WINDOWS NT NETWORKING AND ADMINISTRATION
As mentioned earlier in this chapter, a Windows NT Workstation can participate in a workgroup or a domain environment. In a workgroup, each computer system houses its own SAM database. In a domain environment, the SAM database is located in a more central location, such as a PDC or BDC. This allows administrators to control user access to the network and provide for the sharing of network resources from a centralized location. A workgroup model mirrors a peer-to-peer network in which security and the sharing of resources is controlled at every machine. Imagine organizing a workgroup of 200 users—you would have to control user access to the workgroup and password-protected shares at every single system!
User Account Creation and Management
Windows NT comes with an administrator account that is used to manage and maintain the operating system. You were asked to create a password for this account during the Windows NT installation process. Keep in mind that a Windows NT administrator account can be renamed, but it cannot be deleted. Once you are logged on as the administrator, you can create user accounts (or user IDs), which grant users access to a Windows NT network.
User accounts are created in User Manager on Windows NT Workstation. User Manager can be accessed by selecting Start > Programs > Administrative Tools [Common] > User Manager. Selecting User Manager brings up the window shown in Figure 25.3. If you are using Windows NT Server, you will administer user accounts with User Manager for domains. User Manager for Windows NT Workstation is a scaled-down version of the more complex User Manager for Domains.
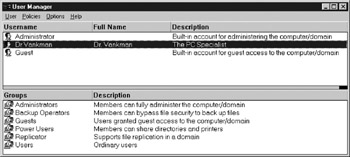
Figure 25.3: The Windows NT User Manager.
Following are guidelines for creating Windows NT User IDs and passwords:
-
User IDs can be up to 20 characters long and are not case sensitive.
-
User IDs can be made up of numbers, letters, and allowable characters.
-
Passwords can be up to 14 characters long and are case sensitive.
-
Passwords can be made up of numbers, letters, and allowable characters. The following characters can be used to make up a password: ` ~ ! @ # $ % ^ & * () _ + - = { } | [ ] \ : “ ; ‘ @ : ? , . /
-
As shown in Figure 25.3, User Manager has several built-in groups. These groups are designed for ease of administration. A Windows NT built-in group has pre-assigned user rights. Windows NT user rights allow users or groups of users to carry out specific tasks, including the right to backup the system, shut down the system, or change the system time. After a user ID has been created in User Manager, it can be placed in a group. When the user ID is placed in a group, the ID inherits all the rights associated with that group. For example, if the user ID BSAWYER were created and added to the Administrator Group, the user BSAWYER would inherit all the user rights associated with the Administrator Group.
Every Windows NT Workstation or Server has a set of built-in local groups. If a user has been placed into a local group, it is possible for the user to access resources and be granted rights on the local system. To ease domain-level administration efforts, Windows NT Server also makes use of global groups. Many users can be placed in a global group, and the global group can then be added to a local group located on a workstation or server. The end result is that it is possible for all users in the global group to access resources assigned to the local group on a particular workstation or server.
In addition to creating user IDs and assigning user rights, User Manager also has the ability to audit the success and failure of events that occur on the system. An administrator can audit access to files and objects, users who have logged on or logged off the system, and security policy changes, just to name a few. The results of the events that have been audited are displayed in the Windows NT Event Viewer. Event Viewer is described under “Utilities and Settings,” later in this chapter.
Logon
When Windows NT first boots up, a user ID and password are required to sign on to the local computer system or the network (domain) the system is connected to.
Once a user ID and password have been created for a user, the user can proceed to sign on. Once a user is signed on to the operating system, the Windows NT Security and Logon Information box can be displayed by pressing the Ctrl+Alt+Del keys, all at once. The Logon Information box displays the following information and provides the following options to the currently signed-on user:
The computer name and currently signed-on user.
The logon date and time.
Lock Workstation: This is a great built-in security feature that lets the user secure the computer while away. To unlock the workstation, the user presses Ctrl+Alt+Del again and enters the proper credentials to sign back on to the system.
Logoff: The option to end the current Windows NT session is available. Simply select the Logoff radio button. The message “This will end your Windows NT session” appears. Select the OK button, and you will be logged off the system.
Shut Down: If you select the Shut Down option, you are presented with the option to shut down the system or shut down and restart. These options are the same as the options offered by selecting Start > Shut Down from the Windows NT Desktop display. The only exception is that you are also offered the ability to close all programs and log on as a different user if you use Start > Shut Down.
