Chapter 4: VPN Interoperability
Overview
The Microsoft Windows Server 2003 family of operating systems and all of the Windows VPN client operating systems have integrated virtual private network (VPN) technology that helps provide secure, low-cost remote access and branch office connectivity over the Internet. Windows Server 2003 virtual private networking has been designed to interoperate with VPN software and devices that support industry standards for secure remote access. Windows XP and down-level clients all have built-in support for Internet Engineering Task Force (IETF) standard VPN protocols. In addition, Microsoft maintains testing facilities to ensure that the Windows VPN clients and the Windows Server 2003 operating systems meet interoperability standards. Microsoft tests these products against several third-party solutions to ensure interoperability with many VPN concentrators on the market today.
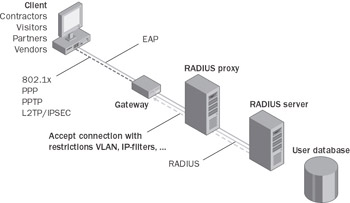
Figure 4-1: RFC Interoperable Standards Support
Microsoft is committed to IETF standards-based technology such as Internet Protocol Security (IPSec) and Layer Two Tunneling Protocol (L2TP) (Request for Comments [RFC] 3193) as well as the Point-to-Point Tunneling Protocol (PPTP)—a proven published informational RFC (RFC 2637) that is supported in multiple interoperable third-party products. Microsoft supports Layer Two Tunneling Protocol/Internet Protocol Security (L2TP/IPSec) and PPTP for the following reasons:
-
PPTP provides simple-to-use, lower-cost VPN security. Unlike VPNs that use IPSec technology, PPTP is compatible without modification with most network address translators (NATs) and supports both multiprotocol and multicast environments. It also combines standard user password authentication with strong encryption without requiring the complexity and expense of public key infrastructure (PKI).
-
IPSec provides advanced security for VPN. IPSec does this by creating and maintaining an encrypted session for L2TP traffic, thus providing security and privacy for the VPN session. With this said, though, it should be noted that IPSec was not designed to address critical remote access requirements such as user authentication and address assignment. In addition, it does not support multiprotocol or multicast environments (including some routing protocols). It is applicable only to Internet Protocol (IP) unicast traffic. These reasons are why Microsoft recommends the use of L2TP/IPSec instead of pure IPSec tunneling—L2TP/IPSec allows for full encryption, session control, authentication, and authorization as opposed to just an encrypted tunnel. IPSec tunneling is supported to comply with the RFC standards. Up until recently, RFC standard IPSec could not traverse NATs, but with the addition of the Microsoft L2TP/IPSec VPN Client for Microsoft Windows Me, Windows NT 4.0, and Windows 98 (available at http://www.microsoft.com/vpn), you have the ability to traverse NAT boundaries with IPSec using NAT traversal (NAT-T) functionality. For NAT-T on Windows 2000 Professional and Windows XP, you need to download the appropriate hotfix from the Microsoft Web site. (The NAT-T hotfix will be incorporated into Windows 2000 service pack [SP] 5 and Windows XP SP2 when they are released in the future.) NAT-T is built into Windows Server 2003.
-
L2TP/IPSec is the only standards-track technology (RFC 3193) that addresses these remote access VPN requirements while leveraging IPSec for encryption. L2TP currently retains the same IETF standards-track status as IPSec.
-
Third-party IPSec-only implementations that do not use L2TP with IPSec are using nonstandard proprietary technologies that can lock customers into closed solutions. This includes the implementation of IPSec tunnel mode (TM) as a VPN solution. As discussed later in this chapter, IPSec TM vendors have implemented this method by using XAUTH/MODCFG functions, which have been rejected by the IETF because of security issues. We will cover these issues in detail later in the chapter.
Because an IETF standards-based pure IPSec solution does not exist, Microsoft believes that L2TP/IPSec provides the best standards-based solution for multivendor, interoperable remote access VPN scenarios. Most major VPN vendors support L2TP/IPSec, even if their primary method is proprietary IPSec TM—this way the vendors can claim IETF compliance. Make sure that when looking for interoperability, you deploy the proper protocol and methods to comply with industry standards.
Customers should analyze the options for VPN solutions and give preference to those that are based on interoperable standards and which support user-based authentication, authorization, and accounting. If you are considering proprietary implementations of IPSec TM, carefully evaluate the availability of solutions based on L2TP/IPSec to support interoperability. You should also consider how your L2TP/IPSec solution might be complemented by PPTP-based solutions. Companies often want a high level of security when working with an untrusted network such as the Internet—and therefore, want the high level of security provided by L2TP/IPSec for external access users—while at the same time preferring to use VPN for security on their internal network. In this case, the combination of PPTP and L2TP/IPSec might make more sense for administrative purposes. Also, to provide certificates to new remote users, a combination of PPTP and L2TP/IPSec allows for the acquisition of certificates to happen under PPTP security and then continue post-certificate provisioning activities on L2TP/IPSec.
Microsoft encourages VPN gateway vendors to provide support for L2TP/IPSec for remote access VPN and as an option to complement IPSec TM for site-to-site (also known as router-to-router) situations, in which multiprotocol and multicast considerations come into play. By supporting L2TP/IPSec, PPTP, or both, Microsoft Windows clients can connect directly to the vendor’s gateway and other VPN solutions without customers having to change client-side code or load a third-party VPN client.
EAN: 2147483647
Pages: 128