Implementing Authentication
| In this book, you use ASDM to implement authentication on the ASA/PIX Security Appliance. The following list of authentication tasks are performed:
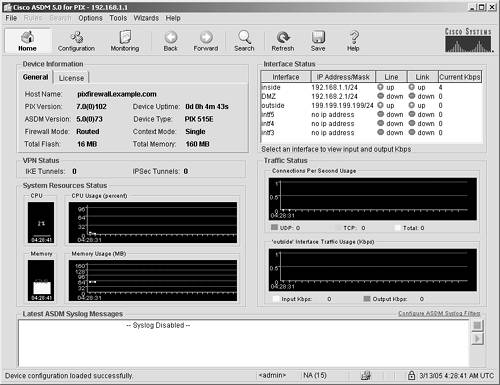
Securing Access to the Security ApplianceNow that you have a basic understanding of both authentication and its importance, you can start ASDM and follow these procedures to deploy authentication. This step-by-step procedure leverages off of the configuration work that you have already done on your ASA/PIX Security Appliance in Chapter 5, "Deploying Secure Internet Connectivity," and Chapter 6, "Deploying Web and Mail Services." Start ASDMTo connect to the ASA/PIX Security Appliance using ASDM and then to authenticate access to your security appliance, follow these steps:
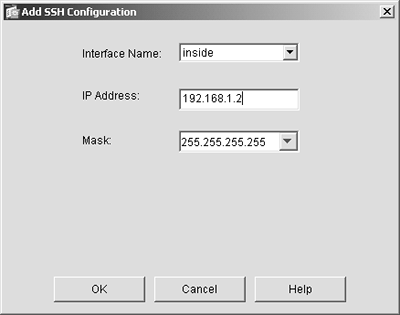
Securing Telnet AccessDo not use Telnet to administer your security appliance. As stated several times in this book, Telnet is a clear text protocol. Therefore, it sends usernames and passwords on the network in clear text. The same occurs if you use Telnet for Line mode configuration of your security appliance, in that the configuration of the security appliance would be passed on the network in clear text. In such a case, hackers can easily intercept the information and thereby gain unlimited access to your security appliance. CAUTION From a security best practices perspective, do not use Telnet to administer your security appliance. You cannot secure the Telnet protocol unless it is used in conjunction with virtual private networks (VPNs), which is beyond the scope of this book. The "SAFE Blueprint" white paper at http://www.cisco.com/go/safe has some recommendations for using VPN as a means to protect clear text management protocols. Securing SSH AccessSecure Shell (SSH) is a utility that you can safely use to manage your security appliance. It is a Line mode tool; therefore, it is important to be familiar with the native ASA/PIX version 7 command set if you elect to use SSH. If you aren't familiar with the command set, ASDM is the option you would want to use. To set up SSH, just in case you have this requirement in your network deployment, follow these steps:
You should now be able to access the ASA/PIX Security Appliance, using SSH, from 192.168.1.2 with the username and password you created. Securing ASDM/HTTPS AccessThe preferred method of access for the ASA/PIX Security Appliance running version 7 is ASDM. It is both secure and easy to use. In this section, you configure the security appliance to add ASDM users. You have already configured the security appliance to use ASDM, but the steps are repeated here again briefly for emphasis:
Monitoring Security Appliance AccessMonitoring system access is a critical task for any network administrator. The ASA/PIX Security Appliance offers several options for keeping track of who is logged on to your system. If you navigate to Monitoring > Features > Administration, you will see a list of all the ASA/PIX access methods, including the following:
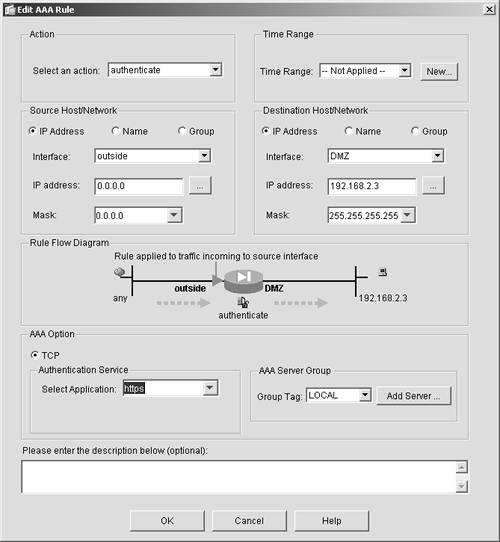
