WIRELESS CONNECTIVITY
All those messy, dangling computer wires and connectors will soon be a thing of the past. Wireless technology has become very popular and affordable. In fact, you can set up a small wireless network at home for about $400. All you really need to set up a wireless network is a couple of transmitters, receivers, and a pair of wireless NICs. The operating system configuration for a wireless network is another story in itself.
There are two main forms of wireless technologies in use for connecting computers together: Radio Frequency (RF) and Infrared (IR).
Radio Frequency (RF)
Many computer peripheral devices today utilize RF technology. With RF, a wireless mouse, keyboard, or modem can communicate with a host system as long as the distance between the peripheral and host does not exceed a specified distance. RF devices use transmitters, receivers, or transceivers (or a combination of these devices) to communicate back and forth. A typical RF mouse or keyboard transmits data through a built-in transmitter to a waiting receiver, which is attached to a system unit through a PS/2 or serial connection. RF devices are designed to meet the IEEE 802.11 standards that apply to wireless networking.
Infrared (IR)
Infrared transmission is a wireless form of transmission that also uses a transmitter and receiver. Instead of sending information with radio signals, however, infrared uses a beam of light that is not visible to the human eye to transmit data between two devices. Line-of-sight is a very popular type of infrared technology used to connect wireless devices, such as a mouse or keyboard, to a host system. The Infrared Data Association (IRDA) is the organization that is responsible for infrared transmission standards. Infrared technology has become very popular with laptop computers, PDAs, and digital cameras. With the infrared IRDA Standard 1.1, the maximum transmission rate is 4Mbps with a data size of 2048 bytes.
Some of the common uses available for infrared transmission are these:
-
Messages can be sent between PDAs or between laptop computers.
-
Faxes can be sent from any device utilizing IR technology.
-
Pictures or images from a digital camera can be sent to a desktop or laptop computer.
-
Letters or documents can be sent from a desktop or laptop computer to a printer.
The majority of infrared transmissions occur between two computers or a single computer and an infrared-enabled device, such as a printer or PDA. The sending host or device uses an infrared transmitter or ‘emitter,’ which sends pulses of infrared light to the receiving host or device that accepts the pulses with an infrared receiver. In order for the transmission of this signal to occur, there must be a direct line of sight between communicating systems or devices, as well as a protocol and a computer name resolution.
Infrared was originally designed for point-to-point bidirectional transmissions via an RS232C serial port. Today, most modern systems come equipped with an IRDA-standard port that can interface directly with an IR transmitter/receiver. IR connections can also be made through the use of a parallel or USB port.
In conclusion to our infrared discussion, keep in mind that IR is sometimes called the “one-to-one” technology. You can only send to or receive from one device at a time. In other words, while you are transmitting or receiving information between your desktop computer and your PDA, you cannot transmit or receive data from your laptop and at the same time use infrared.
Popular operating systems such as Microsoft Windows 95, 98, NT, 2000, XP and Windows Me offer support for adding IR devices. Early versions of Windows 95 required a special IRDA Software Patch that could be downloaded from Microsoft.com to enable IR support. In order for your system to use IR, support must be enabled in your system’s BIOS.
Wireless Networking And Security
Wireless transmission is defined as the sending of signals over electromagnetic ‘radio’ waves. Wireless networks have become very widespread. In some cases, wireless networks have replaced the need for tradition wiring. But in larger networks, wireless technology is typically used as an extension or addition to a wired network. Wireless networks offer the ability for computing in places that would be otherwise hard to reach with a wire or cable. The use of wireless technology has been widely accepted by the military, hospitals, businesses, cell-phone companies, Global Positioning System (GPS) customers, museums, and home users alike. The IEEE has developed standards for wireless technologies. These standards are a set of rules that provide a sort of instruction map of guidelines for technology developers to follow when creating new technologies or adding to existing technologies. The IEEE standards that apply to wireless networking are: 802.11, 802.11a, 802.11b, and 802.11g. In its simplest of forms, a wireless network, or WLAN (Wireless Local Area Network), is displayed connected to a ‘wired’ LAN in Figure 21.11. Basic wirelesses networks typically have a wireless client, an authentication server, or ‘host,’ and an access point.
