| RAS is a complex technology that can be implemented in almost as many ways as there are customers to implement it. The scope of remote access configuration is far beyond what can be addressed within the security focus of this book. However, I can address some common configurations and examine the security-specific configurations and concerns. 14.5.1 Setting Up Remote Access Authentication for Dial-in Users The most common use of RAS is for dial-up users to connect to the corporate network from remote locations with their modems. In this example, I'll assume a third-party modem bank is used and configured to use a separate RADIUS server for authentication and accounting. This customer has allocated a Windows Server 2003 computer specifically to be used for IAS. The written security requirements for remote users connecting to the corporate network include restriction on the hours allowed for dial-in connections to ensure the resources are used appropriately. In addition, security policy dictates that users must authenticate against an Active Directory domain. To configure remote access to provide this functionality, follow these steps: -
Install IAS on the server. You'll find IAS in the Add or Remove Programs application on the Control Panel; just click Add/Remove Windows Components and select Internet Authentication Service from the Networking Services component's Details list. -
Open the Internet Authentication Service console from the Administrative Tools program group . -
Examine the default remote access policies for applicability by clicking Remote Access Policies. Generally, you'll want to delete the two default policies and create your own, which is what I'll do in this example. -
Right-click Remote Access Policies and select New Policy from the pop-up menu. -
Click Next to begin, then click Set Up A Custom Policy. Then provide a policy name. In this example, the policy will be used to restrict dial-up access to evening hours, so I'll name the policy Evening Hours Only. Click Next to continue. -
Click Add to add a policy condition. -
Double-click Day-And-Time-Restriction in the list. -
In the Time of Day Constraints dialog, highlight the hours during which dial-up access will be allowed. Then click Permitted to change the highlighted hours to blue, indicating that dial-up access will be permitted during those times. This is shown in Figure 14-12. Figure 14-12. Date and time restrictions for RAS users 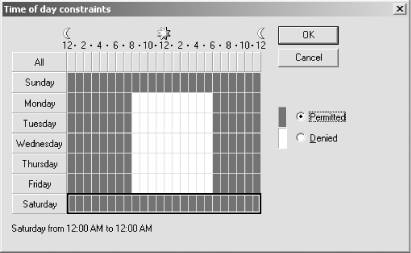 -
-
Click Add to add a new policy condition. -
Double-click Windows Groups in the list. -
-
Type Domain Users in the list and click OK, then click OK again. Your policy conditions will appear similar to those shown in Figure 14-13. Figure 14-13. Policy conditions for the new RAS policy 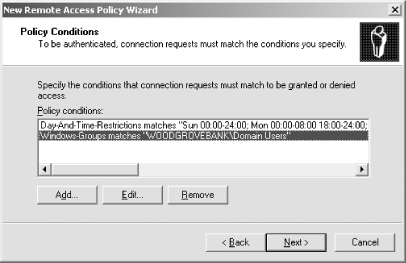 -
-
Click Grant Remote Access Permission. This will grant remote access permission if the policy conditions are met. Then click Next. -
Click Next, and then click Finish to create the policy. The new policy will allow dial-up access for members of the Domain Users group only during the specified hours. If users attempt to dial in at other times, they will not match the policy conditions and will be denied dial-up access. You'll also need to ensure that users' Active Directory accounts are configured to adhere to the remote policy conditions. This is the default in Windows Server 2003, so unless you've previously modified it (on the Dial-in tab of each account's Properties dialog), you're good to go. Now, you'll need to configure your dial-up devices to use IAS for authentication. Consult their documentation for details on doing so. You also have to let IAS know that the devices will be using it, by adding them as RADIUS clients : -
In the Internet Authentication Service console, right-click RADIUS Clients and select New RADIUS Client from the pop-up menu. -
Type a name and the IP address of the first device that will use IAS for authentication. Click Next. -
Generally, you'll select RADIUS Standard for the Client-Vendor. However, if your device's documentation specifies a different setting (such as US Robotics or Shiva), use that. -
Specify a shared secret. This is essentially a password that the device will use to contact IAS. IAS and the device must be configured with the same password. -
That's it! Once your device is configured, IAS will provide central control over dial-up authentication. 14.5.2 Setting Up a VPN Server Another very common example in the modern workforce involves work-at-home employees. Many companies allow employees to work from home or a remote location. As high-speed Internet connections proliferate, the dial-up RAS scenario is often being replaced with virtual private networking that provides a high-speed connection through the Internet to the corporate network. However, this scenario presents a very important security concern. Many attackers prowl the Internet and can be indistinguishable from authorized users. I must ensure that all communication received over the Internet is secure, providing access to authorized clients while blocking unauthorized attackers . To configure RAS to provide secure VPN connections, follow these steps: -
Open the Routing and Remote Access console. This example assumes that you haven't previously configured Routing and Remote Access. -
Right-click the server name and select Configure and Enable Routing and Remote Access from the pop-up menu. -
-
Select Custom Configuration and click Next. -
Select VPN Access and click Next. -
Click Finish to complete the wizard. -
Select Yes to start Routing and Remote Access. This prompt appears because the Routing and Remote Access service is not yet started on this computer and Windows assumes that, because you are configuring Routing and Remote Access, you want to start it. Routing and Remote Access automatically creates a number of VPN ports, including 1 PPPOE port, 128 PPTP ports, and 128 L2TP ports. You should disable any that you don't plan to use and ensure that the others meet your configuration needs. To modify these ports: -
Right-click Ports in the Routing and Remote Access console. Select Properties from the pop-up menu. -
Select a port from the list and click Configure. -
Select the appropriate options to enable inbound VPN access or both inbound and outbound. In this example, only inbound PPTP access is required; I'll enable that for PPTP. In this example, the default of 128 PPTP ports is sufficient, and I leave that alone as shown in Figure 14-14. Figure 14-14. Configuring PPTP to accept incoming connections 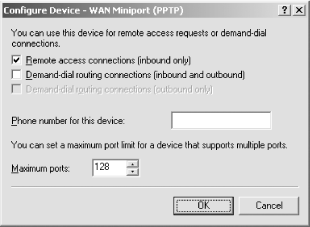 -
I'll disable the other VPN ports since I don't plan to use them right now. I do this by clicking each of them, clicking Configure, then deselecting all connection types as shown in Chapter 14. Eventually the only device that has a Used By listing is PPTP. Figure 14-15. Disabling RAS devices is simple 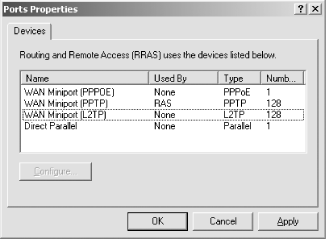
Setting up Routing and Remote Access to accept VPN connections is easy. You'll likely have more trouble dealing with users' ISPs, which may not provide the routing support necessary for PPTP or L2TP connections. If users aren't able to make a VPN connection, contact both your corporate ISP and the user 's ISP to ensure that they support the VPN protocol you are attempting to use.  | Routing and Remote Access can be configured to use IAS or another RADIUS server to authenticate VPN users. To do so, modify the properties of the server in the Routing and Remote Access console and select RADIUS Authentication for the authentication provider on the Security tab. | |
|