| Like the Kerberos authentication protocol, which you learned about in Chapter 7, secure email uses cryptography to validate the sender's identify (in the case of digitally signed messages) or to protect the message's content (in the case of encrypted messages). A.2.1 Digitally Signed Messages Figure A-1 illustrates how a user can send a digitally signed message using email software such as Microsoft Outlook. Figure A-1. Sending a digitally signed message 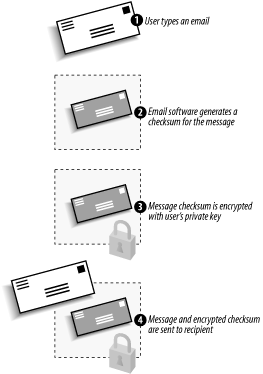
Here's how it works: -
The user types a regular email and tells Outlook to digitally sign the message. -
Outlook calculates a checksum on the message. The checksum is the result of a mathematical hash algorithm and is different for every message. Changing a single character in the email would change the resulting checksum. (Remember that we discussed hash algorithms in Chapter 2.) -
Outlook retrieves the user's private encryption key from local storage and uses it to encrypt the checksum. The checksum is now a digital signature. -
Both the unencrypted message and the signature are sent to the recipient.  | Digital signatures do not prevent others from reading the text of the message. The message is sent in clear text; only the signature uses encryption. This encrypted signature is easily decrypted by anyone , as we will see. | |
The recipient must perform a somewhat more complex process to validate the digital signature, as illustrated in Figure A-2. Figure A-2. Receiving a digitally signed message 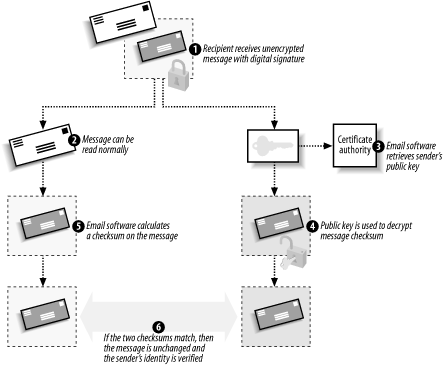
When the message reaches its destination: -
The recipient receives both the clear-text message and the digital signature. The recipient's email software handles each piece individually. -
The email text is immediately readable, because it was not encrypted. -
The email software retrieves the sender's public key. This can be obtained from a certification authority, or the public key may be included along with the message in the form of a certificate. If the certificate accompanies the message, it is verified to ensure it is authentic and chains to a trusted root certification authority. -
The email software uses the public key to decrypt the signature, revealing the original checksum sent by the message's sender. -
The email software uses the same algorithm that the sender used to calculate a checksum on the clear-text message. -
The email software compares the checksum it calculated with the now-unencrypted checksum from the signature. If they match, the sender's identity is verified ”because only the sender could have encrypted the checksum with his private key ”and the contents of the message are verified ”because the two checksums match. How Do They Find My Public Key? Anything encrypted with a digital certificate contains unencrypted information about the certificate that was used. This information allows the recipient to contact the appropriate certification authority and obtain your public key. In Chapter 9, I discussed how certificates can be published to a variety of locations and retrieved when necessary to encrypt, decrypt, or verify data. More commonly, however, email software simply bundles a copy of your public key along with the message, making it immediately available to your recipient. Your recipient must still trust the certificate, which is a concept I'll discuss later in this chapter. The recipient will also verify its authenticity to ensure that you didn't send along a forged certificate. |
A.2.2 Encrypted Messages Encrypted messages go a step further than digital signatures by encrypting the entire message. The message's contents are protected from eavesdroppers, and the message cannot be altered without making it undecryptable. Because of the nature of public key cryptography, encrypted messages do not provide validation of the sender's identity unless a digital signature is used in conjunction with the message encryption. Figure A-3 illustrates how encrypted email can easily be sent. Note that this is a generic example and not specific to any implementation. Many implementations do things differently, such as S/MIME creating a symmetric key for message encryption. Figure A-3 shows the easiest way to implement email encryption. Figure A-3. Sending an encrypted message 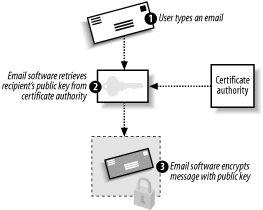
In the simplest encrypted email: -
The sender types an email message and tells her email software to encrypt it. -
The email software retrieves the recipient's public key. This can be obtained from a certification authority, although many enterprise mail servers, including Microsoft Exchange Server, allow recipients' public keys to be stored along with their email addresses in the server's address book. -
The email software uses the public key to encrypt the entire message, which is then sent to the recipient.  | Messages encrypted with your own private key can also be sent. However, anyone with access to your public key ”pretty much anybody ”will be able to decrypt the message. Using your private key to encrypt messages provides a similar form of security as digital signatures, although more information is encrypted, thus making the message larger and more difficult to process. | |
When the recipient receives the email, the corresponding email software simply decrypts the message using the recipient's private key, as illustrated in Figure A-4. Figure A-4. Receiving an encrypted message 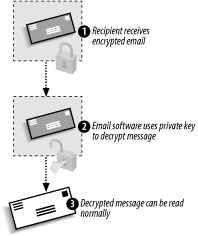
|