Chapter 11: Auditing WLAN and Mobile Devices
WLAN and Mobile Devices Background
Mention wireless inside a corporate environment and people immediately think of either their data-enabled mobile phones or the nearest WLAN access point. For different reasons, both these growing-and now generally accepted-technologies present challenges to corporate security.
Conceptually, WLAN and mobile devices both communicate using electromagnetic radio waves from the device to a remote base station. Laptops wirelessly connect to the network through access points (APs) set up by your company. Data-enabled mobile devices communicate to cell towers set up by the mobile operators such as Verizon, Orange, and Cingular before reaching your network. Both technologies are capable of carrying sensitive company data over the network and out over the airwaves. Both technologies also have issues that necessitate forethought into the security of the data en route from the user to your protected and beloved network.
WLAN Background
WLAN enables you to roam past your cube into the conference room and still get your e-mail. However, WLAN traditionally presents problems to information technology (IT) administrators because of the low cost of the access points and the willingness of corporate citizens to compromise the security of the network in favor of getting more work completed. The good news is that WLAN is improving in both the standards and education of the administrators to keep the network secure. Enough bad press and stories of "wardriving" have forced even home users to start paying attention to the security of their networks.
In 1990, the Institute of Electrical and Electronic Engineers (IEEE) formed a group to develop a standard for wireless equipment. The 802.11 standard was born on June 26, 1997, built on using the physical and data-link layers of the OSI model to allow mobile devices to communicate wireless with wired networks.
You might hear Wi-Fi used in the place of WLAN. Wi-Fi is a brand originally licensed by the Wi-Fi Alliance to describe the underlying technology based on IEEE 802.11 specifications. The term Wi-Fi is used widely, and the brand is no longer protected. The Wi-Fi Alliance originally began as an initiative to help bring interoperability to the growing number of devices using different implementations of the 802.11 technologies. New versions are on the horizon, such as 802l.11n, but Table 11-1 references the most common wireless technologies used.
| Protocol | Release Date | Frequency | Bandwidth |
|---|---|---|---|
| IEEE 802.11 | 1997 | 2.4 GHz | 2 Mbps |
| IEEE 802.11a | 1999 | 5 GHz | 6, 9, 12, 18, 24, 36, 48, 54 Mbps |
| IEEE 802.11b | 1999 | 2.4 GHz | 5.5, 11 Mbps |
| IEEE 802.11g | 2003 | 2.4 GHz | 6, 9, 12, 18, 24, 36, 48, 54 Mbps |
| Note | Note that technically every component in a wireless network is called a station. There are two types, access points and wireless clients. |
Wireless clients are also called supplicants. The access points connect the wireless network to the wired network, and the wireless clients or supplicants connect the wireless network to the mobile device. Mobile devices could be a laptop, a wireless enabled personal digital assistant (PDA), or other device configured to communicate with the access point. The set of stations communicating with each other is the basic service set (BSS). The BSS identifier (BSSID) is usually the media access contral (MAC) address of the access point servicing the clients.
There are two types of BSSs, independent and infrastructure. Independent BSSs are ad hoc networks working without an access point. Infrastructure BSSs have access points that can communicate with each other, allowing stations in one BSS to communicate with other stations in a different BSS. An extended service set (ESS) is a set of connected BSSs. Each ESS has an ID called the SSID consisting up to 32 characters. Finally, access points in an extended service set then are further connected by a distribution system (Figure 11-1).
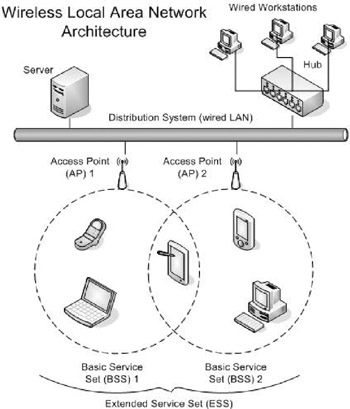
Figure 11-1: Example WLAN architecture.
If you're new to WLANs, then this probably sounds like a lot, and you may think that it's overly difficult to audit. We are going to stick to the basics during the audit process and suggest that you do the same. It's easy to let the scope of a WLAN audit get out of hand, but you can audit for most of the risk by concentrating your efforts on the items listed below. We'll discuss how to go about this process in easily digestible sections.
Data-Enabled Mobile Devices Background
Blackberry devices were by far the most widely used mobile devices in the corporate world at the turn of the century. Since then, other providers have developed similar personal information management (PIM) services and software clients to run on data-enabled mobile devices, or "smartphones." Development is in process and continues such that soon devices will support clients from multiple providers such as Blackberry and Goodlink.
In essence, these smartphones with PDA-like features enable the workforce to take data outside the walls of their companies. This is done with the help of providers such as Blackberry and Good Technologies, which interface your users with your network and the rest of the world through the mobile operator's wireless framework. A typical communications path is illustrated in Figure 11-2.
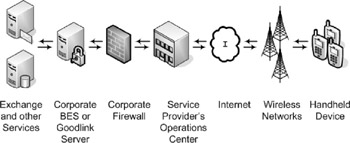
Figure 11-2: Service provider illustration.
The components we want to understand as part of the audit are those that interface directly with your network and users, such as the gateway into your network and the mobile device the user carries.
EAN: N/A
Pages: 159