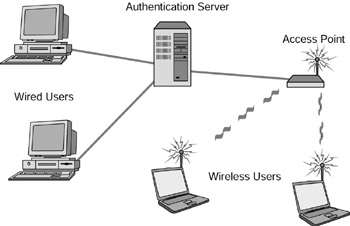
Figure 21.11: A basic wireless network.
The need to secure the use of wireless technologies and remote wireless user access has become paramount. Not too long ago, wireless connections were thought to be somewhat secure. Recently, these thoughts have changes, based on security holes found in the technology. Next we will discuss 802.1X standards and basic wireless protocols.
802.1X
The use and support of wireless networking, equipment, security, and protocols are on the rise. Although the fine details regarding 802.1X will most likely not be addressed on the exam, the following information will give you a very good understanding of wireless concepts.
802.1X is an IEEE standard for wireless connectivity that uses port-based access control. It falls under the influence of the initial IEEE standard 802.11 for WLANs. The IEEE and the standards that apply to networking technologies in general are explained in Chapter 22. In this chapter, we will discuss all of the IEEE 802.11 standards for wireless networking. The 802.1X standard is designed to provide a better framework that supports improved security for users of wireless networks by the implementation of centralized authentication. Standard 802.1X uses the Extensible Authentication Protocol (EAP), which enables the technology to work with wireless, Ethernet, and Token Ring networks.
With 802.1X authentication, a wireless client who wishes to connect to and be authenticated on the network is called a supplicant. The supplicant must first request access from an access point, which is also known as an authenticator. If the access point detects the request for access from the supplicant, the access point will enable the supplicant’s port and only let 802.1X traffic be transmitted. This allows the client to transmit a start-up message, known as an EAP start message; the supplicant’s identity and credentials are then provided to the access point. The access point then transmits the information to an authentication server, which is typically a server that runs RADIUS (Remote Authentication Dial-In User Service). The authentication server can use various algorithms to eventually allow the user to be authenticated. Once the server authenticates the validity of the user, it will transmit either an acceptance or rejection acknowledgement of the client’s request to the access point. If the access point receives positive feedback from the RADIUS authentication server, the access point will enable or activate the supplicant’s port for normal network traffic.
In simple terms, here is how 802.1X wireless authentication works. See Figure 21.12 for a visual regarding 802.1X authentication. To best understand this process, match the following descriptions with their corresponding numeric values in Figure 21.12:
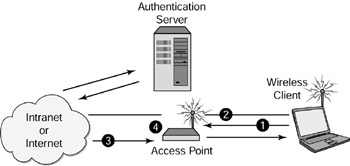
Figure 21.12: 802.1X wireless authentication.
-
A Start message is sent from the remote Client to the Access Point, and the Access Point asks the Client for identification.
-
The Client sends its identity to the access point. The Access Point then transmits or forwards the Client’s identity to an authentication server.
-
The Authentication Server transmits an accept or reject message to the Access Point.
-
If the Access Point receives an accept message from the Authentication Server, the Client’s port activates, and the Client is allowed to communicate with the Server.
The 802.1X standard is fairly new and it is not likely that CompTIA will target it extensively on the exam. However, you should be aware of the basics concepts. Microsoft does a great job explaining this technology. If you are interested in learning more about 802.1X you may find the following site very informative: http://www.microsoft.com/windowsxp/pro/techinfo/planning/wirelesslan/solutions.asp.
WAP
WAP (Wireless Application Protocol) is a wireless standard that applies to wireless communication protocols and devices. There are several standards that are used by various wireless device service manufacturers. WAP is positioned to allow interoperability between them.
WAP has its own built-in security. It uses WTLS (Wireless Transport Layer Security), which uses secure certificates and a client/server verification/authentication process.
