| Implementing secure email requires some form of PKI, either your own or a commercial certificate vendor. There are pros and cons to using either, as I'll discuss in the next two sections. A.4.1 Using a Commercial Certification Authority Commercial certification authorities like VeriSign and Equifax sell digital certificates (which contain asymmetric keys) to anyone who wants them. Certification authorities require that certificate purchasers prove their identity before certificates can be issued; each uses a different method to verify an individual's identity. Thawte, one of the leading public PKI vendor brands, maintains a national network of "digital notaries" who use traditional forms of identification, such as a passport, to verify a purchaser's identity in person before issuing a digital certificate. As you learned in Chapter 9, certificates are useless unless you trust the person or company who issued them. The advantage of purchasing certificates from a commercial certification authority is that your computer is preconfigured to trust most of them. If you look in Internet Explorer's list of trusted certificate publishers, shown in Figure A-5 and accessed through the Internet Options icon in Control Panel, you'll see a list of publishers whose certificates are automatically trusted by your computer. Figure A-5. Viewing trusted certificate publishers 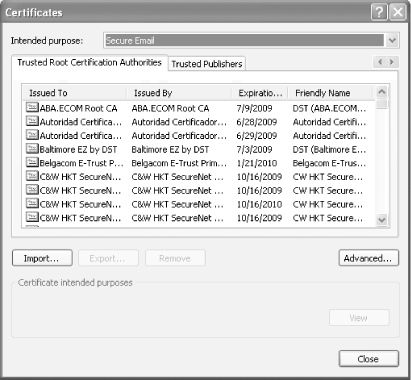
The disadvantage of using a commercial certification authority is that they charge money for the certificates ”from a few dollars to hundreds, depending on the vendor. The certificates usually expire after a year, so the cost of the certificate recurs . As shown in Figure A-6, commercial vendors usually provide a web-based enrollment mechanism, although they often require offline verification of your identity before they will issue a certificate. Figure A-6. Enrolling for a VeriSign personal certificate 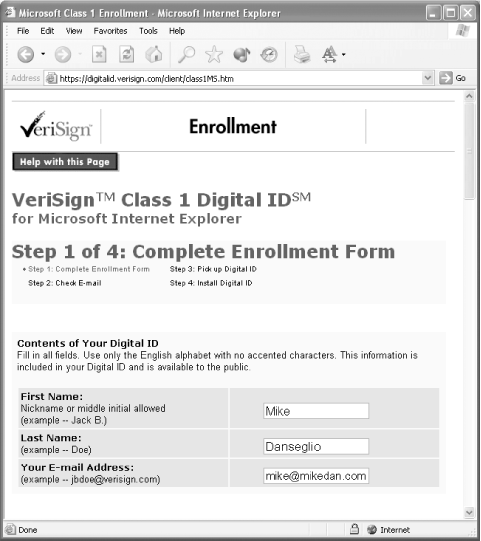
A.4.2 Using Your Own Certification Authority If you need to issue certificates to everyone in your organization, a commercial certification authority can become expensive. You can set up your own certification authority, as described in Chapter 9, to issue certificates to users. The disadvantage of using your own certification authority is that computers, by default, won't necessarily trust the certificates you issue. There are two ways to make them trust you: -
- Obtain a certification authority certificate from a commercial certification authority
-
These are expensive, but they make your certification authority a part of the commercial authority's chain of trust, meaning any computer that trusts the commercial authority will also trust your certificates. -
- Configure your computers to trust your certification authority
-
This is especially easy if the only computers that need to trust your authority are on your network, because you can use group policies to add your certification authority to your computers' trust lists. For information on how to configure clients to trust certificates, see Chapter 9. A.4.2.1 Issuing certificates Windows Server 2003's Certificate Services is capable of issuing email certificates right out of the box. Certificate Services sets up a virtual directory under the server's default web site, which users can connect to in order to request certificates. Figure A-7 shows the web site where users can request a new certificate. Figure A-7. The Certificate Services web site 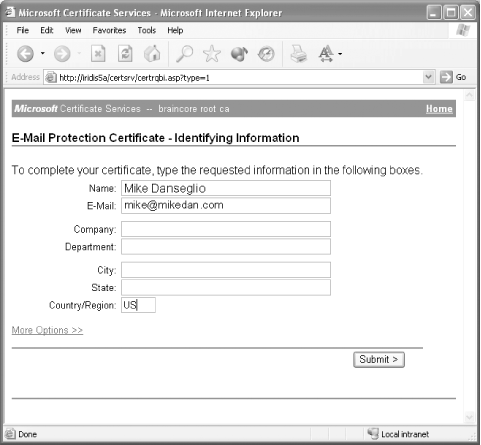
