Transparent Bridging
As discussed in Chapter 2, networks are segmented to provide more bandwidth per user. Bridges provide more user bandwidth by reducing the number of devices contending for the segment bandwidth. But bridges also provide additional bandwidth by controlling data flow in a network. Bridges forward traffic only to the interface(s) that need to receive the traffic. In the case of known unicast traffic, bridges forward the traffic to a single port rather than to all ports. Why consume bandwidth on a segment where the intended destination does not exist?
Transparent bridging, defined in IEEE 802.1d documents, describes five bridging processes for determining what to do with a frame. The processes are as follows:
Learning
Flooding
Filtering
Forwarding
Aging
Figure 3-1 illustrates the five processes involved in transparent bridging.
Figure 3-1. Transparent Bridge Flow Chart
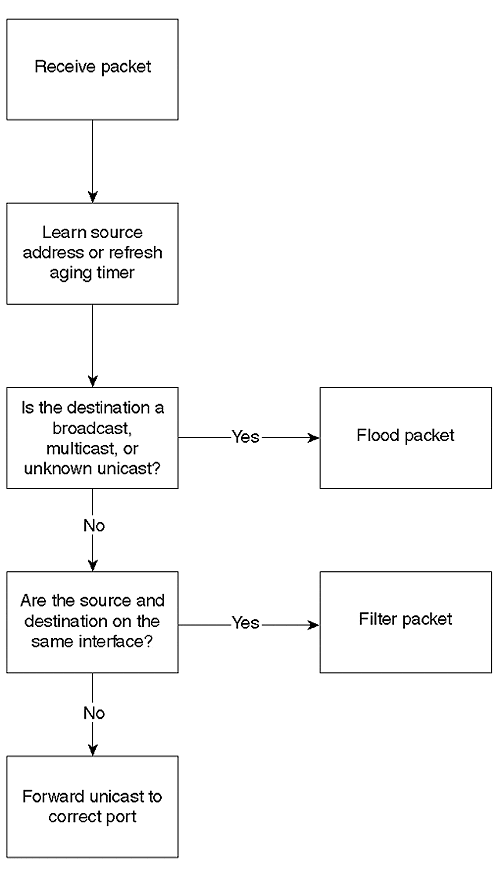
When a frame enters the transparent bridge, the bridge adds the source Ethernet MAC address (SA) and source port to its bridging table. If the source address already exists in the table, the bridge updates the aging timer. The bridge examines the destination MAC address (DA). If the DA is a broadcast, multicast, or unknown unicast, the bridge floods the frame out all bridge ports in the Spanning Tree forwarding state, except for the source port. If the destination address and source address are on the same interface, the bridge discards (filters) the frame. Otherwise, the bridge forwards the frame out the interface where the destination is known in its bridging table.
The sections that follow address in greater detail each of the five transparent bridging processes.
Learning
Each bridge has a table that records all of the workstations that the bridge knows about on every interface. Specifically, the bridge records the source MAC address and the source port in the table whenever the bridge sees a frame from a device. This is the bridge learningprocess. Bridges learn only unicast source addresses. A station never generates a frame with a broadcast or multicast source address. Bridges learn source MAC addresses in order to intelligently send data to appropriate destination segments. When the bridge receives a frame, it references the table to determine on what port the destination MAC address exists. The bridge uses the information in the table to either filter the traffic (if the source and destination are on the same interface) or to send the frame out of the appropriate interface(s).
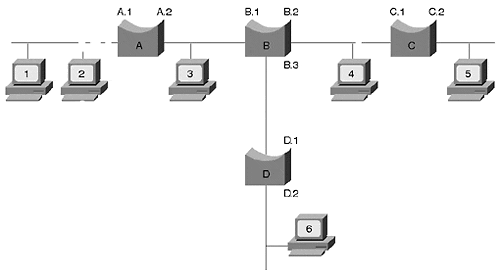
But when a bridge is first turned on, the table contains no entries. Assume that the bridges in Figure 3-2 were all recently powered "ON," and no station had yet transmitted. Therefore, the tables in all four bridges are empty. Now assume that Station 1 transmits a unicast frame to Station 2. All the stations on that segment, including the bridge, receive the frame because of the shared media nature of the segment. Bridge A learns that Station 1 exists off of port A.1 by looking at the source address in the data link frame header. Bridge A enters the source MAC address and bridge port in the table.
Figure 3-2. Sample Bridged Network
Flooding
Continuing with Figure 3-2, when Station 1 transmits, Bridge A also looks at the destination address in the data link header to see if it has an entry in the table. At this point, Bridge A only knows about Station 1. When a bridge receives a unicast frame (a frame targeting a single destination), no table entry exists for the DA, the bridge receives an unknown unicast frame.The bridging rules state that a bridge must send an unknown unicast frame out all forwarding interfaces except for the source interface. This is known as flooding. Therefore, Bridge A floods the frame out all interfaces, even though Stations 1 and 2 are on the same interface. Bridge B receives the frame and goes through the same process as Bridge A of learning and flooding. Bridge B floods the frame to Bridges C and D, and they learn and flood. Now the bridging tables look like Table 3-1. The bridges do not know about Station 2 because it did not yet transmit.