WEP
WEP (Wired Equivalent Privacy) is wireless security protocol specified under the IEEE 802.11b. WEP is intended to provide a WLAN with a similar security level as the protection that can be found in traditional LANs. WEP attempts to secure the obvious security hole that exists between a wireless client and an access point by encrypting the data that is transmitted. Once the data has been safely transmitted, it is thought that conventional network security measures (e.g., VLANS, antivirus, tunneling, and authentication solutions) can be implemented for security purposes.
| Note | The exam is likely to ask you very basic questions relating to wireless networking; for example, What technology does WEP have to do with? Or, what does WAP do? For this exam, it is sufficient to know that they wireless standards that apply to wireless communication protocols and devices. |
Wireless Access Points
Wireless access points are used in WLANs as central points of communication between wireless users. They are sometimes referred to as transceivers because they have the ability to transmit and receive RF signals. They are the ‘hub’ of wireless networks. Access points can also serve as a connection point between wireless users and a wired LAN, as depicted in Figure 21.11.
Access points allow wireless users to roam in a generally predefined area called a “cell.” This cell is actually the area in which the RF signals can be successfully transmitted from the access point to the roaming, or ‘wireless,’ user and back again. In a small business environment, this area is typically around 100 feet, depending upon many outside physical and electrical conditions. In many businesses today, it is very common to find multiple access points strategically positioned around the business environment. When a mobile user moves outside the transmission area of one particular cell, they enter another cell area without losing the RF signal to the entire WLAN. Much larger cell areas are used for broadcasting such things as cellular phone ‘wireless’ radio waves. These cell areas can be as small as a city block or carry radio waves several hundred miles.
Wireless Antennas
In wireless networking, an antenna is used to propagate, or ‘radiate’ RF signals to wireless users and access points in a wireless network. There are various antennas for wireless networking, and each has its own physical characteristics and specialized features. The two main types of wireless antennas that we need to be concerned about are:
Directional antenna: A directional antenna has the ability to direct an RF signal farther than an omnidirectional antenna. It focuses its power in a single direction, which minimizes RF interference. Directional antennas are well suited for long-distance transmissions and work well for transmitting RF signals between buildings or other locations where a direct line of site can be established.
Omnidirectional antenna: An omnidirectional antenna transmits its signals in many different directions, usually in a 360 radius. They are ideal for home, classroom, or small business. A good 802.11b omnidirectional antenna will evenly blanket your WLAN. Most omnidirectional antennas are either snap-on or dipole antennas. A snap-on is typically connected to a radio card located within a mobile or portable access point. A dipole antenna, the simplest form of antenna, is a mobile antenna that connects to a radio card with a relatively short cable.
Ad-Hoc
If a wireless network is set up using a peer-to-peer mode where wireless stations communicate directly with each other without the use of an access point, the wireless network is said to be using ad-hoc mode. An ad-hoc mode is usually implemented for temporary wireless transmission purposes.
Site Surveys
Before you install a wireless network solution into an existing building or between existing buildings (building to building), you should first have a professional site survey conducted by certified RF engineers. These engineers can properly recommend and assist you with an integration plan, as well as keep you in line with federal, state, and local regulations as they apply to wireless networks.
With traditional network installations, it is much easier to plan out a network topology and possibly foresee obstacles that will need to be addressed. However, with wireless networks that implement the use of radio transmission techniques, it is very difficult to plan for and determine how a network will react to the surrounding conditions. Obstacles such as asbestos-lined walls, trees, and other physical impediments can severely impact the effectiveness of wireless communication. The interference with other RF bands in busy airways can severely hamper your performance and ability to communicate between access points. Certified site survey technicians can detect potential interference between RF bands with a tool called a spectrum analyzer.
A good site survey should provide you with the most suitable wireless equipment options to integrate with your current topology and applications. It should also provide you with a wireless standard that is in line with your required transmission speeds and, ultimately, your budget.
| Note | If you are interested in getting a wireless network solution, the first step is to have a site survey performed. |
EAN: 2147483647
Pages: 390
- Chapter II Information Search on the Internet: A Causal Model
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability