Virtual Private Network Definitions
A VPN is the extension of a private network that encompasses links across shared or public networks such as the Internet. A VPN enables you to send data between two computers across a shared or public internetwork in a manner that emulates the properties of a point-to-point private link. In essence, it makes the remote computer virtually part of the private network by making an encrypted tunnel through the public Internet. The act of configuring and creating a VPN is known as virtual private networking.
To emulate a point-to-point link, data is encapsulated, or wrapped, with a header that provides routing information, allowing the data to traverse the shared or public transit internetwork to reach its endpoint. To emulate a private link, the data being sent is encrypted for confidentiality. Packets that are intercepted on the shared or public network are indecipherable without the encryption keys. The portion of the connection in which the private data is encapsulated is known as the tunnel. The portion of the connection in which the private data is encrypted is known as the VPN connection. Figure 2-1 shows the VPN connection.
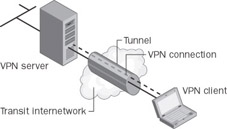
Figure 2-1: The VPN connection.
VPN connections allow users working at home or on the road to connect in a secure fashion to an organization’s remote server by using the routing infrastructure provided by a public internetwork (such as the Internet). From the user’s perspective, the VPN connection is a point-to-point connection between the user’s computer and an organization’s server. The nature of the intermediate internetwork is irrelevant to the user because it appears as if the data is being sent over a dedicated private link.
VPN technology also allows a corporation to connect to branch offices or to other companies over a public internetwork (such as the Internet) while maintaining secure communications. The VPN connection across the Internet logically operates as a wide area network (WAN) link between the sites.
In both of these cases, the secure connection across the internetwork appears to the user as a private network communication—despite the fact that this communication occurs over a public internetwork—hence the name virtual private network. VPN technology is designed to address issues surrounding the current business trend toward increased telecommuting and widely distributed global operations, where workers must be able to connect to central resources and must be able to communicate with each other.
To provide employees with the ability to connect to an organization’s computing resources, regardless of their location, a corporation must deploy a scalable remote access solution. Typically, corporations choose either a department solution, where an internal information systems department is charged with buying, installing, and maintaining an organization’s modem pools and a private network infrastructure; or they choose a value-added network (VAN) solution, where they pay an outsourced company to buy, install, and maintain modem pools and a telecommunication infrastructure.
Neither of these solutions provides the necessary scalability, in terms of cost, flexible administration, and demand for connections. Therefore, it makes sense to replace the modem pools and private network infrastructure with a less expensive solution based on Internet technology so that the business can focus on its core competencies. With an Internet solution, a few Internet connections through Internet service providers (ISPs) and VPN server computers can serve the remote networking needs of hundreds or thousands of remote clients and branch offices.
Common Uses of VPNs
The next few sections describe the more common VPN configurations in more detail.
Remote Access Over the Internet
VPNs provide remote access to an organization’s resources over the public Internet, while maintaining privacy of information. Figure 2-2 shows a VPN connection used to connect a remote access client to an organization’s intranet. This is known as a remote access VPN connection.
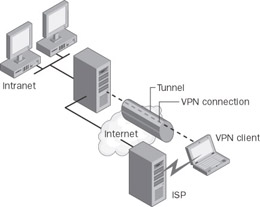
Figure 2-2: Using a VPN connection to connect a remote access client to an organization’s intranet.
Rather than making a long distance (or 1-800) call to an organization’s server or outsourced network access server (NAS), the user dials a local ISP. Using the connection to the local ISP, the VPN client creates a VPN connection between the remote access computer and the organization’s VPN server across the Internet.
Connecting Networks over the Internet—Site-to-Site VPN
The two traditional methods of connecting remote offices to the home corporate network were to have dial-up connections that worked over the public switched telephone network (PSTN) or to use dedicated leased WAN link using frame relay or Point-to-Point Protocol (PPP) synchronous circuits. These methods take a large amount of administration and are expensive to maintain—a typical T1 synchronous circuit that would handle frame relay, PPP, or multiple PSTN lines can cost thousands of dollars a month, a significant recurring cost to a company.
Using site-to-site VPN technology allows a company to remove the recurring monthly costs of high-speed circuits. Using local ISP connectivity on the remote office sites and a single high-speed circuit at the corporate office allows a company to eliminate multiple high-speed connections, frame relay overlay management, the maintenance of a WAN routing architecture, and the significant financial and administrative recurring costs associated with these items.
There are two methods (illustrated in Figure 2-3) for using VPNs to connect local area networks at remote sites:
-
Always-On VPN Networking. Using dedicated lines to connect a branch office to an organization’s local area network (LAN). Rather than using an expensive long-distance dedicated circuit between a branch office and a corporate hub, both the branch office and the corporate hub routers can use a local dedicated circuit and local ISP to connect to the Internet. The VPN software uses the local ISP connections and the Internet to create a VPN between the branch office router and corporate hub router.
-
Demand-Dial VPN Networking. Using a dial-up line to connect a branch office to the Internet. Rather than having a router at a branch office make a long distance (or 1-800) call to a corporate or outsourced NAS, the router at the branch office can call a local ISP. The branch office router uses the connection to the local ISP to create a VPN connection between the branch office router and the corporate hub router across the Internet.
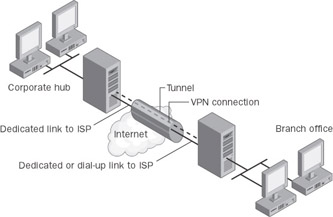
Figure 2-3: Using a VPN connection to connect two remote sites.
In both cases, the facilities that connect the branch office and corporate office to the Internet are local. Either of these approaches allows the corporation to avoid heavy long-distance charges associated with using the PSTN or long-haul leased line costs because both sides are making local phone calls or short-hop leased line connections to their ISP. The ISP then deals with the intermediate network communications issues, Internet routing issues, and site-name resolution—all the complexity is taken out of wide area networking by using site-to-site VPN connections.
When using site-to-site VPN configurations, the corporate hub router that acts as a VPN server must be connected to a local ISP with a dedicated line that is always on-line and listening for incoming connection requests 24 hours a day. The remote sites don’t need active connections for communications. There are many situations when the corporation will want the connection up only as needed, so the connections can be configured as always-on or demand-dial connections that are activated only as appropriate. We’ll cover demand-dial vs. always-on connections in Chapter 8, “Site-to-Site VPN Components and Design Points.”
Connecting Computers over an Intranet—Internal Site-to-Site VPN
In some organizations’ internetworks, some departmental data is so sensitive that the department’s LAN is physically disconnected from the rest of the organization’s internetwork. Examples of this would be company Human Resources records being sealed off from general access or Microsoft’s policy of sealing off development servers from nondeveloper personnel. In essence, the best way to ensure data is not compromised is to not allow connectivity at all by implementing an “air gap” between the secure resources and the general network access. Although this protects a department’s confidential information, it creates information accessibility problems for users not physically connected to the separate LAN. Figure 2-4 shows the use of a VPN connection to connect to a secure or hidden network.
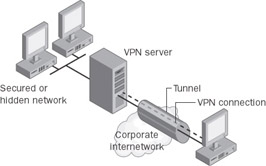
Figure 2-4: Using a VPN connection to connect to a secured or hidden network.
VPNs provide a solution that allows a department’s LAN to be physically connected to the organization’s internetwork but technically shielded and protected by a VPN server. In this configuration, the network physically connects the shielded department network to the rest of the corporation, but by using a VPN server as a gateway to the shielded department’s network resources, the network administrator can ensure that only users on the organization’s internetwork who have appropriate credentials (based on a need-to-know policy within the company) can establish a VPN connection with the VPN server and gain access to the protected resources of the department. Additionally, all communication between the remote workstation and the VPN server can be encrypted for data confidentiality. By placing the VPN server as a gateway to the department, users who do not have proper credentials cannot view the department LAN and users who do have proper access permission can view the department LAN with complete privacy and security over the company intranet.
Basic VPN Requirements
When deploying a remote networking solution, some basic features need to be addressed to provide privacy, data integrity, and connection management for facilitating controlled access to the organization’s resources and information. Providing all these features is a complex process and requires the cooperative effort of several technologies. The solution must allow roaming or remote clients to connect to LAN resources, and it must allow remote offices to connect to each other to share resources and information (site-to-site connections). To ensure the privacy and integrity of data as it traverses the Internet, encryption, authentication, and authorization technologies are required as well. The same requirements apply in the case of sensitive data traversing an organization’s internetwork.
To support all these requirements, a VPN solution should provide all of the following:
-
User Authentication.The solution must verify the VPN client’s identity and grant VPN access to authorized users only. It must also provide audit and accounting records to show who connected and for how long.
-
Address Management.The solution must assign a VPN client an address on the intranet and ensure that addresses used on the intranet are kept private. Also, certain information to allow the client to access resources on the protected network needs to be provided. For example, routing information, resource name resolution, and quarantine security can be provided as well as security filters to ensure the protection of internal data from unauthorized use.
-
Data Encryption.Data carried on the public network must be rendered unreadable to anyone but the VPN client and server. To make this happen, encryption technology must be used between the client and the VPN server.
-
Key Management.To use encryption, the VPN solution needs to provide some sort of encryption-key mechanism to create the session tunnel. The solution must generate and refresh encryption keys for the encrypted data on a mutually agreed upon periodic basis so that security and privacy can be maintained.
An Internet VPN solution based on PPTP or L2TP/IPSec meets all these basic requirements and takes advantage of the broad availability of the Internet. Other solutions, including IPSec tunnel mode (IPSec TM), meet only some of these requirements, but they remain useful for specific situations.
The remainder of this chapter discusses VPN concepts, protocols, and components in greater detail.
EAN: 2147483647
Pages: 128