When users request a new certificate, Certificate Services' default behavior is to hold the request until an administrator approves it. You should approve certificate requests only after satisfactorily proving that the user requesting the certificate has provided the correct credentials for the certificate. In other words, if you see a request from Maria, make sure Maria actually requested it before you issue it. Failure to properly verify user identity could result in certificates being issued to the wrong users, allowing them to impersonate one another. Once you issue a certificate, users can retrieve the certificate from the Certificate Services web site, as shown in Figure A-8. Figure A-8. Retrieving an issued certificate 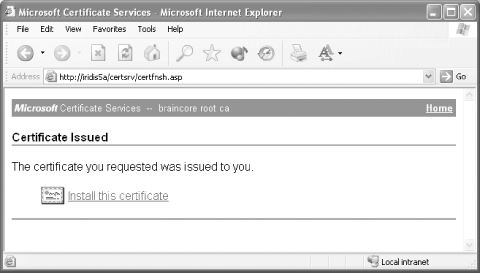
A.4.2.2 Configuring clients to trust you One way to configure clients to trust the certificates issued by your certification authority is to install a certification authority certificate on their computers. The Certificate Services web site allows users to retrieve such a certificate on their own, as shown in Figure A-9. Figure A-9. Downloading a certification authority certificate 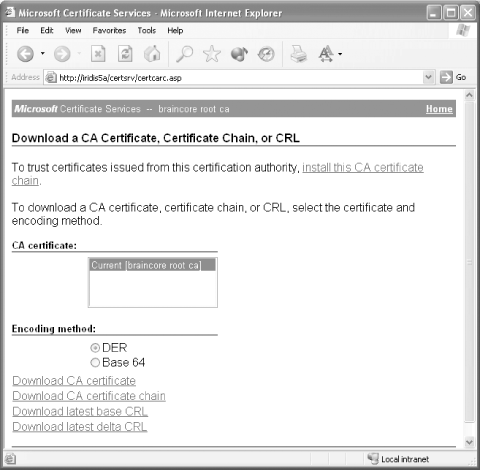
When users download the certificate, they should store it in their computers' Trusted Root Certification Authorities store, as shown in Figure A-10. Once they do, your certification authority will be added to the list of certificate publishers their computer trusts, as shown in Figure A-11. Figure A-10. Selecting a certificate store for the new certificate 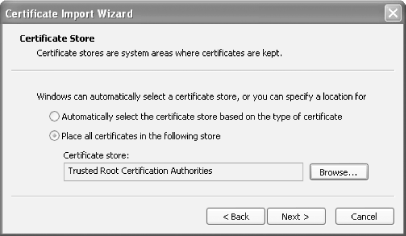
Figure A-11. Viewing the updated list of trusted certificate publishers 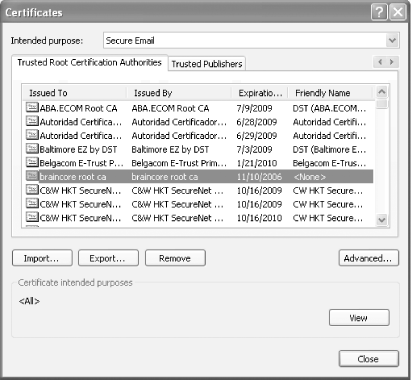
 | You can also create a Group Policy Object (GPO) that modifies the list of trusted publishers on all your company's computers. You'll find this policy in Computer Configuration\Windows Settings\Security Settings\Public Key Policies\Trusted Root Certification Authorities . This is a great way to configure all the computers on your network to trust your certification authority, although it won't allow you to configure outside computers. | |
A.4.3 Configuring Your Email Client Users' email software usually requires some configuration in order to use their newly issued digital certificates. A wide variety of email clients ”including Microsoft Outlook Express, Microsoft Outlook, Netscape Communicator, and Lotus Notes ”support secure email.  | In this section, I'll focus on configuring Microsoft Outlook Secure email for other email software is very similar, although you should consult your software's documentation for details. | |
Outlook 2002's Options dialog box includes a Security panel, shown in Figure A-12. The Security panel lets you configure Outlook to encrypt or sign all outgoing messages. You may also choose to encrypt or sign specific messages by using the appropriate toolbar buttons or menu commands within each message you type. Figure A-12. Outlook security options 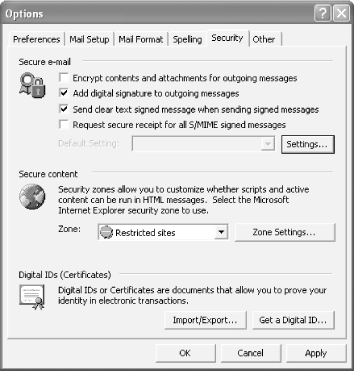
Clicking the Settings button displays Outlook's Change Security Settings dialog box, shown in Figure A-13. As shown, you can specify encryption methods and, most importantly, select the certificates that Outlook will use to digitally sign and encrypt messages. Figure A-13. Outlook secure email settings 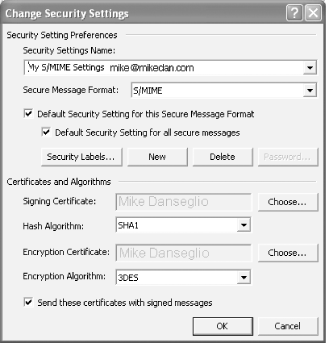
When you select a certificate, Outlook displays the list of certificates installed on your system that are marked as usable for email security, as shown in Figure A-14. Figure A-14. Selecting a certificate for Outlook to use 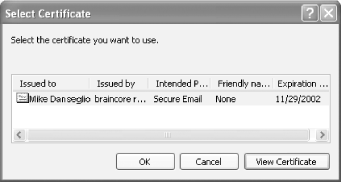