Change Password: If you have been granted the right to change your own password by a network administrator or network security person, you can select the Change Password radio button to change your sign-on password (user rights are discussed shortly).
Task Manager: Similar to Windows 9x, Windows NT comes with a built-in Task Manager. (Task Manager is discussed in more detail later.) You can enter the Task Manager by selecting the Task Manager radio button.
Cancel: The last option is the Cancel radio button. If Cancel is selected, you are directed back to the Windows NT Desktop.
It is important to note that the same Windows Security and Information display can be accessed in Windows 2000 Professional and Windows NT Server by following the same procedures. The information and options available are identical.
LSA, SID, and ACL
Security access to resources and the entire security sign-on process that takes place when a user logs on to Windows NT is very complicated and beyond the scope of this book. However, a basic explanation of the process is in order.
When a user logs on to Windows NT Workstation, the Local Security Authority (LSA) generates what is called a Security Access Token (SAT). This SAT is assigned a SID (Security ID for the user). The unique user SID contains access rights and privileges that have been assigned to the user’s ID that was created in User Manager or User Manager for Domains (explained in the next section). Windows NT maintains an Access Control List (ACL) for all objects on the Windows NT domain. An object can be a file, a folder, or a printer share, just to name a few. In order for a user to be granted access to an object on the domain, the user’s SAT must be accepted by the ACL. It is improbable that the A+ Operating System Technologies exam will address detailed questions on this subject.
User Profiles and System Policies
A Windows NT local user profile is created when a user first logs on to a Windows NT system. The local user profile is a configuration of the environmental settings and preferences that have been established by the user. In simple terms, a user profile is a combination of Desktop configuration settings the user sees every time he or she logs on. An administrator may implement a roaming user profile for an individual if he or she wishes to use the particular configuration settings assigned to the user at any other computer.
With a roaming user profile, the user’s profile information is stored on a server computer and is presented to the user wherever he or she logs on to the network.
Windows NT has a useful tool for controlling user environments, called the System Policy Editor. With the System Policy Editor tool, an administrator can configure system policies for computers, users, or groups of users. For example, let’s say you wanted all users who signed on to the network as the user ID GUEST to be restricted from changing the screen saver and wallpaper, and editing the Registry. You can use the built-in settings within System Policy Editor to create a policy for the user ID GUEST and apply the restrictions above. You would then need to copy the file NTCONFIG.POL (which is the policy you have saved in System Policy Editor) to the NETLOGON share on the authentication server. When the user GUEST logs on to the network, the policy takes effect.
Profiles and system policies are basically tools used by administrators to control a Windows NT network.
Dial-Up Networking
Dial-up networking allows you to connect to remote networks using a modem or ISDN connection from within Windows NT. If you did not choose the Remote Access to the Network option during the Windows NT installation process, dial-up networking is not installed on your system. If this is the case, you can add dial-up networking by accessing the Network applet located in the Control Panel, select the Services tab, and click the Add radio button. A list of network services opens. Choose Remote Access Service, and click OK. Remote Access Service must be installed to utilize dial-up networking. You will be asked for the location of the I386 folder, which contains Windows NT installation .CAB files. Insert the Windows NT installation CD-ROM if you have not copied the I386 directory to the C:\ drive (which, by the way, is common practice among NT administrators; this avoids the need to use the installation CD-ROM to install services and drivers). Select Continue, and the Remote Access Service will attempt to find a modem connected to your system. Simply follow the instructions for the modem identification and associated COM port, and reboot the system when prompted. This process also installs a network dial-up adapter, which can be seen in the Network applet of the Control Panel once you have rebooted.
After you have rebooted your system, navigate to My Computer > Dial-Up Networking. You will be required to set up a phone book entry and configure the proper protocols and authentication methods used to communicate with the Dial-up Server. From here, it’s as simple as clicking the phone book entry you have created to access a server remotely.
If you are using dial-up networking in Windows 9x or Windows NT, and cannot connect to a dial-up server—or an ISP, for that matter—you should first try to establish a new connection within dial-up networking. For Windows 9x, select the New Modem option from the Dial-Up Networking Connection Properties. For Windows NT, attempt to create and configure a new phone book entry from within the Dial-Up Networking applet in My Computer.
| Note | In order to establish a dial-up connection with the Internet, you must have TCP/IP and a network dial-up adapter. |
EAN: 2147483647
Pages: 390