By just clicking any of these categories, you can immediately see who is connected to your system and the method by which they established their connection. Syslog can also be an excellent tool to see who has connected to your system. However, you would need to write a script or utility to search the syslog file for keywords that indicate that someone has connected or disconnected from your system. AAA Authentication AccessBy using the AAA features of the ASA/PIX Security Appliance, you can limit the hours that users can log on to your ASA/PIX. AAA also has utilities that enable an administrator to see what time a user logged on or off and, in some cases, what the user did while on the system. Adding an AAA server is an additional expense, but considering the additional features and reporting, many customers have little problem justifying the purchase. You can find out more about AAA on the Cisco website at http://www.cisco.com/go/acs. Authentication for Inbound and Outbound ServicesAnother compelling feature of the ASA/PIX Security Appliance is the ability to authenticate users before you allow them to access certain inbound and outbound services. For example, if you have a website on your demilitarized zone (DMZ) that is to be accessed only by a few choice users, the ASA/PIX Security Appliance can prompt anyone trying to access that site for a username and password before allowing access. The following are the services that can be authenticated:
To deploy this authentication, you must complete the following steps. In this example, HTTPS is used and users are authenticated before they can access your web server at 199.199.199.202:
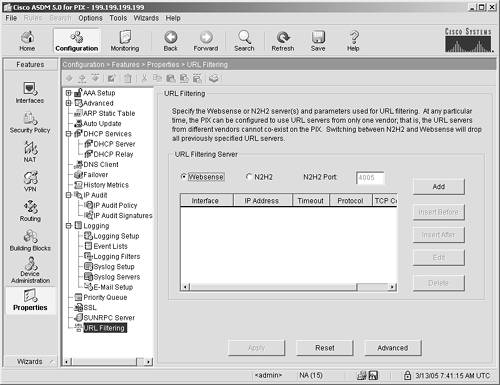
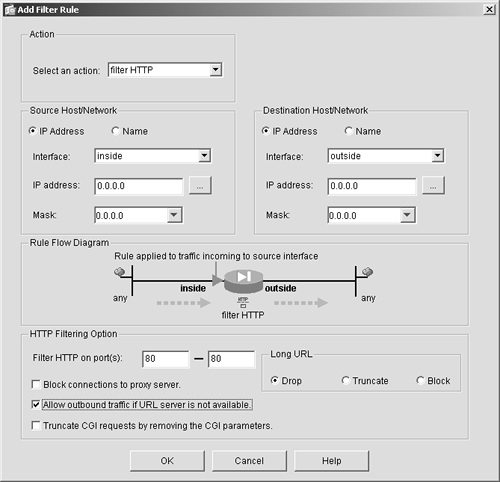
You can authenticate outbound users in the same manner, except, when you create the AAA rule, choose Inside as the source and Outside as the destination. Outbound URL Filtering for Public ServicesAs discussed in Chapter 4, "Exploring the Adaptive Security Device Manager," in the ASDM overview, outbound URL authentication can be a powerful security and network bandwidth-management tool. You can block access to certain websites or classes of websites and thereby limit access to certain sites such as porn, free download, and file-sharing sites, which in turn will help reduce the following threats to your hosts:
The ASA/PIX version 7 operating system supports URL filtering from several different vendors. This feature enables you to stop access to several different classes of websites that might be responsible for the spread of spyware, Trojans, web viruses, and data-mining cookies. Examples of classes of websites that might be blocked by this software include the following:
NOTE The classes of sites listed here are not considered bad sites, per se. But they represent some of the classes of sites that could be blocked using URL filtering. Unfortunately, many web servers that fit in these classes have chosen to do things such as download spyware, data miners, and Trojans. The result of this activity has led to client computers experiencing excessive pop-up ads, significantly slower CPUs, and usage of unnecessary network bandwidth. URL blocking servers enable you to block classes of URLs that you deem dangerous or inappropriate. If you elect to block a class called "hacker sites," the software automatically blocks several hundred URLs that are known hacker sites. You can also use URL blocking to improve bandwidth usages in some businesses (especially if users previously had been downloading large files such as MP3s, WAVs, MPEGs, or streaming audio). You can deploy URL blocking to reduce these traffic classes. CAUTION A few states in the United States consider URL blocking illegal. Check with a legal representative before deploying this feature.
VPN AuthenticationVPN authentication is discussed in Chapter 11, "Deploying VPNs." |
EAN: 2147483647
Pages: 120