 | All certificates are not created equal. When a certification authority issues a certificate, it marks the certificate with certain approved uses. Email software cannot use a certificate unless that certificate is marked for use with secure email. | |
In the certificate selection dialog box, you can select any certificate and then click View Certificate to see the details, as shown in Figure A-15. The certificate's details will show the uses the certificate is good for and indicate whether you have the private key associated with the certificate. The certificate's private key is required for Outlook to work properly. Outlook's configuration must also be changed from the default, as described in the "Outlook's Default Encryption Settings" sidebar. Figure A-15. Viewing certificate details; note the very bottom line of text, which indicates that you have the private key for this certificate 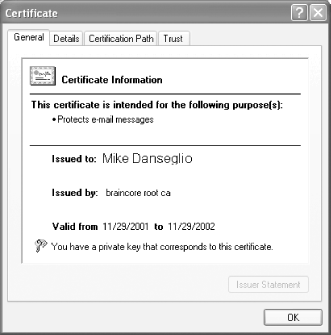
A.4.4 Non-Microsoft Secure Email What if you're not using Microsoft Outlook, or a similar solution, for email? What if you don't want to invest in expensive certificates or implement a certificate hierarchy? For years , Internet users have been using Pretty Good Privacy (PGP), a powerful and flexible solution for secure email, even across operating systems.  | How good is "pretty good" privacy? Since the newest editions of PGP use top- notch 128-bit encryption, the answer is "pretty great." While it's certainly possible to break PGP's encryption, doing so would take several powerful computers several years of dedicated effort. Odds are, by the time they broke the encryption, the information thus revealed would be useless. In practice, because of the time and resources required to break this level of encryption, pretty much nobody tries . | |
PGP is an open source (www.opensource.org) project of the PGP Corporation (www.pgp.com). The PGP product is available in a variety of editions, including free editions, enterprise-ready editions, and more. PGP provides 128-bit encryption for email and attachments, tools to manage PGP deployments within an enterprise, and robust cross-platform support, including the latest Windows, Linux, Apple, and Unix operating systems. PGP even integrates directly with Outlook, Notes, GroupWise, Eudora, and a number of other email clients for easier operation. In addition to providing encrypted email, PGP can also be used to digitally sign email, ensuring that recipients know your email is from you and was not altered in transit. A number of online services ”including HushMail (www.hushmail.com) ”provide secure email delivery. These online services allow you to establish an SSL-secured session in your web browser, compose or upload an email, and have that email digitally encrypted and sent. These web-based services are great for users who have only an occasional need for secure email and don't want to implement a complete secure email solution. PGP, by the way (along with the many PGP-compatible products out there), requires PKI, too. Generally, you'll obtain a certificate from a commercial certification authority so that everyone will trust your certificate and have access to your public keys. Solutions like HushMail don't generally require a key purchase, although they do often require their own registration and usage fees that offset any savings you might see in not buying a certificate. |