Monitoring Directory Services
| The most obvious reason to monitor the health of your directory service is to detect a failure as soon as it occurs so it can be fixed quickly. Another reason is to make sure the directory service is running efficiently . Failures can be detected and reported by running agents on the directory server that report back to some central management console. These include:
Tools to analyze the behavior of your directory service include:
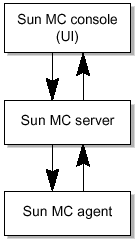
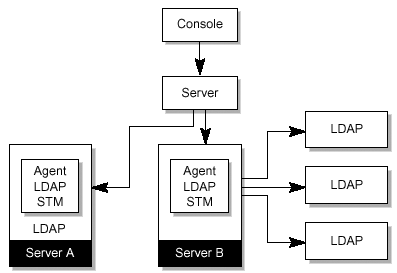
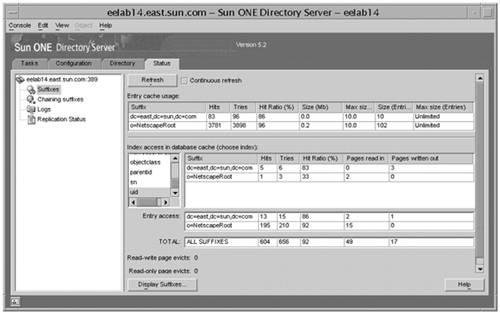
This section provides an overview of these tools. Sun Management Center 3.0 SoftwareThe Sun Management Center (SunMC) software provides a framework to simplify management of Sun systems. It is based on a three- tier architecture, as shown in FIGURE 7-1. Figure 7-1. SunMC Components In this architecture, agents report back to a server that interfaces to the SunMC console. The console displays status information and provides an operator interface. The agent can reside on the system running the service or on a remote system. To monitor an LDAP service you need to install an additional piece of software (SunMC add-on) called the Service Availability Manager (SAM). The SAM provides Synthetic Transaction Modules (STMs), that mimic clients accessing the service. The STM for LDAP is configured with an LDAP server IP address, port number, and search base. A predefined search is periodically performed against the configured directory servers. The agent running the LDAP STM reports back to the SunMC server if the search exceeds a pre-defined threshold. FIGURE 7-2 shows how this can be deployed. Figure 7-2. SunMC With the SAM Add-on In this diagram, System A is running the LDAP STM on the same server as the LDAP server. System B is running the LDAP STM, but is not running an LDAP server. Instead, it is monitoring three other LDAP servers. Sun ONE Directory Server 5.2 Software Performance CountersUseful data pertaining to cache hits can be obtained from the Status Display under Suffixes. FIGURE 7-3 shows output from a directory server with two suffixes. Figure 7-3. Sun ONE Directory Console Showing the Directory Server Status Screen Unlike the previous version, you can choose which attribute you want to monitor. Using logconv.plThe Directory Server Resource Kit software includes a Perl script called logconv.pl for examination of directory server access logs. This is a very helpful tool because log files can become quite large making them difficult to interpret without automated tools. The logconv.pl program provides the summarized information. It is a static tool that uses the directory server access log for input. The logconv.pl command syntax: ./logconv.pl [-h] [-d rootDN ] [-s size_limit ] [-X ipaddress ] [-E error_code ] [-N] [-v] [-V] [-efcibaltnxgju] [ access_log_file ] Using the following logconv.pl options, the following data can be extracted: e Error Code stats f Failed Login Stats c Connection Code Stats i Client Stats b Bind Stats a Search Base Stats l Search Filter Stats t Etime Stats n Nentries Stats x Extended Operations r Most Requested Attribute Stats g Abandoned Operation Stats j Recommendations u Unindexed Search Stats logconv.pl example: # ./logconv.pl -V /files/public/access* iPlanet Access Log Analyzer 4.31 Initializing Variables... Processing 1 Access Log(s)... /files/public/access.20021218-091516 (Total Lines: 9964) Restarts: 0 Total Connections: 1184 Total Operations: 3206 Total Results: 3206 Overall Performance: 100.0% Searches: 1472 Modifications: 0 Adds: 0 Deletes: 0 Mod RDNs: 0 5.x Stats Persistent Searches: 0 Internal Operations: 0 Entry Operations: 0 Extended Operations: 576 Abandoned Requests: 0 Smart Referrals Received: 0 VLV Operations: 0 VLV Unindexed Searches: 0 SORT Operations: 0 SSL Connections: 0 Entire Search Base Queries: 0 Unindexed Searches: 0 FDs Taken: 1184 FDs Returned: 1184 Highest FD Taken: 69 Broken Pipes: 0 Connections Reset By Peer: 0 Resource Unavailable: 0 Binds: 1158 Unbinds: 1184 LDAP v2 Binds: 0 LDAP v3 Binds: 1158 Expired Password Logins: 0 SSL Client Binds: 0 Failed SSL Client Binds: 0 SASL Binds: 0 Directory Manager Binds: 0 Anonymous Binds: 0 Other Binds: 1158 ----- Errors ----- err=0 3206 Successful Operations ----- Total Connection Codes ----- U1 1184 Cleanly Closed Connections ----- Top 20 Clients ----- Number of Clients: 2 896 129.148.181.216 896 - U1 Cleanly Closed Connections 288 129.148.181.130 288 - U1 Cleanly Closed Connections ----- Top 20 Bind DN's ----- Number of Unique Bind DN's: 2 870 cn=proxyagent,ou=profile,dc=example,dc=com 288 cn=replication manager, cn=config ----- Top 20 Search Bases ----- Number of Unique Search Bases: 6 765 ou=people,dc=example,dc=com 314 root dse 288 cn=schema 101 ou=hosts,dc=example,dc=com 2 ou=profile,dc=example,dc=com 2 dc=example,dc=com ----- Top 20 Search Filters ----- Number of Unique Search Filters: 11 602 (objectclass=*) 153 (&(objectclass=posixaccount)(uid=user2)) 153 (&(objectclass=posixaccount)(uid=user12345678)) 153 (&(objectclass=posixaccount)(uidnumber=123456789)) 153 (&(objectclass=posixaccount)(uidnumber=101)) 153 (&(objectclass=posixaccount)(uid=user123456789)) 33 (&(objectclass=iphost)(iphostnumber= 129.148.181.216)) 33 (&(objectclass=iphost)(cn=eelab14)) 33 (&(objectclass=iphost)(iphostnumber= 129.148.181.130)) 4 (nisdomain=*) 2 (&((objectclass=solarisnamingprofile)(objectclass= duaconfigprofile))(cn=default)) ----- Top 20 Most Requested Attributes ----- 864 cn 765 uidNumber 765 homeDirectory 765 description 765 gecos 765 loginShell 765 uid 765 gidNumber 314 supportedControl 288 supportedExtension 288 nsSchemaCSN 99 ipHostNumber 26 supportedSASLMechanisms 4 nisDomain 2 All Attributes |
EAN: N/A
Pages: 87