What Just Happened?
| I came across Kathy's blog, shown in Figure 5-1, one afternoon, by performing a search with three common keywords: blog, vacation, and teenager. Figure 5-1. Leaking information through blogs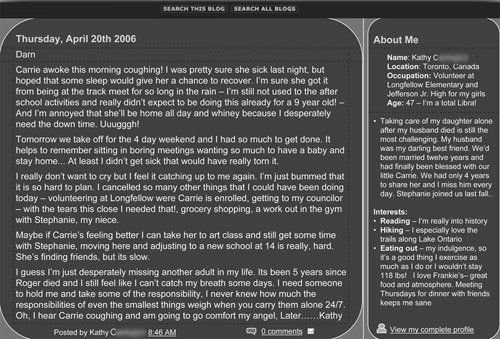 On browsing through her blog, I found that Kathy, a 47-year-old seasoned blogger who'd had a site for over three years, was articulate and well read. Yet, she had unknowingly provided all the information necessary to
It took me four minutes to get information about Kathy, including her address, phone number, workplace, personal history, emotional state, family situation, and weight. With the information she's provided, Kathy has opened herself up to having her identity stolen, her house broken into, or even potentially being physically abused. A man studying her interests and background could transform himself into her "dream" man by sharing her likes and use that advantage in a variety of ways. He could also use that connection to get to her daughter or niece. When I contacted Kathy, I started by asking her if she felt she understood the risks of posting information online. She said she did. When I expressed concern over what her blog contents revealed about her, she reacted with disbelief that anybody could locate her through information in her blog. "How do you think I got your phone number?" I asked. There was a silence on the other end of the phone line. Suddenly Kathy seemed to take my call more seriously. When she realized the danger she had placed herself and her daughter and niece in, Kathy's reaction was one of anger that her blog host had not advised her about the risks of posting personal information online to the public. Unfortunately, this is all too common. Most blog/social networking companies default users to a "Public" profile, which gives them the best revenue opportunity. It is then up to the user to figure out how to change the settings if they want to limit the number of people they share their space with. Keep in mind that publicly viewable blogs are great for sharing publicly appropriate information. The trouble begins when you place private information on a publicly viewable site, whether a blog, discussion board, or chat room.
|
EAN: 2147483647
Pages: 157