating StillnessCreating stillness requires a level of silence at every location where a security check takes place. This involves the art of alert filtering, making sure we only hear that which is suspicious. When a new security device is put in place, a new operating system is installed, or a new application is created, it must go through a "noise-tuning process." The tuning process should include some post-installation tweaks and adjustments, one of which should be log reduction to provide filtering. Here are some simple guidelines for tuning an object: Five Steps for Tuning Silence
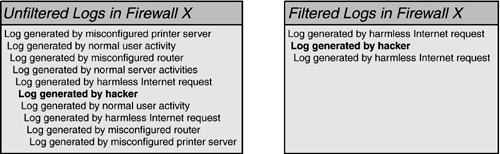
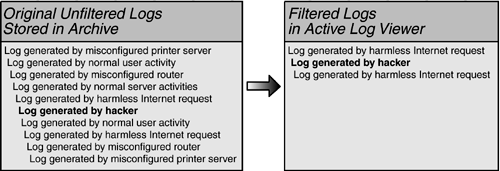
Once all the common events are removed from the environment, we will be much more likely to notice strange events that may indicate an attack. Having finished the tuning process, it will become a part of our daily effort, applying proper filters as new log-generating activities occur. Tiered SilenceWhile it is important to maintain silence at security checkpoints, it is also important to maintain a thorough and accurate record of the events taking place. Many of the events filtered out of the logs could potentially play an important role in a future investigation; do we really want to erase them? When filtering events from logs, it is best to not simply discard them, but rather to store them in an unfiltered archive, separate from normal viewable logs. In this case, logging is set to record many types of events that could potentially be of importance in the future. Only the logs that are the most significant, however, are held in the monitoring system; the rest are sent to an archive server. This way, we can filter out all the extra noise, but still have events on record in case we ever need to go back and do a detailed investigation. At a minimum, this should be performed with critical applications and servers, IDSs, and firewalls. Figure 5.9. Basic log filtering.
Figure 5.10. Filtering with log preservation.
Striking a BalanceThere is a delicate balance that must be struck when creating silence within an environment. If enough of the noise is not filtered out, an attacker's steps could be lost in a sea of extraneous logs and false alarms. If too much is filtered, the alerts will never show a hacker's presence. Here are some good higher practices to follow:
|
EAN: 2147483647
Pages: 119