Table 3-1. Bridging Table after Flooding
Bridge Port
A.1
A.2
B.1
B.2
B.3
C.1
C.2
D.1
MAC Address
1
1
1
1
Still considering Figure 3-2, all the bridges in the network have an entry for Station 1 associated with an interface, pointing toward Station 1. The bridge tables indicate the relative location of a station to the port. Examining Bridge C's table, an entry for Station 1 is associated with port C.1. This does not mean Station 1 directly attaches to C.1. It merely reflects that Bridge C heard from Station 1 on this port.
In addition to flooding unknown unicast frames, legacy bridges flood two other frame types: broadcast and multicast. Many multimedia network applications generate broadcast or multicast frames that propagate throughout a bridged network (broadcast domain). As the number of participants in multimedia services increases, more broadcast/multicast frames consume network bandwidth. Chapter 13, "Multicast and Broadcast Services," discusses ways of controlling multicast and broadcast traffic flows in a Catalyst-based network.
Filtering
What happens when Station 2 in Figure 3-2 responds to Station 1? All stations on the segment off port A.1, including Bridge A, receive the frame. Bridge A learns about the presence of Station 2 and adds its MAC address to the bridge table along with the port identifier (A.1). Bridge A also looks at the destination MAC address to determine where to send the frame. Bridge A knows Station 1 and Station 2 exist on the same port. It concludes that it does not need to send the frame anywhere. Therefore, Bridge A filters the frame. Filtering occurs when the source and destination reside on the same interface. Bridge A could send the frame out other interfaces, but because this wastes bandwidth on the other segments, the bridging algorithm specifies to discard the frame. Note that only Bridge A knows about the existence of Station 2 because no frame from this station ever crossed the bridge.
Forwarding
If in Figure 3-2, Station 2 sends a frame to Station 6, the bridges flood the frame because no entry exists for Station 6. All the bridges learn Station 2's MAC address and relative location. When Station 6 responds to Station 2, Bridge D examines its bridging table and sees that to reach Station 2, it must forward the frame out interface D.1. A bridge forwards a frame when the destination address is a known unicast address (it has an entry in the bridging table) and the source and destination are on different interfaces. The frame reaches Bridge B, which forwards it out interface B.1. Bridge A receives the frame and forwards it out A.1. Only Bridges A, B, and D learn about Station 6. Table 3-2 shows the current bridge tables.
Table 3-2. Bridging Table after Forwarding
Bridge Port
A.1
A.2
B.1
B.2
B.3
C.1
C.2
D.1
D.2
MAC Address
1
1
1
1
2
2*
2*
2*
6
6
6
*. B.1, C.1, and D.1 did not learn about Station 2 until Station 2 transmitted to Station 6.
Aging
When a bridge learns a source address, it time stamps the entry. Every time the bridge sees a frame from that source, the bridge updates the timestamp. If the bridge does not hear from that source before an aging timerexpires, the bridge removes the entry from the table. The network administrator can modify the aging timer from the default of five minutes.
Why remove an entry? Bridges have a finite amount of memory, limiting the number of addresses it can remember in its bridging tables. For example, higher end bridges can remember upwards of 16,000 addresses, while some of the lower-end units may remember as few as 4,096. But what happens if all 16,000 spaces are full in a bridge, but there are 16,001 devices? The bridge floods all frames from station 16,001 until an opening in the bridge table allows the bridge to learn about the station. Entries become available whenever the aging timer expires for an address. The aging timer helps to limit flooding by remembering the most active stations in the network. If you have fewer devices than the bridge table size, you could increase the aging timer. This causes the bridge to remember the station longer and reduces flooding.
Bridges also use aging to accommodate station moves. In Table 3-2, the bridges know the location of Stations 1, 2, and 6. If you move Station 6 to another location, devices may not be able to reach Station 6. For example, if Station 6 relocates to C.2 and Station 1 transmits to Station 6, the frame never reaches Station 6. Bridge A forwards the frame to Bridge B, but Bridge B still thinks Station 6 is located on port B.3. Aging allows the bridges to "forget" Station 6's entry. After Bridge B ages the Station 6 entry, Bridge B floods the frames destined to Station 6 until Bridge B learns the new location. On the other hand, if Station 6 initiates the transmission to Station 1, then the bridges immediately learn the new location of Station 6. If you set the aging timer to a high value, this may cause reachability issues in stations within the network before the timer expires.
The Catalyst screen capture in Example 3-1 shows a bridge table example. This Catalyst knows about nine devices (see bolded line) on nine interfaces. Each Catalyst learns about each device on one and only one interface.
Example 3-1 Catalyst 5000 Bridging Table
Console> (enable) show cam dynamic VLAN Dest MAC/Route Des Destination Ports or VCs ---- ------------------ ---------------------------------------------------- 2 00-90-ab-16-60-20 3/4 1 00-90-ab-16-b0-20 3/10 2 00-90-ab-16-4c-20 3/2 1 00-60-97-8f-4f-86 3/23 1 00-10-07-3b-5b-00 3/17 1 00-90-ab-16-50-20 3/91 3 00-90-ab-16-54-20 3/1 1 00-90-92-bf-74-00 3/18 1 00-90-ab-15-d0-10 3/3 Total Matching CAM Entries Displayed = 9 Console> (enable)
The bridge tables discussed so far contain two columns: the MAC address and the relative port location. These are seen in columns two and three in Example 3-1, respectively. But this table has an additional column. The first column indicates the VLAN to which the MAC address belongs. A MAC address belongs to only one VLAN at a time. Chapter 5, "VLANs," describes VLANs and why this is so.
EAN: N/A
Pages: 223